In this post, I would like to share a walkthrough of the Meta Machine from Hack the Box
This room will be considered as a medium machine on Hack The box

What will you gain from Meta machine?
For the user flag, you will need to abuse the ExifTool exploit so that we can upload images to the machine.
As for the root flag, you need to abuse neofetch to obtain a root shell on the machine
Information Gathering on Meta Machine
Once we have started the VPN connection which requires download from Hackthebox, we can start information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN

From the nmap result, there’s two open port such as ssh and http.
Let’s access the website interface

Sadly, the website is showing an error “page not found“

After we have whitelisted the domain into our /etc/hosts, we finally got a proper website interface.

However, we didn’t get any interesting that we can make use of within the website.
Let’s enumerate the website by using gobuster

There’s nothing been highlighted on the gobuster result

Let’s look for a subdomain that has been stored within the website

We found a simple page within dev01.artcorp.htb website interface but there’s a link been displayed on the interface that stated “MetaView“
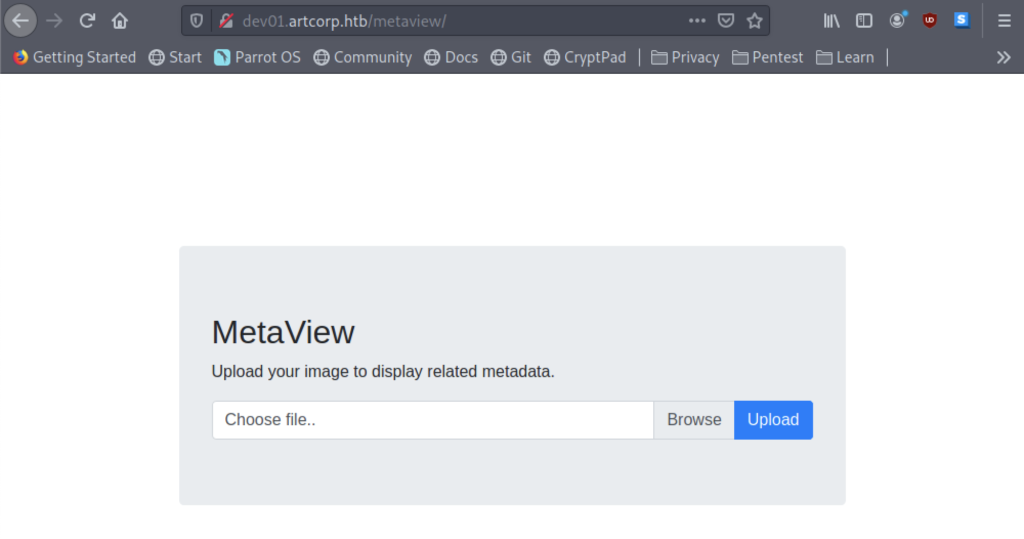
When we have successfully accessed the MetaView, we are presenting with an upload page

Gaining Privilges Access on Meta Machine

Sadly, the activity is a failure where it also allowed only jpg/png

The output is things that I have recently seen when I’m doing some forensic activity before

The screenshot above shows the output of the ExifTool


We can download the exploit by using the git clone https://github.com/convisolabs/CVE-2021-22204-exiftool.git command


We should execute the python file from the GitHub website before
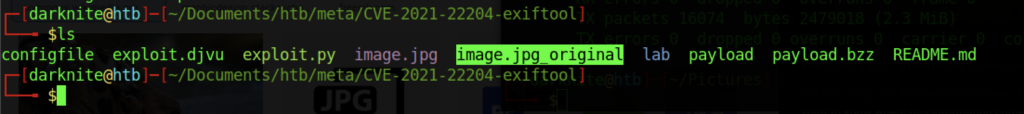
The process will be creating an image file which we are required to upload later on

Let’s start our nc listener on our own attacker’s machine

We should be uploading the image.jpg that has been created by the python file previously

Therefore, we should be able to retrieve the reverse shell connection back to us
Establish a proper shell





The screenshot above shows the step of how to obtain a proper shell
Maintaining the Priviliges Access

While roaming inside the server, i have noticed that there’s a folder on the /var/www/dev01.artcorp.htb called convert_images

There is a sh file that looks weird to me at least.

From the script, I notice that there’s a method that we can take advantage of with this file.


The content of the file will something as shown above.

Let’s cp the file into /var/www/dev01.artcorp.htb/convert_images/
Then, let’s wait for a while because the cron job will proceed with the rest. However, it will take a few minutes and you can obtain the ssh id_rsa on the /dev/shm

We successfully access the machine via ssh service using the ssh id_rsa that we obtain on the previous activity


We can read the user flag by running the command “cat user.txt“
Escalate to Root Privileges Access

As usual, we can run the command “sudo -l” to see if any SUID file that we can abuse
Sadly, I have no knowledge of some of the commands shown above, and let’s do some research on it


I managed to find some information about XDG which I have some directory such as highlighted above

I found some information that related to neofetch as mentioned above



Some information has stored inside /home/thomas/.config/neofetch


We run those commands above trying to obtain a root shell but it goes down as a failure

My bad! We need “sudo” so that it can execute properly

Uwu! We have finally obtained a root shell

We can read the root flag by running the command “cat root.txt“
-THE END-
Happy Learning Guys!
Extra Information on Meta machine
We can go to /etc/shadow so that we can unlock and read the write-up


No responses yet