HackTheBox: Dynstr Machine Walkthrough – Medium Difficulty
Medium Machine BurpSuite, Challenges, DNS, dyn, gobuster, HackTheBox, Linux, nsupdate, Penetration Testing, ssh, SSH keyIn this post, i would like to share walkthrough on Dynstr Machine.
This room is been considered difficulty rated as Medium machine

Information Gathering on Dynstr machine
Once we have started the VPN connection, we can start information gathering on the machine by executing the command nmap -sC -sV <IP Address> -PN


Let’s run gobuster to get a clear enumeration of the machine itself. From the gobsuter result, we notice that there is /nic directory stored over here.
If we continue enumeration on the website, we should be able to be found a file called update
When we access to send the packet to the server, we notice that the Response output for server information such as
server 127.0.0.1
zone no-ip.htb
update. delete beta.no-ip.htb
good 10.10.14.16

Gaining Access on dynstr
Let’s do some research for further knowledge on the internet

Source: Return Codes (RA-API) | Dyn Help Center

Source: Perform Update (RA-API) | Dyn Help Center

Let’s try to enter the code on BurpSuite Community and i didn’t manage to get a reverse shell back connection.

We managed to get the command correct on the burpsuite and send the request to the server

We managed to get the reverse shell connection back to us.
Maintaining Access

Let’s read the update file I have noticed that we need to nsupdate the DNS configuration which requires a key

The screenshot above shows the infra.key with the secret key

We need to update the DNS connection configuration with the command nsupdate -k /etc/bind/infra.key

Let’s retrieve the ssh key on authorized_keys but we cannot login to the machine via the ssh service.

Let’s roam around the server and found some script on /home/bindmgr/supported_case-C62796521.

Inside one of the script, we managed to get ssh id_rsa
Let’s ssh into the machine using that id_rsa
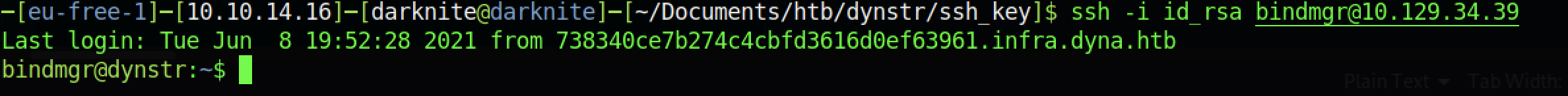
We managed to login to the server via ssh service

We can read the user flag by executing “cat user.txt” command
Escalate to Root Privileges Access

We should be able to get the SUID file if we run the sudo -l command

Let’s read the file at /usr/local/bin/bindmgr.sh and we notice that the bug is related to wildcard injection

The command above will be executed by the attacker to get bash copied to our ssh session

I have been manage to found the bash file have been assigned a SUID binary
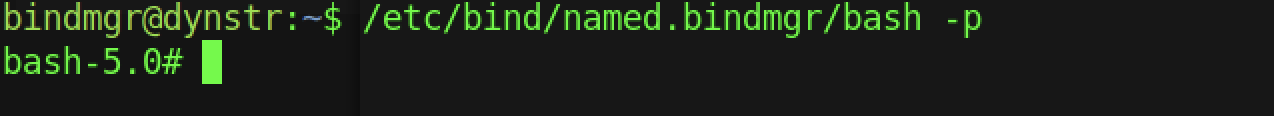
Let’s run the bash -p at /etc/bind/named.bindmgr/bash -p

We are logged as root


We should be able to read the root flag by going to /root/ directory and running “cat root.txt“
-THE END-
Happy Learning Guys!
Extra Information
We can go to /etc/shadow to unlock the write-up


great as always !