In this post, I would like to share a walkthrough of the CyberMonday Machine from Hack the Box
This room will be considered a Hard machine on Hack the Box

What will you gain from the CyberMonday machine?
For the user flag, you will need to process it front-loaded before the user flag. Initially, I’ll begin by exploiting an off-by-slash nginx misconfiguration on a website to access a .env file and the Git source repository. Subsequently, I’ll exploit a mass assignment vulnerability within the site to gain admin privileges, thereby obtaining a new subdomain for a webhooks API. Upon enumerating the API, I’ll discover its utilization of JWTs and asymmetric cryptography. Leveraging this, I’ll manipulate the system to fabricate a token, thereby securing admin access to the API. This access enables me to generate webhooks, one of which facilitates the issuance of server-initiated web requests, such as an SSRF. Exploiting a CRLF injection in one of the webhooks, I’ll access the Redis database caching the Laravel session data. This access allows me to execute code within the web container. From there, I’ll locate a Docker Registry container, retrieve the API container image, and conduct a source code review, uncovering additional API endpoints requiring an extra header. Exploiting these endpoints, I’ll perform a file read on the API container, consequently extracting a user’s SSH password
As for the root flag, you need to abuse a script crafted to enable users to execute Docker Compose securely. I’ll demonstrate several methods, primarily focusing on granting container privileges, to accomplish this goal.
For those who want to learan or improve CyberSecurity skills especially Red Teaming and Blue Team, You can use the link https://affiliate.hackthebox.com/gnfp67dzy7p0 to support me
Academy link can be found https://affiliate.hackthebox.com/wanmohdariffwanmohdrosdi6259vvInformation Gathering on CyberMonday Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start the information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN
┌─[darknite@parrot]─[~/Documents/htb/Cybermonday]
└──╼ $ nmap -sV -sC 10.10.11.228 -oA initial
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-24 20:17 EDT
Nmap scan report for 10.10.11.228
Host is up (0.23s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 7468141fa1c048e50d0a926afbc10cd8 (RSA)
| 256 f7109dc0d1f383f20525aadb080e8e4e (ECDSA)
|_ 256 2f6408a9af1ac5cf0f0b9bd295f59232 (ED25519)
80/tcp open http nginx 1.25.1
|_http-title: Did not follow redirect to http://cybermonday.htb
|_http-server-header: nginx/1.25.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://map.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 61.38 seconds
┌─[darknite@parrot]─[~/Documents/htb/Cybermonday]
└──╼ $
Let’s access the website interface

Nothing that we can abuse while looking at the website.

Therefore, let’s sign up for a new account which we can abuse after accessing the dashboard.

As a result, let’s try to login by using the credentials that we created earlier.

We tried to register the same credentials as previously and got an error page which we managed to see ‘isAdmin’ => ‘boolean’;

Therefore,let’s update our profile and add isAdmin=1 after the password confirmation

As a result, we managed to sight a new tab which is a dashboard

The screenshot above shows the actual dashboard on the machine

Let’s investigate the changelog and there’s a Webhook link that we can access into

However, we cannot access the page without whitelisting it on the /etc/hosts file



Therefore, let’s register and login via the packet above.

It looks normal to me

We have one payload that we can use in the latter stage

As a result, we are required to install the JWT editor on the burpsuite


We should add “kid”:”anything”

At last, we are presented with public key

Let’s use the jwt_tool for the next stage

After a while, we managed to obtain the jwt hashes



Boom! We can test the method

It works like a charm!


Redis Enumeration on the CyberMonday machine


After a while, we managed to obtain information on redis



Let’s execute the Redis Exploitation


As shown above, we are able to replicate the redis database on our attacker’s machine



The screenshot above shows the actual and real packet inside the laravel session



Therefore, let’s insert the payload into the Redis server.

At last, we managed to obtain the reverse shell connection

Let’s download docker-grab on our attacker’s machine

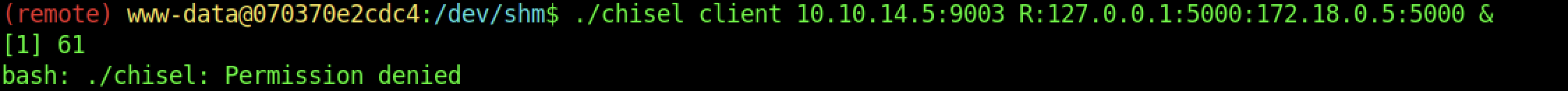


By default, we should do port-forwarding on the machine.

It didn’t work at all


Each person will have a different IP to play with

At last, we are able to download the docker file


At least, we can retrieve the api_key

Let’s access the MySQL database with the credentials as root:root





We can retrieve the information on webhooks

Boom! We have obtained the password for John’s credentials


We can read the user flag by typing the “cat user.txt” command
Escalate to Root Privileges Access

As usual, we need to find the SUID binary by using the command “sudo -l”

Let’s start our listener on our attacker’s machine

The Python code of binary looks something as shown above


We can execute the binary with yml file which it hangs!

At last, we managed to get root reverse shell

Finally, we can mount the root drive into the docker


We can read the root flag by typign the “cat root.txt” command
Extra Information

No responses yet