In this post, I would like to share a walkthrough of the Ransom Machine from Hack the Box
This room will be considered as a Medium machine on Hack The box

What will you gain from the Ransom machine?
For the user flag, you will be using burpsuite to play with JSON code so that we can access some files on the website interface.
As for the root flag, you need to enumerate harder on the application file where you will be able to find the password to the root access
Information Gathering on Ransom Machine
Once we have started the VPN connection which requires download from Hackthebox, we can start information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN

There are a few ports such as 22 and 80 which are open to the public.
Let’s access the website interface

The website interface only shows a simple page that requires to enter something and clicking login
Enumeration with Burpsuite

Let’s inspect the packet using BurpSuite.
From the burp packet, I managed to notice that there’s a cookie XSRF-token and laravel_session.
To be frankly honest, I’m not sure about the laravel_session, and let’s read the information over here

Let’s change the request method so that we can the request packet to retrieve the response packet.

However, the website response shows a JSON programming

We can change POST request to GET request where we retrieve a different JSON response


Source: JSON Data Types (w3schools.com)

Let’s execute the JSON Boolean into play and we got the message state “Login Successful”
As a result, let’s inspect the packet again and replace it with the request above.

Just forward all the way.

The website interface has given us a page where you can download two files as homedirectory.zip and user.txt

We can get the user flag using this method.

Let’s download the homedirectory.zip file into our machine

Once the file has been fully downloaded into our machine, we can move the file into our HTB directory.

Let’s try to extract the file but sadly it requires a password for it to proceed.

I did try to crack the zip password by transferring the zip format to john, but it was badly encrypted.

We can use tools such as 7z to look at what kind of file has been stored inside the zip file.


We also can find any file format or method which can use for further escalation. I notice that ZipCrypto is the method that has been used for the file.
Let’s do some research on the exploit

I managed to find the link to the exploit but sadly it’s not the information that i needed. Therefore, let’s continue doing the research.


Finally, I have managed to find the right information over here
Change the password of the zip file
From the information that we found here, let’s use bkcrack tool for further inspection.

Let’s download the tool into our machine.

Once the file has been fully downloaded into our machine, we can move the file into our HTB directory.

For me, i need to extract the tool manually for some reason.


Let’s access the bkcrack directory and let’s see inside the directory.
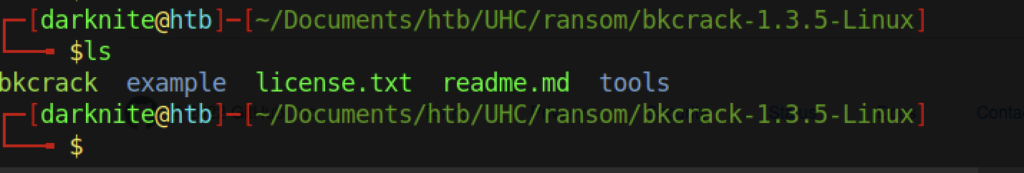
Luckily! There’s a Binary file that we can use over here.

The screenshot above shows the manual of the tools

Let’s follow the instruction that has been written on the website previously. Sadly, we have an error saying that they could not open the input file.
After a few hours of troubleshooting, we are required to zip the .bash_logout into anyfilename.zip (which in my case, i use darknite.zip)

Voila! It works like a charm

It will take around a few seconds to completed and we managed to retrieve the key

We can use the command above to change the password of the zip file.

As a result, we were able to unlock the zip file using the password that we use for change.

There’s nothing except for the zip file.

We will be able to see other files when we run the command “ls -al“


A folder of .ssh has caught my attention where we might find ssh private and public keys.

From the ssh public key, we managed to verify one of the users that can access the machine.

We can access the machine via ssh service using the id_rsa file that we found earlier.

We can also read the user flag by executing the command “cat user.txt“
Escalate to Root Privileges Access on Ransom machine

Let’s try to enumerate manually on the server for the SUID file

The Linux terminal is looking okay

When i was roaming on /etc/ directory, i found some interesting directories which we can use later.

Let’s see on the /etc/apache2 whether there’s a new subdomain that we can use.




Inside the 000-default.conf file, there’s a DocumentRoot that located at /srv/prod/public

There are some directories and files that have caught my attention especially public and app


The screenshot above shows some configuration file

Let’s access /app/HTTP/Controllers directory

The file such as AuthContrroller.php look interesting to look into


I managed to find a password that we can use as a root
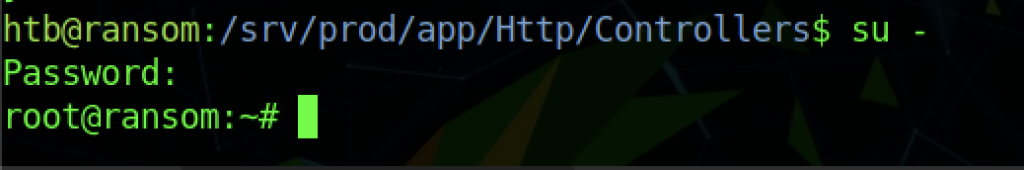
Let’s try the password as root and it works

We also can access the ransom machine via ssh service

We also can read the root flag using the command “cat root.txt“

No responses yet