In this post, I would like to share a walkthrough of the Derailed Machine from Hack the Box
This room will be considered an Insane machine on Hack the Box

What will you gain from the Derailed machine?
For the user flag, you will need to create a new user with XSS script notes on the rails notes application which the notes report will be reviewed by the admin. We will be using the administrator’s browser session so that we can read the admin page with a file read vulnerability.
As for the root flag, you need to exploit the vulnerability on openmediavault’s RPC which we can insert a SSH key for root access
Information Gathering on Derailed Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start the information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN
# Nmap 7.92 scan initiated Tue Feb 21 07:37:12 2023 as: nmap -sC -sV -oA initial -Pn 10.10.11.190
Nmap scan report for 10.10.11.190
Host is up (0.19s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 16:23:b0:9a:de:0e:34:92:cb:2b:18:17:0f:f2:7b:1a (RSA)
| 256 50:44:5e:88:6b:3e:4b:5b:f9:34:1d:ed:e5:2d:91:df (ECDSA)
|_ 256 0a:bd:92:23:df:44:02:6f:27:8d:a6:ab:b4:07:78:37 (ED25519)
3000/tcp open http nginx 1.18.0
|_http-title: derailed.htb
|_http-server-header: nginx/1.18.0
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Feb 21 07:37:46 2023 -- 1 IP address (1 host up) scanned in 34.79 seconds
# Nmap 7.92 scan initiated Tue Feb 21 07:37:12 2023 as: nmap -sC -sV -oA initial -Pn 10.10.11.190
Nmap scan report for 10.10.11.190
Host is up (0.19s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 16:23:b0:9a:de:0e:34:92:cb:2b:18:17:0f:f2:7b:1a (RSA)
| 256 50:44:5e:88:6b:3e:4b:5b:f9:34:1d:ed:e5:2d:91:df (ECDSA)
|_ 256 0a:bd:92:23:df:44:02:6f:27:8d:a6:ab:b4:07:78:37 (ED25519)
3000/tcp open http nginx 1.18.0
|_http-title: derailed.htb
|_http-server-header: nginx/1.18.0
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Feb 21 07:37:46 2023 -- 1 IP address (1 host up) scanned in 34.79 seconds
Let’s access the website interface
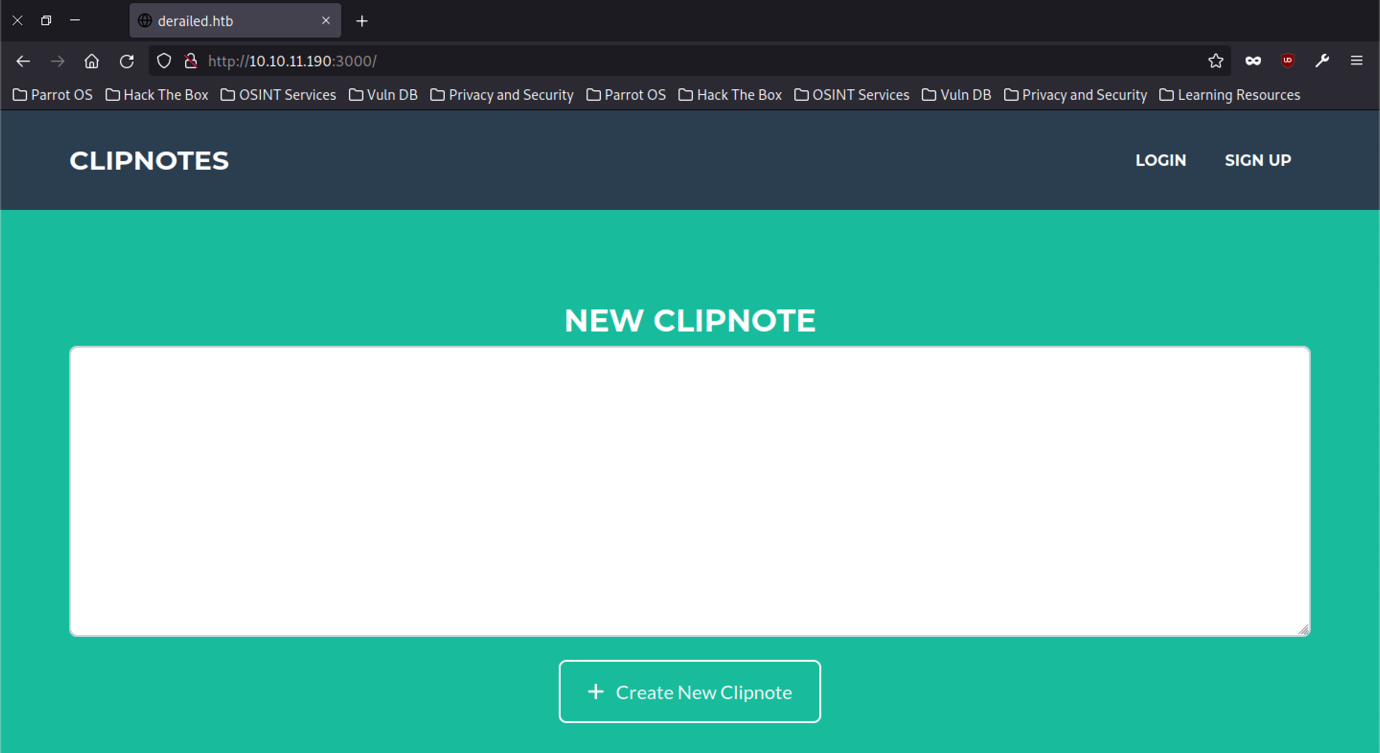
There are a few functions that we can abuse such as login, sign up, and one blank box which we can create a new clipnote




As a result, let’s try to register a new account on the website application

Therefore, let’s try to login using the credentials that we register earlier.

Nothing happens when trying to enter any malicious file


Sadly, the creator has patched this path
The intended way to escalate the privileged access




Firstly, let’s inject the packet with the XSS method and need to encode the strings to character code.


Let’s just enter just a simple payload

Let’s start our nc listener

It looks fine so far.
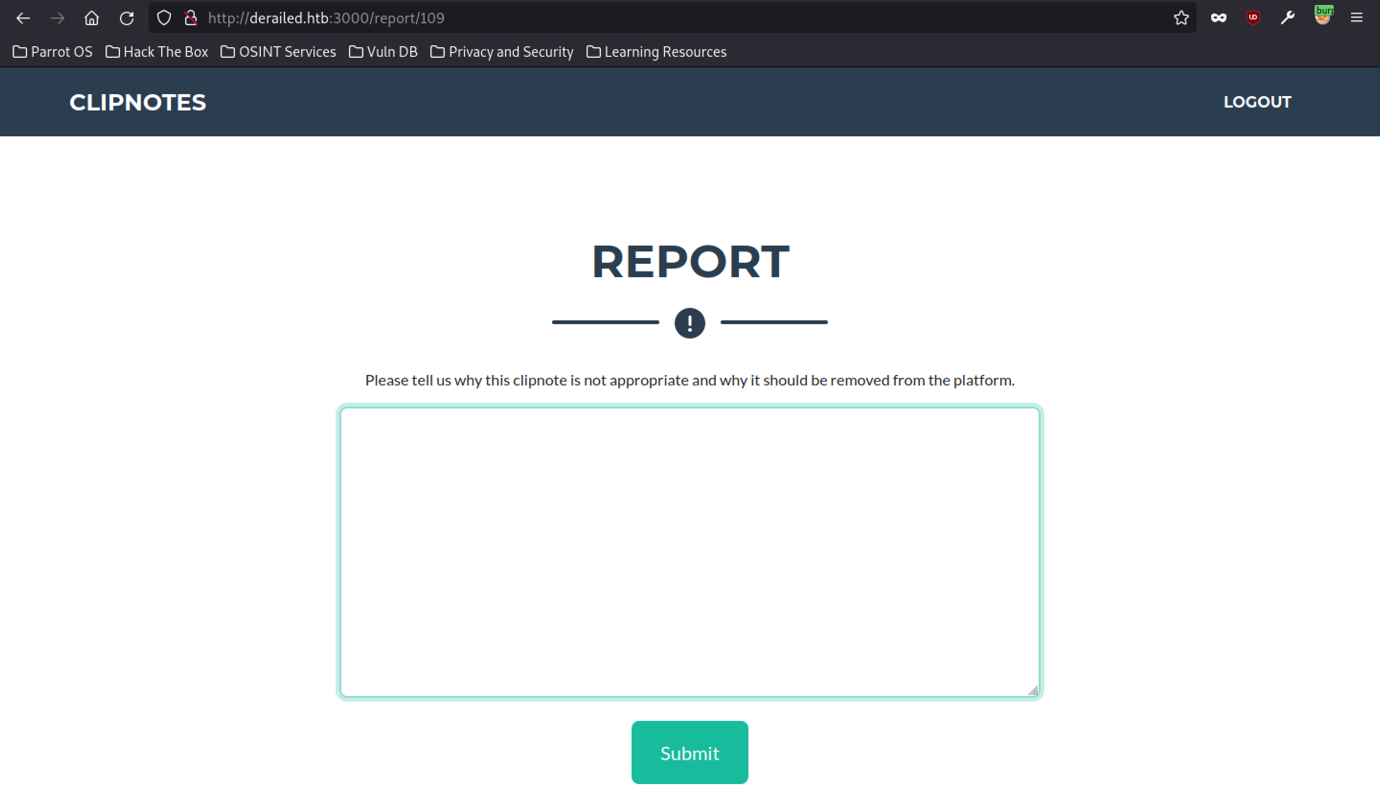
Next, we need to trigger the payload by submitting a simple command on the reporting endpoint


After a while, the malicious file has finally uploaded to the machine.

Finally, the reverse shell connection is back to us.

We can read the user flag by typing the “cat user.txt” command
Escalate to Root Privileges Access



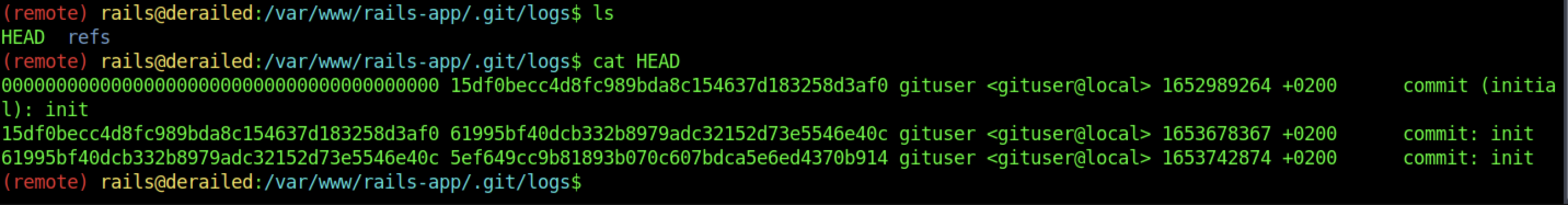
It looks like a log that we can execute.


We managed to find the username “Marcus” and “openmediavault-webgui” on the machine.



At last, we managed to find a hash for the toby’s credentials.

We are also successfully a password for the toby

It’s successful access to another user


There is a file that obviously caught my attention

Let’s execute the command above to test the omv command


Let’s try port-forwarding the machine connection

The website interface from the port-forwarding the connection.


My bad, the command should only use the omv-confdabdam read conf.system.usermngmnt.user

We are required. to modify the command as root and ssh key

Sadly, it doesn’t work at all which it’s weird to me


Finally, it has worked as I am hoping for.

Therefore, let’s execute the command that applies the change on the omv command

We can copy-paste the private key into the machine.

Boom! We have successfully the machine via SSH private key

We can read the root flag by typing into the “cat root.txt” command
Extra Information


No responses yet