In this post, I would like to share a walkthrough of the Moderators Machine from Hack the Box
This room will be considered a Hard machine on Hack The Box

What will you gain from the Moderators machine?
For the user flag, you will need to enumerate the website where we will find an upload page that we are required to bypass the filters to obtain a webshell. We can also use port forwarding using chisel where we will able to access internal WordPress. Inside the WordPress dashboard, we can exploit the WordPress plugin “Brandfolder” to get a database password. We managed to obtain the SSH key from the other WordPress Plugin.
As for the root flag, you need to access VirtualBox encryption to obtain LUKS where we will able to retrieve the Root’s Password
Information Gathering on Moderators’ Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN

Only two-port are open for this machine.
Therefore, let’s access the website interface

When i trying to analyze the website, i didn’t find any interesting thing that we can abuse.
As a result, let’s directory enumeration using gobuster

Sadly, there’s no directory that we can look further.

Those are the fuction that we can look inside the website interface.

It looks like a walkthrough for the attack’s report

The screenshot above shows the example of the report

There is no subdomain that we can look for further escalation.
Oh no! I’m running out of ideas at this moment.

After a while, i just notice that the report id is totally different
Let’s enumerate the report id using wfuzz

At last, we have a bunch of id that we can use


Wow! It’s a valid report id that contains some information inside.

Inside one of the report, there’s a additional information such as the LOGS: logs/

However, only the blank page has been shown to us.

However, when we access the logs.pdf location which it show the information such as logs removed

We should be converting the actual id into md5

As a result, we have some information been shown as above.

Finally, we have found a file upload page from the previous activity.

Let’s create a malicious pdf file that which we will use it for obtaining a shell on the mac


We have inspected the packet via Burpsuite which looks like the above.

Sadly, we got an error even though we uploaded the pdf file.

Therefore, let’s bypass the packet by adding the %PDF-1.5 and %%EOF on the packet itself.

The file uploaded is a success.


At last, we managed to obtain a shell by using the method above.
Using Chisel

We are required to transfer the chisel into our victim’s machine so that we can execute the port forwarding


The screenshot above show that the port forwarding is a success.

It look like a WordPress interface




Therefore, we can create a file called wp-load.php which contain the reverse shell command but sadly, the file cannot be created at all.


As a result, we need to create the file on our attacker’s machine and move it into our victim’s machine.


At last, we managed to retrieve the reverse shell connection back to us.



We can read the user flag by using the command “cat user.txt“
Escalate to Root Privileges Access on Moderators machine




We can access the machine by obtaining the SSH private key and downloading it into our attacker’s machine

Finally, we managed to access it using the SSH service.

There’s a new directory has been stored inside the /opt directory

I notice that the file that was saved inside the /opt/site.new is WordPress file

Inside the wp-config.php have stored a Database configuration such as Database name, username, and password.


We can execute the SQL command so that we can access the Database.

We can generate the WordPress password Hash Generator over here

Therefore, let’s reset the password by running the command above.

However, the website connection was been reset for some reason

After a while, we managed to solve the issues


Let’s access the wp-admin directory on the website itself.

We should enter the credentials that we created earlier on the SQL Database.

As a result, we managed to see the WordPress Dashboard

There’s a plugin that I haven’t seen before for WordPress


It’s a SSH private key for john which we might be able to login as John


Let’s copy and paste the SSH private key into our attacker’s machine

At last, we managed to access the machine as John

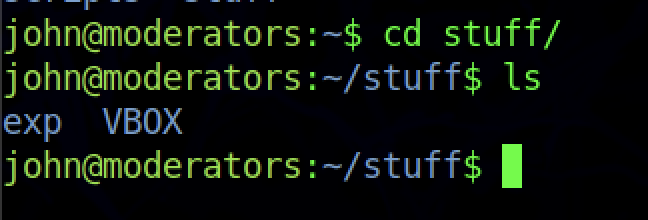

There is a file that looks like a VirtualBox file

From the result above, we are aware that John can run sudo as all

Finally, we managed to change from john to root

We can read the root flag by running the command “cat root.txt“
Extra Information


No responses yet