In this post, I would like to explore more binary exploitation such as nreport which will improve my skills and knowledge. For a record, the binary file is coming from OverGraph Machine on Hack the Box Platform.

Before we start to analyze the binary file, we can obtain some information on the binary by running some command such as ldd nreport

When we try to execute the binary, the program is asking for some token so that it can proceed with the next step.
Analyze the nreport using the GDB tool

As a result, we can analyze the file by using the GDB tool for a better understanding of the binary.
Anyway, those who don’t know what is GDB’s purpose can read the information over here
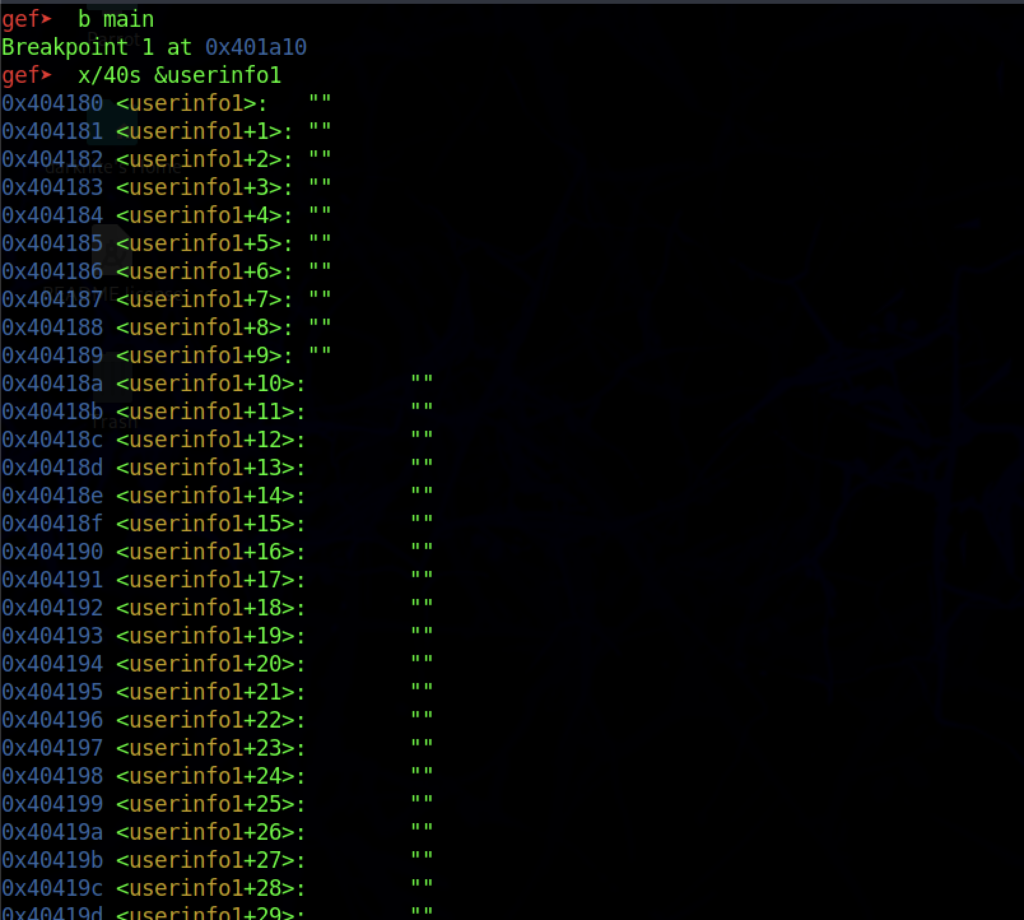
Let’s skip some steps on the binary analysis where we can break the code by using b main and list the sequel by running x/40s userinfo1


Therefore, let’s try to see what happens after we execute the binary file (nreport) which it shows not much information on the binary


From the analysis of the previous post especially, we are aware of the token for the binary.
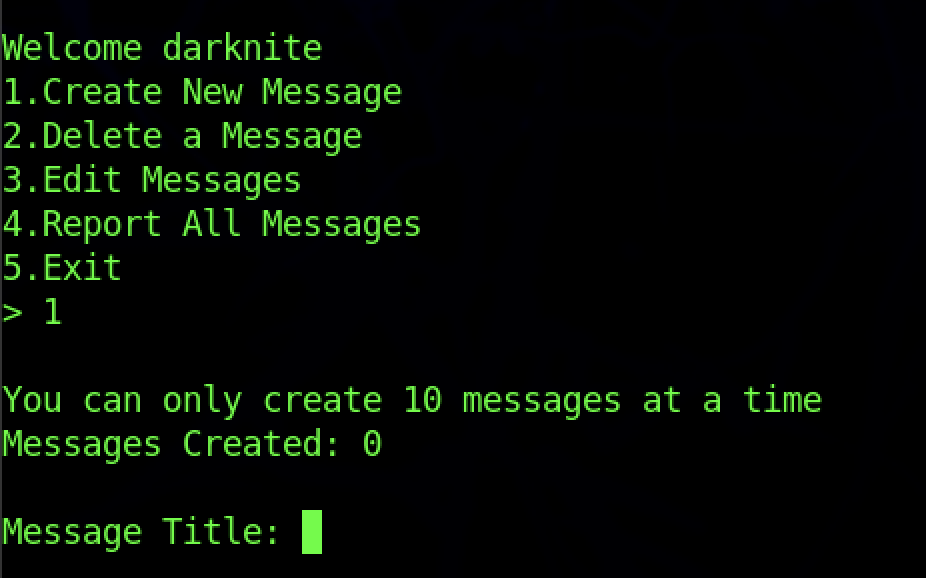
Let’s try to create a message to see what happens after that process.


However, there are some errors such as Segmentation Fault when trying to create a message
Analyze using Ghidra tool

We can upload the binary on Ghidra and we can start the analysis straight-away

The screenshot above shows the creation code where we can see that all the process that create is using

The screenshot above shows the authentication code where we can retrieve the token by looking at the code over here.



The several screenshots above show the main function of the binary


The screenshot above show the edit and delete function that can use on the binary whenever you execute it

No responses yet