Case Scenario
We recently hired some contractors to continue the development of our Backup services hosted on a Windows server. We have provided the contractors with accounts for our domain. When our system administrator recently logged on, we found some pretty critical files encrypted and a note left by the attackers. We suspect we have been ransomwared. We want to understand how this attack happened
via a full in-depth analysis of any malicious files out of our standard triage. A word of warning, our tooling didn't pick up any of the actions carried out - this could be advanced.Firstly, we need to download the zip file into our machine and extract the file to proceed further

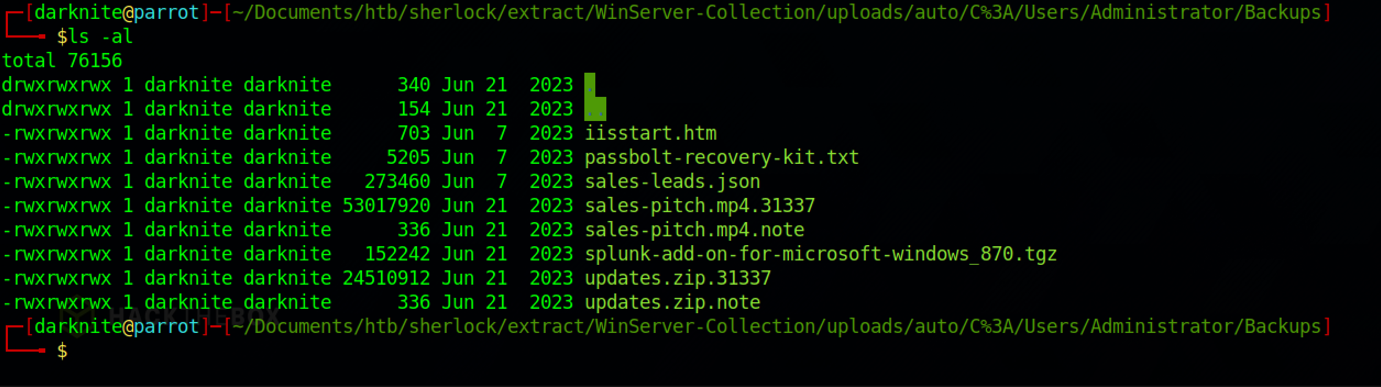
From the screenshot above, we notice that there are two other files that we need to investigate deeper

Before we analyze all the files stored inside this document, we can try to unzip the WinServer Collection log.

We managed to find the password of the potential to unlock the zip file.

At last, we have successfully unlocked the file.



The screenshots above show the file that is stored inside the zip file.
Testing
- 2. Which command did the TA utilise to escalate to SYSTEM after the initial compromise?
- 3. How many files have been encrypted by the ransomware deployment?
- 4. What is the name of the process that the unpacked executable runs as?
- 5. What is the XOR key used for the encrypted strings?
- 6. What encryption was the packer using?
- 7. What was the encryption key and IV for the packer?
- 8. What was the name of the memoryfd the packer used?
- 9. What was the target directory for the ransomware?
- 10. What compression library was used to compress the packed binary?
- 11. The binary appears to check for a debugger, what file does it check to achieve this?
- 12. What exception does the binary raise?
- 13. Out of this list, what extension is not targeted by the malware?
- 14. What compiler was used to create the malware?
- 15. If the malware detects a debugger, what string is printed to the screen?
- 16. What is the contents of the section?
- 17. What file extension does the ransomware rename files to?
- 18. What is the bitcoin address in the ransomware note?
- 19. What string does the binary look for when looking for a debugger?
- 20. It appears that the attacker has bought the malware strain from another hacker, what is their handle?
- 21. What system call is utilised by the binary to list the files within the targeted directories?
- 22. Which system call is used to delete the original files?
1. Which user account was utilised for initial access to our company server?

2. Which command did the TA utilise to escalate to SYSTEM after the initial compromise?


3. How many files have been encrypted by the ransomware deployment?
33
4. What is the name of the process that the unpacked executable runs as?


5. What is the XOR key used for the encrypted strings?


6. What encryption was the packer using?
AES-256-CBC
7. What was the encryption key and IV for the packer?






8. What was the name of the memoryfd the packer used?

9. What was the target directory for the ransomware?

10. What compression library was used to compress the packed binary?
zlib
11. The binary appears to check for a debugger, what file does it check to achieve this?
/proc/self/status
12. What exception does the binary raise?
SIGSEGV
13. Out of this list, what extension is not targeted by the malware?
.exe
14. What compiler was used to create the malware?
gcc
15. If the malware detects a debugger, what string is printed to the screen?

16. What is the contents of the section?

17. What file extension does the ransomware rename files to?
18. What is the bitcoin address in the ransomware note?


19. What string does the binary look for when looking for a debugger?
TracerPid
20. It appears that the attacker has bought the malware strain from another hacker, what is their handle?
blitztide
21. What system call is utilised by the binary to list the files within the targeted directories?
getdents64
22. Which system call is used to delete the original files?
unlink

No responses yet