In this post, I would like to share my experience on how to detect some vulnerabilities within the application itself. A lot of people did ask me how I manage to detect any vulnerabilities with no information (blindly) at all while playing the CTF game.
There are a lot of ways to detect vulnerabilities within the application such as the application’s version which can tell the threat actors about the application that has been installed within the server.
For the demonstration in this post, I will share some well-known attacks such as SQL Injection and Local File Inclusion
First vulnerability: SQL Injection on the application
Normally, we will test whenever the login page appears on the web application itself. The demonstration comes from here

Let’s open our burpsuite tool to analyze the packet.

Let’s inspect the packet

I try to use an error SQL Injection on the website but didn’t see anything at all.

Therefore, let’s try using a very common SQL Injection and it was a success.

As a result, let’s enumerate the SQL Injection using union based

On the website interface, we got the message “Welcome 4” and it was successful.

The screenshot above shows 4’s profile.

We should be able to enumerate the SQL Database deeper by using the syntax ‘ union select 1,2,3,database()– –

It was a success and it show the main
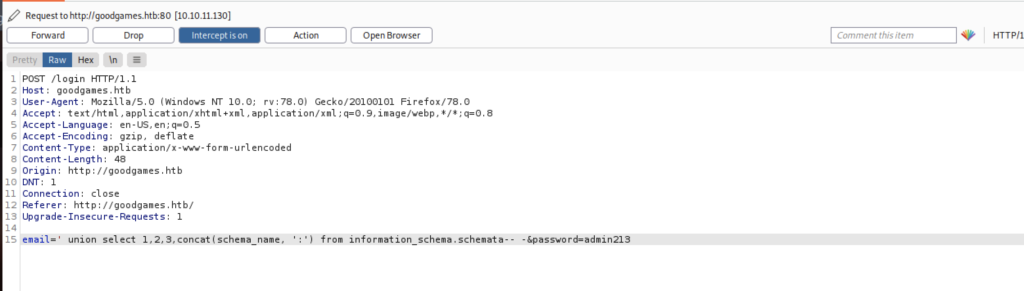
Next, we can use the syntax ‘ union select 1,2,3,concat(schema_name, ‘:’) from information_schema.schemata– –

It is also successful and it shows information_schema:main:
Second Vulnerabilities: Local File Inclusion (LFI) attack
The vulnerability comes from here

On the website interface, nothing much that we can take advantage but I did notice that the Website’s URL is vulnerable to Local File Inclusion
Therefore, let’s test our theories on the website.

Sadly, we got a blank page when trying to execute the LFI attack but it works pretty well with BurpSuite.
No responses yet