In this post, I would like to share a walkthrough of the Health Machine from Hack the Box
This room will be considered a medium machine on Hack the Box

What will you gain from the health machine?
For the user flag, you will need to abuse the SQL Injection via redirect exploit and use SSRF attack to exploit on Gogs which leaks the user table.
As for the root flag, you need to exploit a cron job by generating tasks directly to the database which also can bypass the filtering of the website
Information Gathering on Health Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start the information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN

Let’s access the website interface.

We managed to see the website that show a page that ask us to configure the webhook

Before we enter the information on the form, we can start our nc listener that listens to port 80

The information that we enter will look something as shown above.
Sadly, we didn’t get any response back from the nc listener.

As a result, let’s start our nc listener which is using port 9000
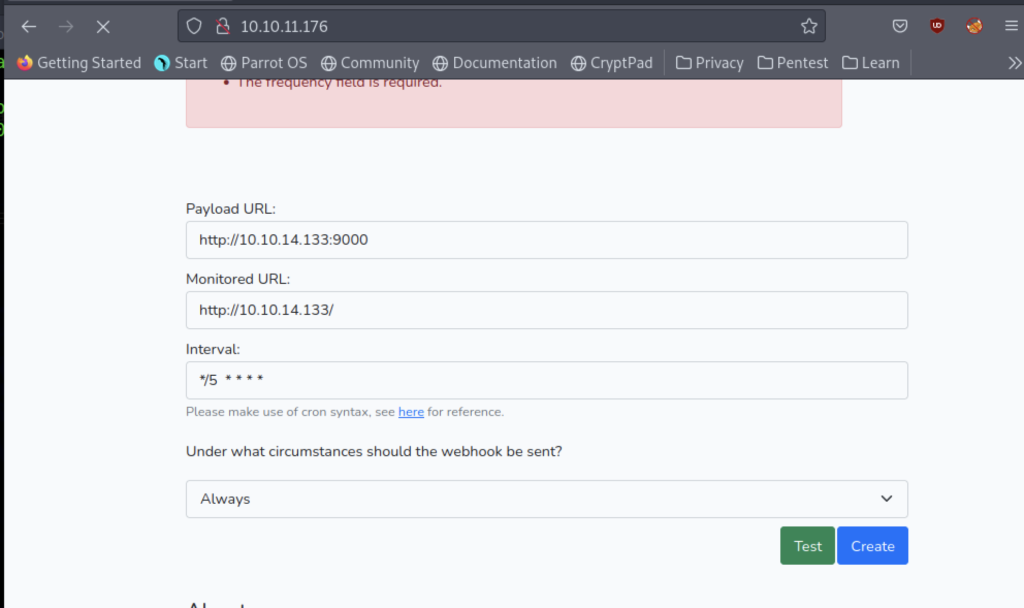
As previously, we enter the information as shown above.

Let’s redirect the website to localhost which uses port 3000

Finally, we managed to obtain some data on the nc listener, and I did notice that the website is using Gogs.
After a while, i do some research and found some valuable information here

As a result, we can redirect the website to use SQL injection (union select method)


At last, we managed some username: Susanne with the password hash

We are required to change the password hash into base64 encoded


Therefore, we can crack the password hash by using hashcat and we got the password as february15

Voila! We have successfully accessed the machine via SSH service

We can read the user flag by typing the ‘cat user.txt‘ command
Escalate to Root Privileges Access

As usual, we can try to find the SUID Binary by typing the “sudo -l” command

However, there’s nothing that looks interesting at the first glance.

When i look deeper into hidden files, i notice there’s one file that stands out for me at least. The file is called .env

Inside the env file, i notice a database username and password have been written on MySQL connection.

We should be creating a new webhook on the website which is the only difference would be the interval as */1 * * * *
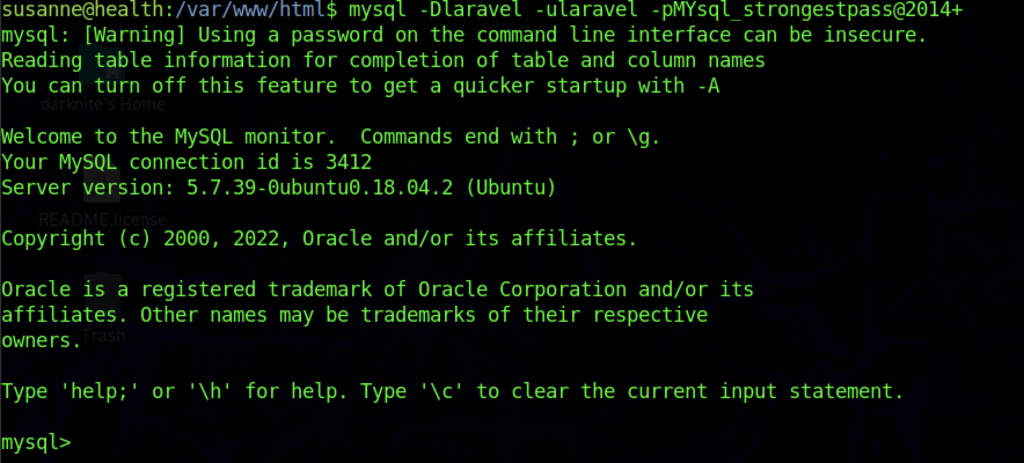
As a result, let’s access MySQL with the credentials that we found earlier.

The screenshot above shows the tasks that have been created.

Let’s try to retrieve the root ssh private key so that we can access it via SSH Service.

At last, we managed to retrieve the SSH private key


Finally, we have successfully accessed the machine as root via SSH service.

We can read the root flag by typing the “cat root.txt” command
Extra Information


No responses yet