In this post, I would like to share a walkthrough of the Download Machine from Hack the Box
This room will be considered a Hard machine on Hack the Box

What will you gain from the Download machine?
For the user flag, you will need to abuse the file read vulnerability which allows us to read the site’s source code. There’s an injection that allows me to access the other user’s file on the download file path. As a result, we managed to retrieve a hash where we were required to crack. Once you obtain the password, you can access the machine via SSH service.
As for the root flag, you need to identify the crontab for the root which we can insert some command to the Postgres user to execute the database queries. We can execute to root by exploiting the TTY pushback
Information Gathering on Download Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start the information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN
┌─[darknite@parrot]─[~/Documents/htb/Download]
└──╼ $ nmap -sV -sC 10.10.11.226 -oA intial
# Nmap 7.93 scan initiated Tue Aug 8 05:27:35 2023 as: nmap -sV -sC -oA intial 10.10.11.226
Nmap scan report for 10.10.11.226
Host is up (0.16s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 ccf16346e67a0ab8ac83be290fd63f09 (RSA)
| 256 2c99b4b1977a8b866d37c913619fbcff (ECDSA)
|_ 256 e6ff779412407b06a2977ade14945bae (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://download.htb
|_http-server-header: nginx/1.18.0 (Ubuntu)
1062/tcp filtered veracity
1216/tcp filtered etebac5
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Aug 8 05:28:34 2023 -- 1 IP address (1 host up) scanned in 59.70 seconds
┌─[darknite@parrot]─[~/Documents/htb/Download]
└──╼ $
Let’s access the website interface

The website interface looks something like shown above which upload and login is the only function available.
Enumerating the website using burpsuite

We are also aware that the website is been powered with Express framework.




We can register a new account on the website interface.

Therefore, let’s see what the upload function looks like



The packet will look something shown above.

From the cookie value, it shows that the authentication is a success

Let’s inspect the download file on the burpsuite

The response to the command injection which leads to 400 bad requests
Found a file for further analysis on the download machine


However, we should be able to read the file after we encode the bad character.
Exploiting using the cookie-monster


Firstly, we are required to download the script onto our attacker’s machine

We should be getting those two files as shown in the screenshot above.

Let’s ensure that the script works by running it as plain as possible

Let’s create a JSON file that contains details as above where the only difference is the username. The details can be similar to the cookie value that has been decoded back as plain text while the username Wesley is taken from package.json file

As a result, we are provided with a new cookie value for both data and signature cookies.

Therefore, let’s change the current cookie with the cookie that we created using cookie-monster
Access the dashboard as Wesley

Boom! We have successfully accessed the dashboard as Wesley

There are a few pdf files but let’s download the AnnualReport2022.pdf into our attacker’s machine

Nothing that looks interesting inside the pdf file
Obtaining the access to machine via SSH service


We should obtain the hash after we execute the Python script.

At last, we managed to retrieve the password for Wesley using John the Ripper


We should be able to get the password using Hashcat

Finally, we managed to access the machine via SSH service

We should be able to read the user flag by typing the “cat user.txt” command
Escalate to Root Privileges Access

As usual, we can verify any SUID binary that we can abuse but sadly we cannot find any useful SUID binary.

As a result, we should be enumerated by using the pspy64 script




After a while, i noticed that Postgres was running on the machine. I would be assuming that the database is using the Postgres database.
Postgres enumeration on the download machine

Let’s find the filename that contains the downoload-site.service on the machine

Oh wow! We managed to see the possible password for the Postgres database.

As we expected, we have successfully accessed the database that was configured inside the machine.

We should be able to add or modify any function on the database.
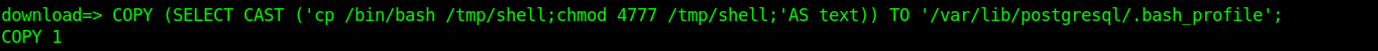
We can try to copy the bash file on the /tmp/ directory which can lead to escalation to Postgres users.


After a few minutes, we managed to see the process had been executed for the Postgres and download-site
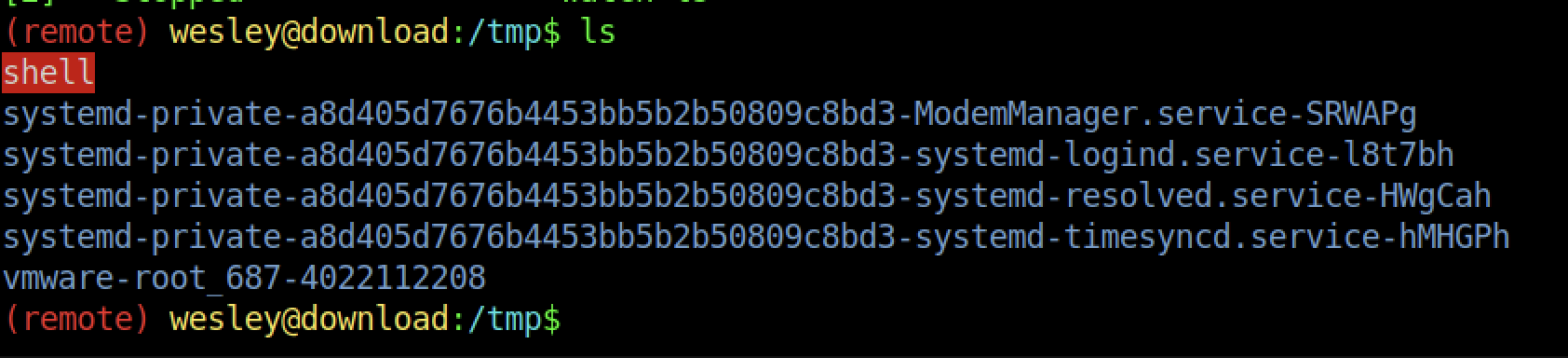
At last, the file is been created on the /tmp/ directory


We can escalate to Postgres user access.
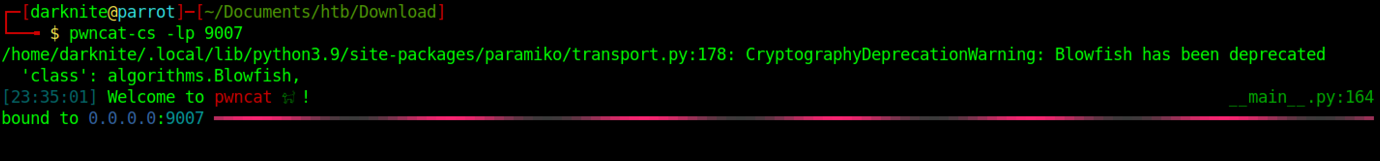
Let’s start our nc listener on our attacker’s machine.

We should test by inserting the bash shell connection into the Postgres database which might work

Finally, we have managed to obtain the shell on Postgres shell

Sadly, the shell is not stable at the moment.

After a long thinking on how to create the exploit, i managed to create one exploit script based on my research on the internet.

Let’s compile the c program file into the executable file


We should be transferring the file into our victim’s machine.

As usual, we should be starting our nc listener on our attacker’s machine

By executing the command above, we should be able to retrieve the reverse shell connection back to us.

Uwu! We have a Root Reverse Shell Connection back to us.

We can read the root flag by typing the “cat root.txt” command

By changing the reverse shell command on the script, we can modify it with the “chmod u+s /bin/bash” command

After a while, the bash file is assigned to the SUID binary

We also can obtain root by using this method
Extra Information


No responses yet