Web Application Assessment Information
Firstly, we need to understand why Web Application Assessment is important to any organization out there. As people should be aware by now, Web Applications have played an important and vital role in an organization’s future which is also exposed to cybercriminals attacks.
A pentester will be doing Penetration Testing on the Web Application to find all vulnerabilities while the attacks need one. For Web, Application Assessment will use the testing methodology such as WSTG – Latest | OWASP Foundation
What is Burp Suite?
Burp Suite can be considered as one of the most popular Penetration Testing and Vulnerability Assessment tools that it can use for Web Application Security Assessment. For those who are not familiar with the tools, Burp Suite has normally been used to evaluate any security or vulnerability on the web-based application and the tester will proceed with the hands-on testing.
Burp Suite or also known as Burp can be classified into two categories like Professional and Community. The only difference between those categories is that the Professional version has a more advanced feature available than the Community Version of Burp Suite.
The tool Features:
| Features | Burp Suite Community | Burp Suite Professional |
| Proxy | Allow the tester to intercept and modify requests and responses | Allow the tester to intercept and modify requests and responses |
| Repeater | Allows to capture, modify the packets, and retry sending the request over and over | Allows to capture, modify the packets, and retry sending the request over and over |
| Intruder | Rate-limited from the Professional version | Allow spraying an endpoint with requests which sometimes used on brute-force attacks/fuzz endpoints |
| Decoder | Decoding captured information, or encoding a payload prior and then sending the payload to the target | Decoding captured information, or encoding a payload prior and then sending the payload to the target |
| Comparer | Comparing two pieces of data at either word or byte level | Comparing two pieces of data at either word or byte level |
| Sequencer | Accessing the randomness of tokens such as session cookie values or other random generated data | Accessing the randomness of tokens such as session cookie values or other random generated data |
| Extra Features | The evidence or progress cannot be saved | The evidence or progress can be saved |
The Startup of Burp Suite and Usage
We are required to start the tool for this Web Application Assessment which the step of starting up can be seen below
Disclaimer: I’m using Community Edition of the tools for demonstration

As a result, the first thing that you see after starting Burp Suite would be an interface shown as above so that we can proceed with the tools, you can click the button “Next“

We can click the “Start Burp” Button on the page shown above.

Normally, it will take a few seconds for it to fully start which somehow takes some time depending on your own Operating System

Therefore, the interface is shown above only means that you have properly started Burp Suite

Firstly, we are not touching the configuration unless we need to use different IP, port and use a different client request method on Proxy Tab.


In conclusion, we need to configure our browser while we can interact with the Burp Suite tool


For example, we can capture the curl command via Burp Suite and then send the packet to Repeater
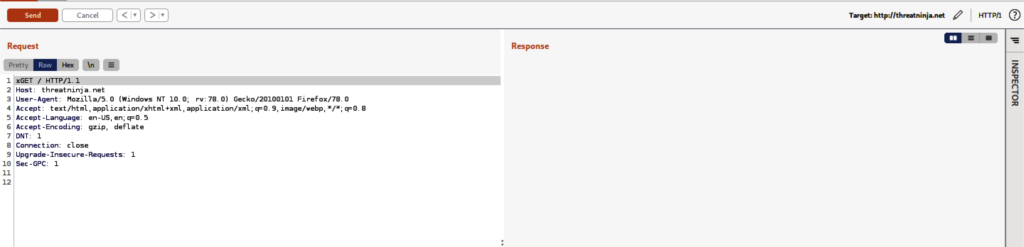
We will obtain the interface as above.
Burp Suite Attacks


Those two pictures above show that we can modify the payload which will be sent to the application. For example, we can change any information or permission to the application where it can be scary sometimes.


Another interesting attack is to play with any agent but we use User-Agentt on the screenshot above. As a result, we can use methods such as zerodiumsystem to obtain a reverse shell on the victim’s machine.

Aside from that, we also can obtain a reverse shell during a Local File Inclusion attack or also known as LFI. On the other hand, LFI is being used to get a good understanding of the directory or file residing inside the machine.

A Pentester also can use a common attack such as SQLi via Burp Suite

The sample of the output is been show above.

No responses yet