In this post, I would like to share a walkthrough of the Extension Machine from Hack the Box
This room will be considered a Hard machine on Hack the Box

What will you gain from the Extension machine?
For the user flag, you will need to find leaked multiple information from the management/dump which will try to brute-force the token. By exploiting the IDOR vulnerability to verify the username of “jean”. We also can bypass the cross-site scripting filters to attack the Gitea’s API which lead to find a backup file frm the another user. Once we completed the downloading the backup file on our attacker’s machine, we will find a SSH access to the host. and some password to use on the next user.
As for the root flag, you need to enumerate more on MySQL database and insert a command injection on the MySQL database. and get RCE on the website which we are required to validated our account. The docker socket (docker.sock) which can be found on te container can be writable which lead to a simple container breakout
Information Gathering on Extension Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start the information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN

Only two-port are open for this machine
Let’s access the website interface

However, the website interface didn’t show any interest that we can make use
Therefore, let’s enumerate the website directory by using gobuster

Nothing much to see except for the login and register directory

Sadly, We don’t have any credentials that we can use to access the interface

Let’s see the source code of the website if we might find some interesting code embedded together. Finally, we found some code that looks interesting to us.


However, when we try to inspect the management/dump on burpsuite where we stumbled upon an error of “405 Method Not Allowed”
Get information using Burpsuite

We will need to inspect the login page and I notice there’s a JSON code on line 19

For this attack, i just need to change login to management/dump and modify the JSON item to something such as:
{
“download”:”users”
}

The result will be shown something such as above
“name”: “Gia Stehr”,
“email”: “gia@snippet.htb”,
“password”: “ef92b778bafe771e89245b89ecbc08a44a4e166c06659911881f383d4473e94f”,
However, i notice that the credentials that have been highlighted above
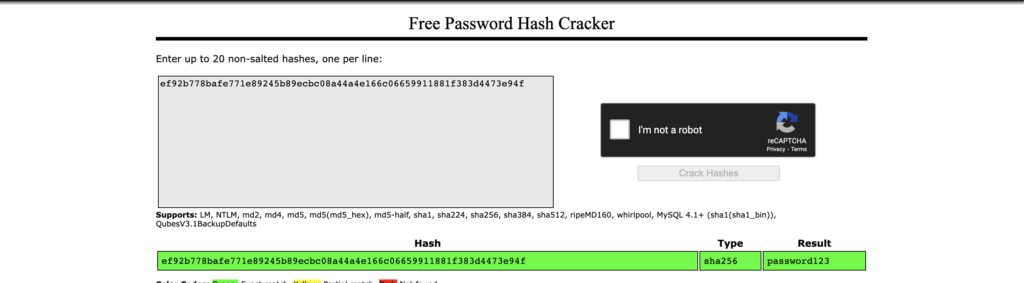
At last, we managed to obtain a password for username gia from here
Snippet Dashboard and read the snippet’s hidden message

Finally, we managed to access the dashboard for the git

There’s something written on one of the snippets. I managed to notice that this snippet parks under snippet/1
I’ve been thinking if there’s another snippet than snippet/1

Sadly, we cannot see anything on snippet2 which we are not authorized to view this snippet

However, there’s no snippet/3 has been stored on the website or server
Let’s try to bypass the snippet/2 so that we can read the hidden message

Let’s create our own snippet such as shown above.

Therefore, let’s edit the snippet that we created earlier and move it to snippet/2

Boom! We have finally seen the hidden message where it’s a curl command. However, I notice that authorization has some base64 encoded
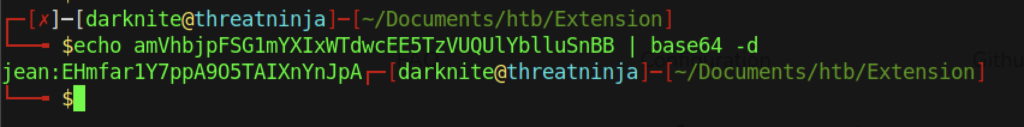
As a result, let’s try to decode the base64 code and I notice that it’s some credentials for some website

From the gobuster output, there are a lot of subdomains where we can see the status 200. It’s ridiculously hard and confusing, to be honest.

As a result, let’s enumerate using wfuzz which will result in lesser payload
gitea’s enumeration on extension machine
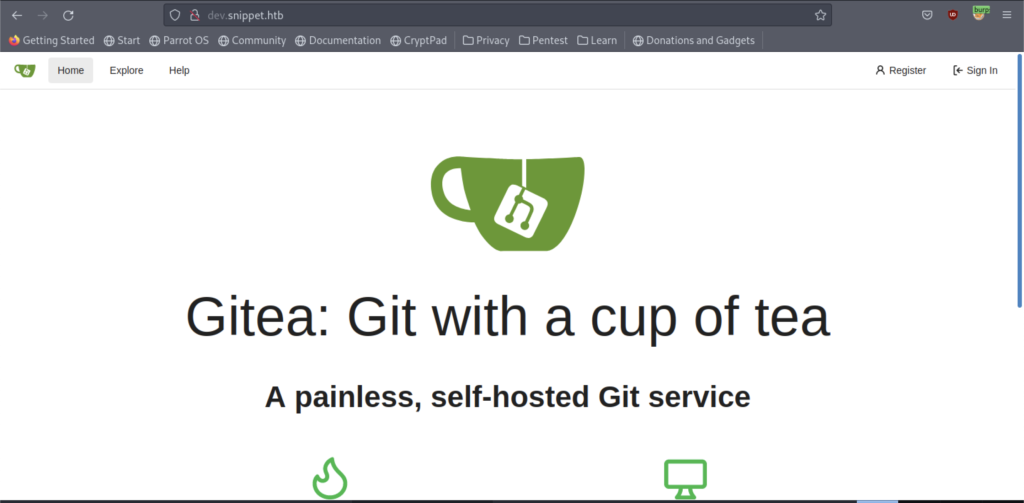
Finally, we got dev.snippet.htb website that shows a Gitea Website. However, we already know that the other subdomain will be Gitea Based

We managed to access the Gitea Dashboard using jean’s credentials

Inside jean’s extension repository, there are a few files that we can investigate

Let’s try creating a new issue for the extension’s repository

Therefore, let’s start our python server

Let’s create the issues as above and save them as any name

We managed to retrieve a file that doesn’t exist at all.

At last, we managed to obtain Charlie’s backup folder into Gitea’s Dashboard


As a result, let’s download the file to our attacker’s machine


We managed to find an SSH private key that we can use to access the machine via SSH service.


Finally, we successfully access the machine via SSH service

Sadly, we cannot find the user flag inside Charlie’s home directory

However, the user flag is stored in jean’s directory

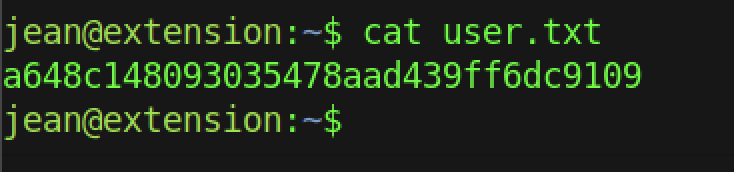
We can read the user flag by typing the command “cat user.txt”
Escalate to Root Privileges Access

From the netstat output, we can see that there are some ports open within the server such as the database port open.

Sadly, we cannot execute the MySQL database command within the server itself.

Therefore, let’s run the MySQL command from the attacker’s side by doing the port forwarding method.


Once we managed to login into the database, we can execute the command to update the role of the gia@snippet.htb into the manager’s role

As a manager, we can create a new user into the database which contains a reverse shell together.

We can start our listener so that we can retrieve our connection back to us.

After searching for the username on the Dashboard, we managed to see it at the end of the page. For us to obtain the reverse shell connection, we are required to click the “Validate” Button.

Finally, we managed to retrieve back the connection

Sadly, only a file called docker.sock is saved inside the /app directory.

We can execute the command above to get /bin/bash as SUID Binary

Finally, we have successfully into the root’s bash shell

We can read the root flag by typing the “cat /root/root.txt” command
Extra Information


No responses yet