In this post, I would like to share a walkthrough of the Soccer Machine from Hack the Box
This room will be considered an Easy machine on Hack The Box

What will you gain from the Soccer machine?
For the user flag, you will find a website that is managed using Tiny FileManager. We will use a PHP simple shell to get a shell on the server. While we roaming the server, we managed to find a subdomain for a new site that uses a WebSocket. The website will require a validation task in which we will exploit WebSocket SQL Injection to leak a credential to be used in the SSH service
As for the root flag, you need to abuse the dstat by using doas function which will get us a root shell
Information Gathering on Soccer Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start the information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN

Let’s access the website interface


There is nothing that we can use on the page here.


From the gobuster output, we can access a login page that related to Tiny File Manager

After finishing doing my research on the internet, i found a good website here to learn a little bit about the tiny file manager itself.

From the GitHub page, we managed to obtain a credential that we might be able to use to access the Dashboard.

At last, we have managed to access the Dashboard by typing the credentials that we found earlier from the GitHub

Based on GitHub here, we can use either bash or python script to execute our reverse shell file

Therefore, let’s start our nc listener

As a result, let’s upload a Shell code in PHP version on the uploads of the file manager

The content of the file will look something like the above.

Boom! We have successfully executed some command injections on the website


The screenshot above shows the output that we saw on the burpsuite response

As a result, let’s enter our reverse shell connection command and press Execute button

At last, we managed to retrieve the reverse shell connection back to us.

However, we managed to sight a file that looks caught my attention at first glance.

The first sight, we found out that there’s a subdomain that we can investigate further

The website of the subdomain that we found earlier looks exactly as shown in the screenshot above.

Let’s register a new account on the website which we might be able to use to access the dashboard.
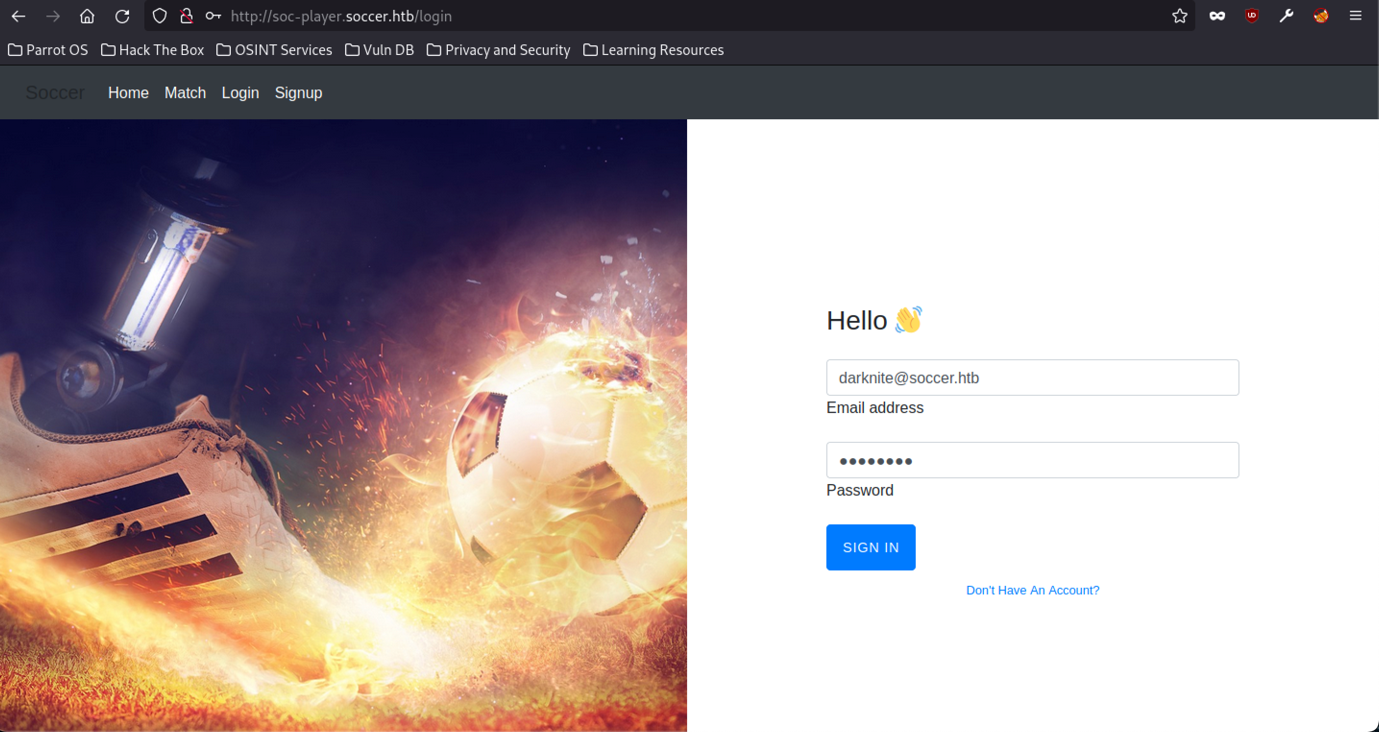
As a result, let’s access the dashboard by entering the credentials that we created earlier.

The page have re-direct to the Ticket page which we should be looking the source code to bypass the authentication

It looks like we are required to play with WebSocket which the source has given us the PATH that we can use later on

Let’s do some research on the internet and found an interesting website here where we can use Python over there to escalate further

Therefore, let’s start the Python file so we can obtain the credentials via SQLMAP

Let’s start our SQLMAP command as above.

Don’t worry about the response that we get from the websocket packet which it’s very normal

After a while, we managed to notice a few databases that we can look into


We managed to see one table inside the soccer_db database


We should be getting the credentials on the username, and password columns on the tables of accounts


At last, we managed to see the credentials in plain sight on the MySQL database

Therefore, let’s access the machine via SSH service with the credentials that we found earlier.

We can read the user flag by typing the “cat user.txt” command
Escalate to Root Privileges Access on Soccer Machine

While finding the SUID Binary with the manual way, I notice one weird file that caught my attention right away.
For those who are not familiar with doas, it is a program the function is to execute commands as another user.



We can see a configuration on doas which we can see how it has been configured on the machine

Nothing interesting for me at least.

Based on the doas.conf file, let’s run the dstat as root which we have to see the output as shown in the screenshot above.
Dstat is a program that has been used to generate system resource statistics which can be replaced by vmstat, netstat or iostat

Inside the dstat folder, we managed to see that there’s a potential way to execute as root

As a result, we should be creating a file as dstat-privsec.py which we should be able to execute via root privileges access

Finally, the bash file have been assigned as SUID binary which we can escalate to root right now

Boom! We have managed to execute the common line to get a root shell


We can read the root flag by typing the “cat root.txt” command
Extra Information

No responses yet