In this post, I would like to share a walkthrough of the Trick Machine from Hack the Box
This room will be considered an Easy machine on Hack The Box

What will you gain from the Trick machine?
For the user flag, you will need to exploit SQL Injection that allows bypassing some authentication which we can read files from the system. We can also obtain an SSH key by taking advantage LFI attack
As for the root flag, you need to abuse fail2ban
Information Gathering on Trick Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN

Let’s access the website interface

Nothing that we can look into the website itself

The website still didn’t show anything that can be used even though we add the host on the /etc/hosts
Let’s enumerate the website directory by using gobuster

We didn’t manage to see any directory that had been analyzed into
At this moment, I’ve stuck and cannot see any method for further escalation.

Let’s try to gather information by using the command above. However, we can sight two new subdomains
- root.trick.htb
- preprod-payroll.trick.htb

When accessing the website URL Address, we have been redirected to a login page. Sadly, we dont have any credentials that we can use over here.


Let’s try to enumerate it by using sqlmap. Therefore, let’s incept the packet using burpsuite and save it as login.req


There are two databases when i try to run the sqlmap command

As a result, let’s enumerate more on the payroll_db and found the tables as shown above

We have to retrieve the credentials that we can use later.
Let’s execute the command such as sqlmap -r login.req –file-read=/var/www/market/index.php


Finally, we managed to see the source code of the file


We also can obtain the information by using the curl command such as show above

Therefore, let’s grab the ssh private key using this method

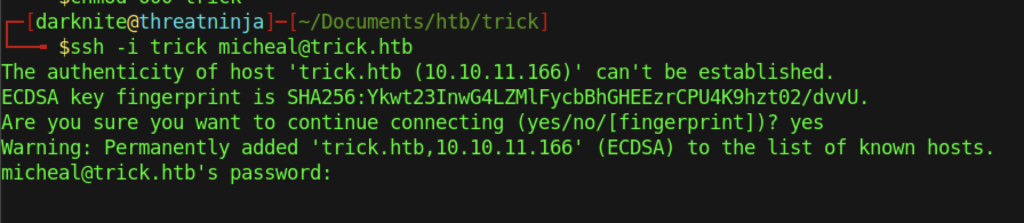
This is weird! By default, we should be able to login into the machine via ssh service

My mistake! I mistype the username of the machine


We can read the user flag by typing the “cat user.txt” command
Escalate to Root Privileges Access

As usual, we need to find the binary SUID file to proceed to the next step.

Let’s see what file is been stored in the /etc/fail2ban/action.d directory

After a while, all the files inside the action.d went missing.
Let’s do some research on the fail2ban escalation method

We found some articles on the escalation method

Let’s execute the command above.
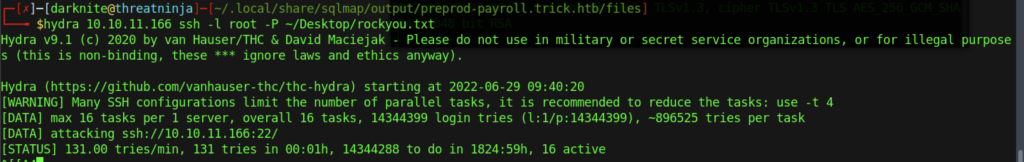
Next, we need to brute-force the ssh session by using hydra

After a while, we managed to get /bin/bash assigned to the SUID Binary

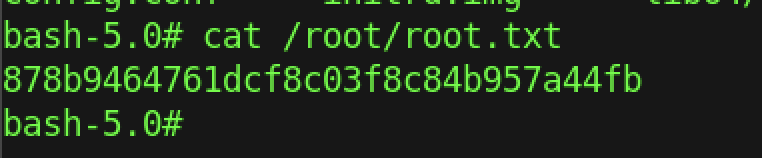
We can read the root flag by typing the “cat /root/root.txt” command
Extra Information

No responses yet