In this post, I would like to share some walkthroughs on the Sherlock Challenges such as Nubilum-1 which can be considered a Medium Difficulty which can be found here
- Introduction to Nubilum-1 Challenge
- Case Study of Nubilum-1
- 1. Which AWS IAM account was compromised by the TA?
- 2. Where did the attacker locate the hard-coded IAM credentials?
- 3. In total how many EC2 hosts were deployed by the TA?
- 4. What is the name of the key pair/s generated by the attacker?
- 5. What time were the key pair/s generated by the attacker?
- 6. What are the key pair ID/s of the key/s generated by the attacker?
- 7. What is the description of the security group created by the attacker?
- 8. At what time did the Sys Admin terminate the first set of EC2s deployed?
- 9. Can we confirm the IP addresses used by the TA to abuse the leaked credentials? (Ascending Order)
- 10. In addition to the CloudTrail data and S3 access we have provided artefacts from the endpoint reported by AWS. What is the name of the malicious application installed on the EC2 instance?
- 11. Please can you provide the hostname and username details of any victims of the C2 server?
Introduction to Nubilum-1 Challenge
In this challenge, the cloud administration team is alerted to potential malicious activity occurring within their Amazon EC2 instances. Unrecognised deployments were discovered by the system administrator, posing a serious threat to the company’s reputation. The lack of preemptive security measures exacerbates the situation, including the unrestricted global access to the critical S3 bucket. The incident responder emphasises the urgency of investigating the misuse of their infrastructure, urging the necessity for immediate collaboration to collect CloudTrail data and initiate a Phase 1 UNIX collection on the implicated EC2 instance. The situation outlines a critical security lapse demanding swift action to protect the company’s reputation.
Case Study of Nubilum-1
Our cloud administration team recently received a warning from Amazon that an EC2 instance deployed in our cloud environment is being utilised for malicious purposes. Our sysadmin team have no recollection of deploying this EC2, however do recall logging onto the AWS console and finding in excess of 6 EC2s running, which he did not recall deploying. You have been provided with the interview with our Cloud sysadmin within the triage.Let’s start analyzing the Nubilum-1 challenge

The screenshot above shows the extraction of the zip file after downloading the zip file from the website

Therefore, let’s read the interview between the Incident Responder and the Cloud System Administrator

Let’s extract the tar.gz file on our machine to investigate further

We are also required to unzip the unusual-directory which there are a lot of directories in which the password is the same as found in the Hack The box page

We managed to see a few files within the money directory
1. Which AWS IAM account was compromised by the TA?

After analysing the whole file within the CloudTrail, let’s go through carefully one file like shown above

I noticed there’s a username called forela-ec2-automation
2. Where did the attacker locate the hard-coded IAM credentials?

On the forela-storage, there’s a backups directory which a python file is stored inside.

I notice there’s an access_key and secret_key mention within the ec2.py file
3. In total how many EC2 hosts were deployed by the TA?
13
4. What is the name of the key pair/s generated by the attacker?

Let’s analyze every file within the forela-storage. I found a few files in which the content caught my attention


We managed to notice the 1337.key and 13337 on the keyname details
5. What time were the key pair/s generated by the attacker?

The time at which the key pair have been generated can be found on the file shown above
6. What are the key pair ID/s of the key/s generated by the attacker?

I also found the KeyPairID within one of the files
7. What is the description of the security group created by the attacker?
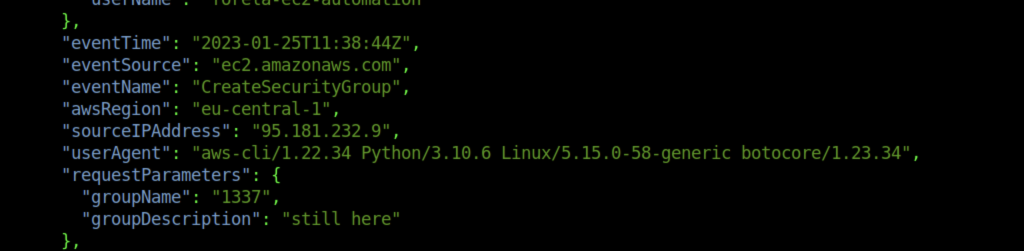
On the note, we have found the Group description which said “still here”
8. At what time did the Sys Admin terminate the first set of EC2s deployed?

When analyzing each file, I also noticed there is another time that might be showing the activity as requested in the question
9. Can we confirm the IP addresses used by the TA to abuse the leaked credentials? (Ascending Order)
95.181.232.4,95.181.232.8,95.181.232.9,95.181.232.28
10. In addition to the CloudTrail data and S3 access we have provided artefacts from the endpoint reported by AWS. What is the name of the malicious application installed on the EC2 instance?

When we try to extract the unusual-directory, there is one directory that stands such as poshc211.
11. Please can you provide the hostname and username details of any victims of the C2 server?

Let’s see the poshc2.server.log and maybe we can find the answer to this quest

The output starts showing the information as shown above.

Finally, we have found the answer to this question such as DESKTOP-R4KM0GJ\Marcus Athony

No responses yet