In this post, I would like to share a walkthrough of the RedPanda Machine from Hack the Box
This room will be considered an Easy machine on Hack The box

What will you gain from the RedPanda machine?
For the user flag, you will need to exploit the SSTI vulnerability in a Java web Application so that we can obtain the shell.
As for the root flag, you need to exploit the Java application that the root’s access to has been assigned credit to various authors. Need to generate a malicious JPG image that will be injecting a log that pointed to the image created. We will be able to obtain the root’s private SSH key where the image or metadata that exploited a directory traversal to XML external entity attack
Information Gathering on RedPanda Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN

Let’s access the website interface

Nothing much that we can see on the website itself

Let’s try to execute the code using the SSTI method but sadly failed
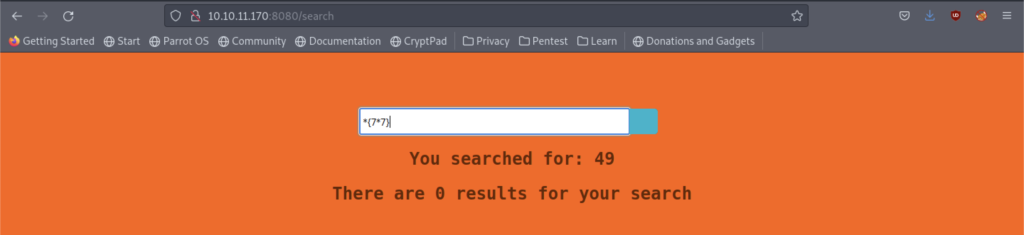
It works!

Let’s download the script to execute the ssti-payload as shown above

We have the converted payload

The screenshot above shows the result of the request for the SSTI payload

Finally, we notice there are credentials that we can take advantage

At last, the credentials work on the SSH service

We can read the user flag by using the command “cat user.txt“
Escalate to Root Privileges Access

Sadly, there’s no SUID binary that we can make use of when running the command “sudo -l”


Let’s read again the source we found earlier
public static String getArtist(String uri) throws IOException, JpegProcessingException
{
String fullpath = "/opt/panda_search/src/main/resources/static" + uri;
File jpgFile = new File(fullpath);
Metadata metadata = JpegMetadataReader.readMetadata(jpgFile);
for(Directory dir : metadata.getDirectories())
{
for(Tag tag : dir.getTags())
{
if(tag.getTagName() == "Artist")
{
return tag.getDescription();
}
}
}
return "N/A";We managed to see that we can abuse the metadata that normally been using with exiftool tool.
However, we can use the command such as Exiftool -Artist=”../home/woodenk/darknite” darknite.jpg

As a result, we need to transfer the picture that we have been modify using the ExifTool into the victim’s machine

Inside the victim’s machine, we need to create a file that contains the source code shown above.

From our attacker’s machine, we need to execute the curl command with the User-Agent which it will put using the directory that we put the ExifTool picture

After a while, we managed to obtain an SSH Private Key stored inside the file that we put on the machine


At last, we can access the machine as root via SSH service

We can read the root flag by executing the command “cat root.txt”
Extra Information


No responses yet