In this post, I would like to share a walkthrough of the Iclean Machine from Hack the Box
This room will be considered a Medium machine on Hack the Box

What will you gain from the Iclean machine?
For the user flag, you need to examine a Flask web application and find an XSS vulnerability to capture a session cookie. This cookie is used to bypass the authentication on the /login page and access the /dashboard page. On this page, a Server-Side Template Injection (SSTI) vulnerability is exploited to gain remote code execution. By finding hardcoded credentials in a Python script, hashes are retrieved from a database. Cracking one of these hashes allows for lateral movement to a standard user’s account.
As for the root flag, you need to find a specific binary, which is leveraged to extract the root flag.
Information Gathering on Iclean Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start
─[darknite@parrot]─[~/Documents/htb/iclean]
└──╼ $nmap -sC -sV 10.10.11.12 -oA initial
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-03 08:37 EDT
Nmap scan report for 10.10.11.12 (10.10.11.12)
Host is up (0.060s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 2c:f9:07:77:e3:f1:3a:36:db:f2:3b:94:e3:b7:cf:b2 (ECDSA)
|_ 256 4a:91:9f:f2:74:c0:41:81:52:4d:f1:ff:2d:01:78:6b (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.42 seconds
┌─[darknite@parrot]─[~/Documents/htb/iclean]
└──╼ $
Let’s access the website interface

Nothing interesting that we can abuse on the website interface

However, I found one login page that we can test with a random credentials

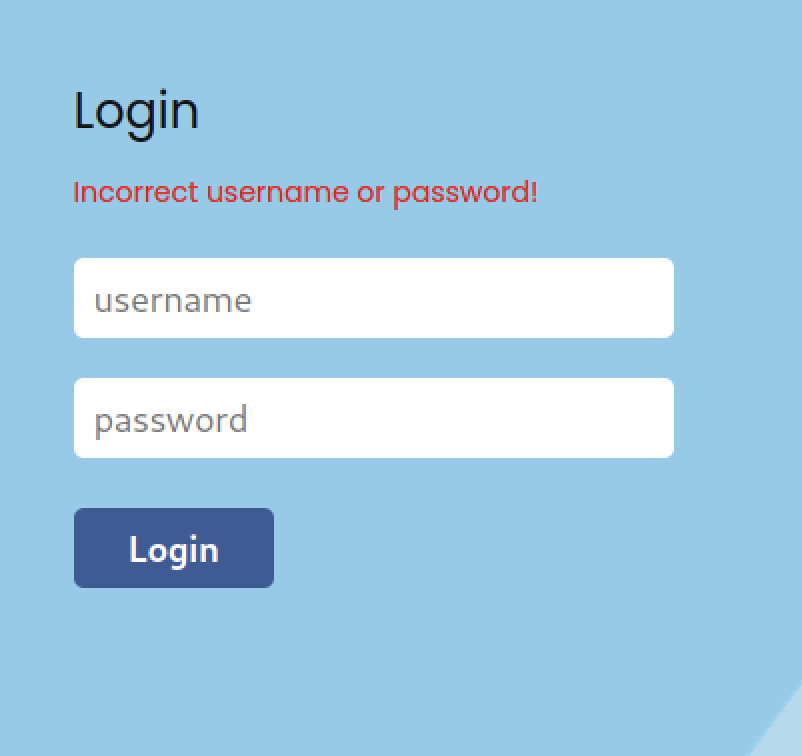
Sadly, the random credentials seem not working at all. At this point, I stuck on the page for a few minutes before deciding to enumerate the directory using the gobsuter

At least, we managed to find some directories that we can investigate further

There is one directory that stands out to my eyes.
Play around the SSTI payload on the website interface

Let’s test the function by entering the information as shown above

It will look something as shown in the screenshot above via Burpsuite

It works like a charm!

Therefore, let’s enter the XSS payload as shown above

We found some cookies we can use in the latter stage.

We can copy-paste the cookie that we found earlier and use it on the cookie’s parameter

Finally, we managed to access the dashboard interface

On the Generate QR section, we managed to see the invoice-id that we can generate

After a while, we were presented with the Invoice ID that had been generated as shown above.

Let’s try to manually generate the invoice as shown above

As usual, we managed to see the Generated of Invoice ID

Let’s enter the ID as the QR as shown in the screenshot above

We are required to enter the QR-LINK to be generated above

Therefore, let’s try to play around SSTI payload


We managed to see that the SSTI payload works

As a result, let’s enter some SSTI payload but sadly we are provided with one error

Let’s enter the SSTI payload that asks for an ID injection

It has worked as I expected

Therefore, let’s start our listener

Let’s call our file on the attacker’s machine

At least, we managed to find out that the command injection works

Therefore, let’s create the reverse shell command on a new file

Let’s inject the command as shown above

Let’s try to inspect the payload via burpsuite and URL encode.

It works but the shell does not look properly at all

Therefore, let’s change to a normal shell using nc

On the victim’s machine, we managed to find the database’s credentials
Enumerate the SQL database

Let’s enumerate the SQL database

There are 3 databases that we look deeper



Finally, we managed two hashes but I will look into the consuela’s hash

We can use crackstation to crack the hashes and we managed to find the password



We can read the user flag by typing the “cat user.txt”
Escalate to Root Privileges Access

As usual, we can find the malicious binary to abuse in the next step. We managed to find qpdf


After a while, we managed to find the directory


We can read the root flag by executing the command above

No responses yet