This post is an extension of the full writeup on the Response machine that can be found here which we will abuse the AES key
Extract the AES file by using the bulk_extractor tool on the Response machine
Firstly, we are required to download and install the bulk_extractor on our attacker’s machine
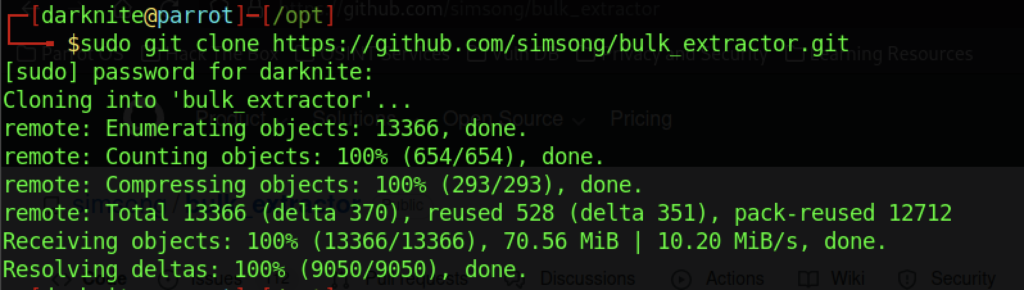
Let’s install the bulk_extractor on our attacker’s machine
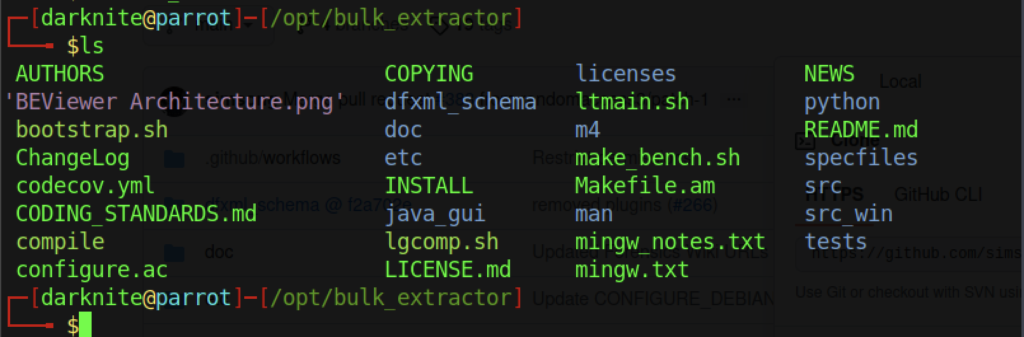
However, there are no binary files that we can use to extract the file with the binary file. As a result, I will try to install it on different platforms such as Kali Linux.
To install the binary on any Linux type of Operating System, you are required to execute the following command
./configure
sudo make
sudo make install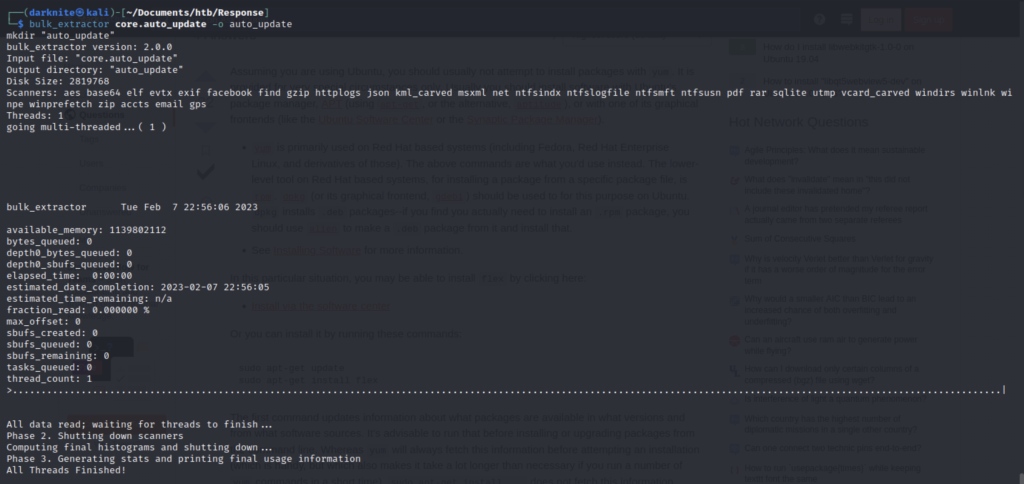
Therefore, let’s extract the file from the core.auto_update by running the command “bulk_extractor core.auto_update -o auto_update“

The screenshot above shows the process of the bulk_extractor. The result should be giving us some files that might be useful to us in the latter stage of the escalation
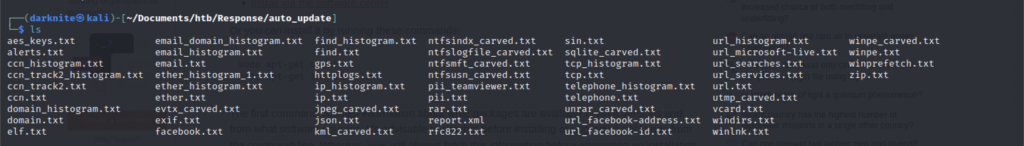
Once the process is completed, you will be provided with a bunch of files as shown in the screenshot above. However, there are a few txt files that caught my attention at a glance.
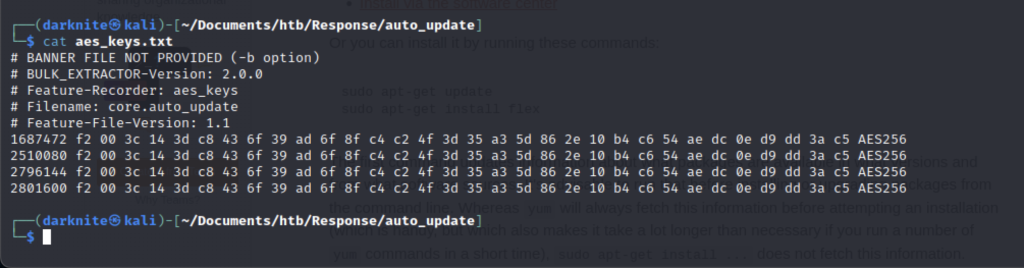
The screenshot above shows what is been stored inside the AES keys
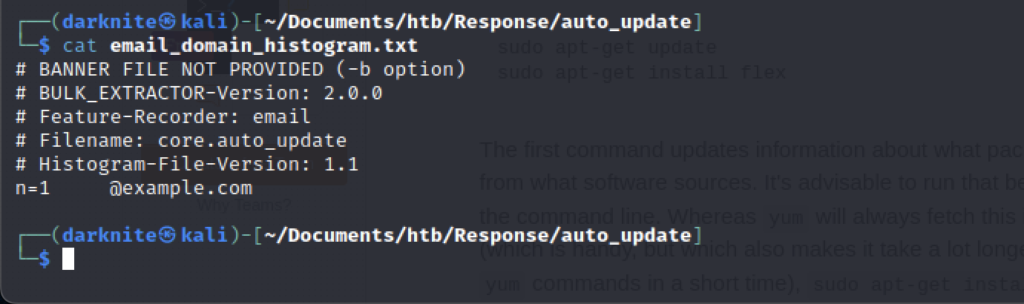
Another file content that contains an email domain history is been save inside the email_domain_histogram file
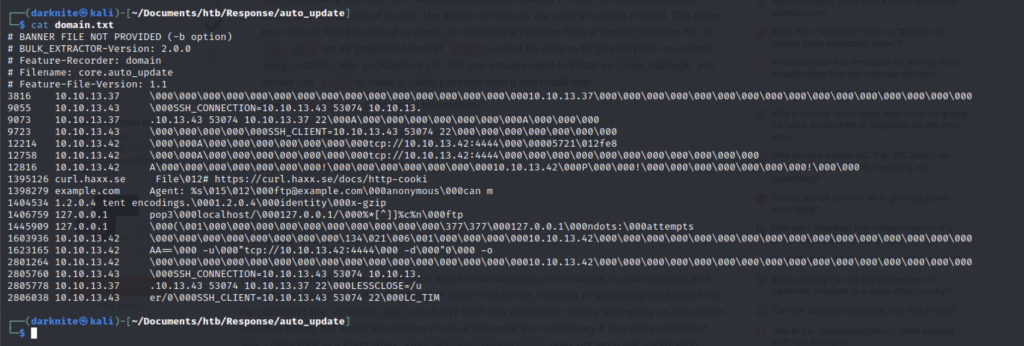
There is a lot of information when accessing the domain.txt file
