In this post, I would like to share a walkthrough of the Phoenix Machine from Hack the Box
This room will be considered as a Hard machine on Hack The box

What will you gain from the Phoenix machine?
For the user flag, you will need to abuse a vulnerability on asgaros-forum and use an exploit that is available on the internet. We also enumerate MySQL database and wp-login to escalate to user privileges access.
As for the root flag, you need to take advantage of the cron job where we can throw a reverse shell on the machine
Information Gathering on Phoenix Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN

The Nmap result shows three open ports such as 22, 80, and 443.
Let’s access the website interface

Sadly, there is nothing we can see on the website interface.
Let’s execute the gobuster tool to enumerate the directory on the machine.

However, I notice that there is a WAF has been implemented on the machine. As a result, let’s analyze the website source code

I have managed to find the CMS that the website is using which is WordPress 5.9
Let’s start running wpscan tool to check on the WordPress


From wpscan tool result, I notice asgaros-forum is outdated which we can take advantage of
Let’s do some research on asgaros-forum


The screenshot above shows some warning that we can make use of it

We can use the exploit.py from the website and execute the command such as python3 exploit <url> <.phtml file>
Let’s start our nc listener so that reverse connection back to us.

We didn’t receive a response on the website which looks good.

Voila! We managed to retrieve our reverse connection back to us.
Let’s establish a proper shell




Let’s roam the machine to see any interesting file or folder




We managed to find the two-factor folder as shown above

The file contains a lengthy line which I didn’t manage to find any interesting



We managed to find a MySQL password that we can use for the database on the machine

Let’s access the MySQL database using the credentials that we found earlier.






We found password hashes that we can crack later.

We can crack using the john tool but I didn’t have a screenshot to show over here.

Let’s see what is stored in /etc/security/access.conf file

I notice that there’s an IP Address of 10.11.12.13


I notice that there’s an IP Address of 10.11.12.13

Let’s access the localhost interface using the ssh service
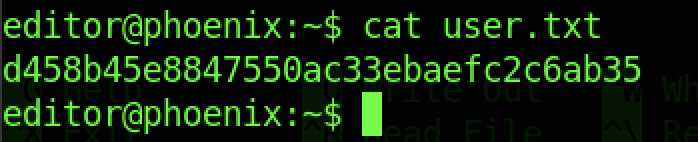
We can read the user flag using the command “cat user.txt”
Escalate to Root Privileges Access

Let’s run the usual command such as sudo -l to escalation

Let’s monitor the processes that run on the victim’s machine by executing the ps aux command

There is a file called cron.sh.x which looks weird to me.

Let’s execute the file

I have found out that the rsync –server -te.LsfxC –ignore-existing . /backup that we can abuse it

We can add a new file on backups

We can abuse the SUID of rsync that is stated on gftobins


After a few minutes, the /bin/bash does not change to the SUID file

Let’s throw a reverse shell on the command

We got a root reverse shell


We can read the root flag by executing the command “cat root.txt“
-THE END-
Happy Learning Guys!
Extra Information on Paper machine
We can go to /etc/shadow so that we can unlock and read the write-up


No responses yet