What is Varnish’s HTTP cache?
To be honest, it’s my debut of hearing about the Varnish HTTP cache and my first time exploiting it. As a result, let’s try to learn it together where my thought might be different from others.
Varnish HTTP Cache is a high-level web application accelerator or also called caching HTTP reverse proxy. It is also a powerful and open-source HTTP engine proxy that the web application can speed up to 1000 percent by applying to cache/storing an exact copy of the website interface when the users or visitors access the website for the first time.
vcl 4.0;
backend default {
.host = "127.0.0.1";
.port = "8080";
}
sub vcl_recv {
if (req.url ~ "/static") {
return (hash);
}
}
sub vcl_backend_response {
if (bereq.url ~ "/static") {
set beresp.http.cache-control = "public, max-age=240";
set beresp.ttl = 1d;
return (deliver);
}
}
sub vcl_deliver {
}
Those who want to learn more about the Varnish HTTP Cache can access the resource here
Demonstration of the Varnish HTTP cache vulnerabilities
A demonstration of the attack is taken from the forget machine walkthrough which can be found here

Finally, we managed to access the Dashboard as shown above.
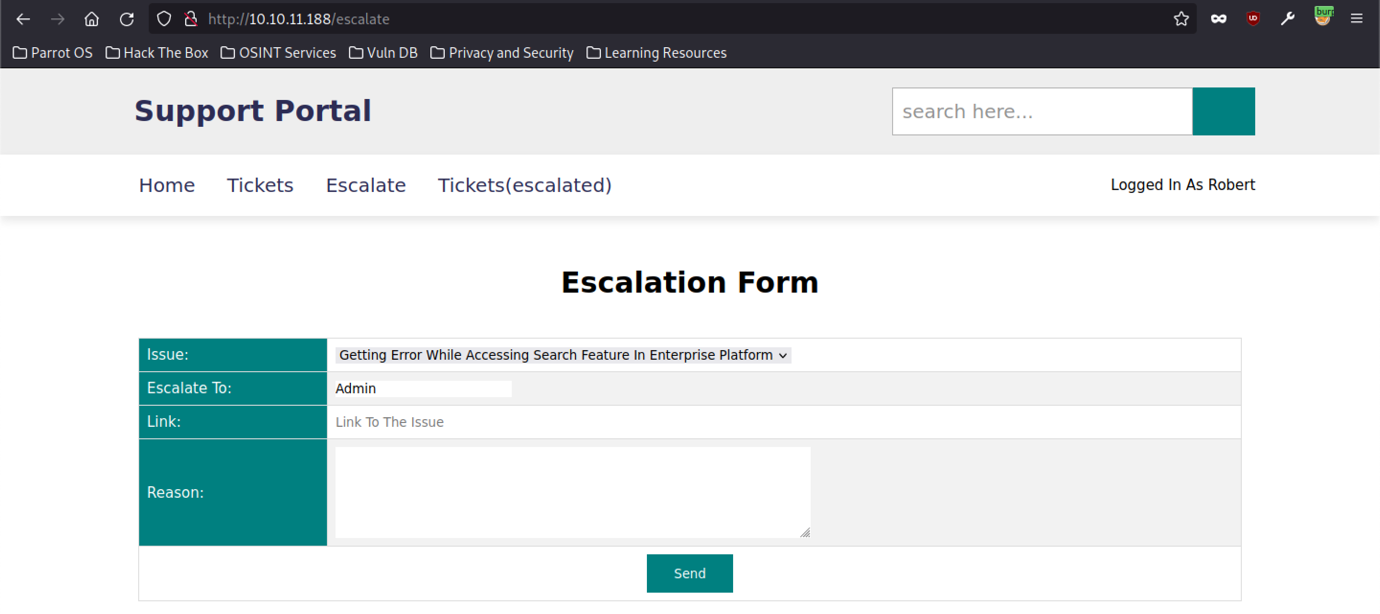
As a result, let’s roam the Dashboard and managed to find an Escalation Form as shown in the screenshot above.

There are a few tickets that have been raised and I notice one ticket stands out too much such as “SSH Credentials are Not Working for Jenkins Slave Machine“
Exploiting the cache on escalate form
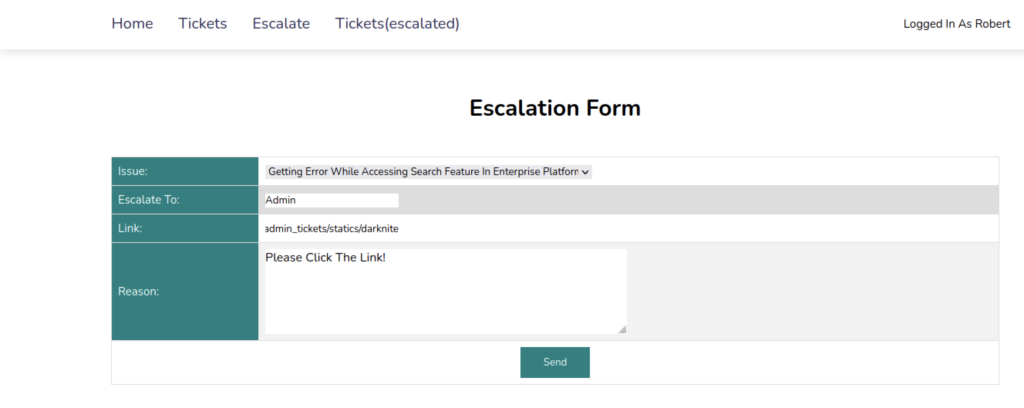
We can read the admin tickets by injecting the cache page on the Escalation form which should leak the tickets information
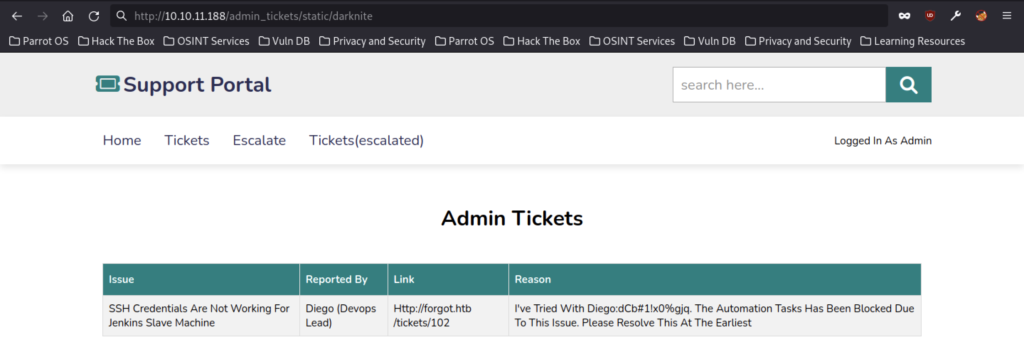
At last, we manage to obtain a password for Diego which I assume it’s the credentials for SSH service.
No responses yet