In this post, I would like to share a walkthrough of the Catch Machine from Hack the Box
This room will be considered as a medium machine on Hack The box

What will you gain from the Catch machine?
For the user flag, you will need to
As for the root flag, you need to
Information Gathering on Catch Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN



I have noticed that there are a lot of ports open by looking at the nmap result.
Let’s check the website interface on all those ports
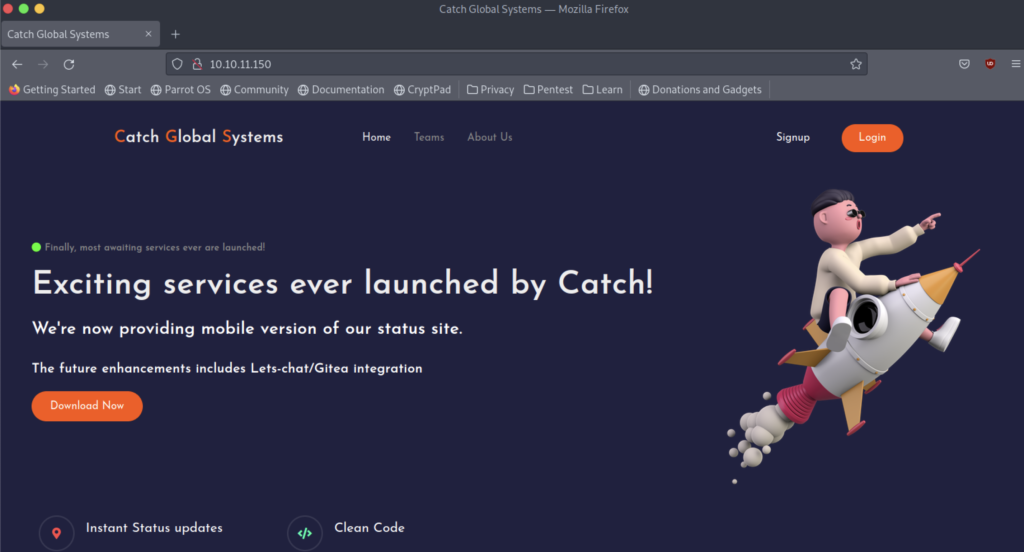
The first website using the port 80

I notice that we can download a file called catchv1.0.apk into our machine
Let’s move the file into our htb directory
Android Investigate

We can extract the apk file by using apktool which can be used for the android file format.


Let’s investigate the /res/value directory which looks weird to me.


Let’s open and read the strings.xml

We should analyze the string

I notice there’s a let’s chat token that has been embedded inside the code

Let’s access another website interface that uses port 3000

Let’s access another website interface that uses port 5000 and if you are not aware, the website interface show let’s chat.
However, let’s move on from now.


Let’s access another website interface that uses port 8000 and we have noticed that it’s a cachet login page. Sadly, we don’t have any credentials to login in.

We can use curl to try to inspect the packet using the let’s chat interface.

The Burpsuite interface will look something like the above when we try to inspect the packet from the curl command.

As a result, we managed to see the details when we try to access the API endpoints

There is some id that we can use from rooms endpoints

The response to the messages looks promising

We found some messages stating on “text”

Finally, we managed to obtain one credential



We have tried the credential within the two previous websites, but we retrieve “username or password is incorrect”


On the cachenet website interface, the credentials work and we got a dashboard

I notice the cachenet version is 2.4.0-dev which might be useful to exploit.
Let’s do some research on the internet

Cachet 2.4: Code Execution via Laravel Configuration Injection (sonarsource.com)



We got the username will by entering ${DB_USERNAME}


We got the password by entering ${DB_PASSWORD}

Let’s access the machine via ssh service
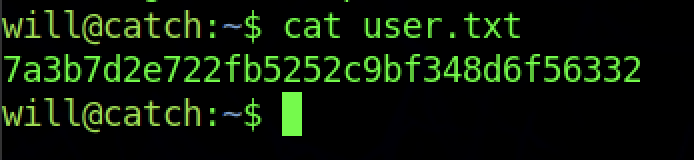
We can read the user flag by slamming the command “cat user.txt“
Escalate to Root Privileges Access

As usual, let’s use common privileges but it says that the user will not run sudo on catch

Let’s execute the pspy64 to see what is running in the background

There is a file such as to verify.sh that has been stored inside /opt/mdm
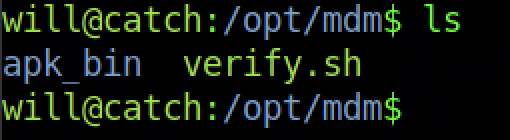
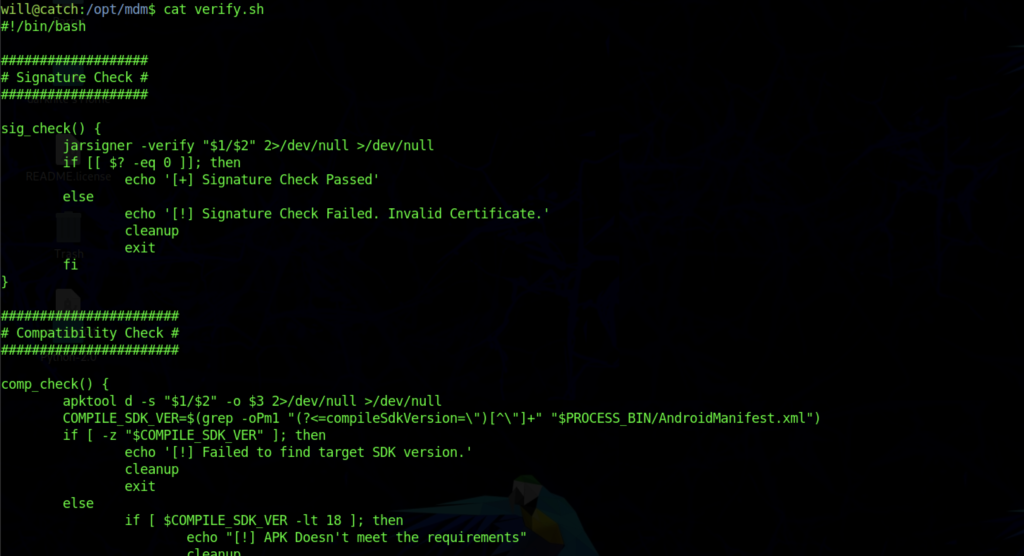

Let’s analyze the source code that we need to put one file an apk file inside /opt/mdm/apk_bin

Let’s throw a reverse shell on the source code

Sadly, the source code cannot be compiled back to apk file format

Let’s change it into a command that give us a SUID binary to us

At last, we can compile the source code

We are required to create a key where we can use keytool for this activity

The key has been created


Let’s sign the apk by using jarsigner

Let’s transfer the file into our victim’s machine
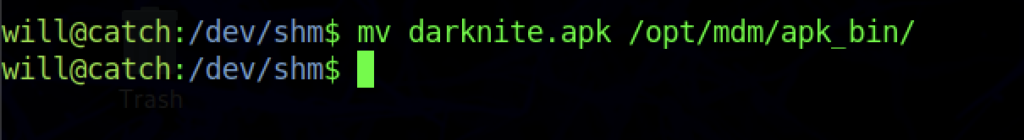
We can move the file into /opt/mdm/apk_bin

As a result, let’s monitor the activity by running pspy64 tool

Finally, the /bin/bash file has changed into SUID Binary
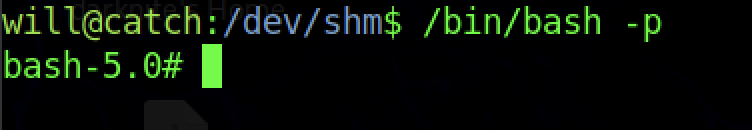
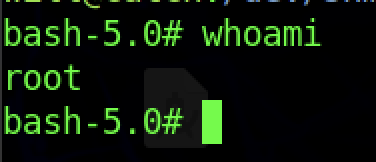
We can read the root flag by running the command “cat /root/root.txt”


No responses yet